In-app purchasing exploit discovered for OS X apps
Discovered and implemented by the same Russian hacker who crafted the iOS in-app purchasing workaround, the so-called "In-Appstore for OS X" uses a similar receipt-spoofing method to bypass Apple's validation system to get paid content for free, reports The Next Web.
Alexey Borodin's newest exploit uses the same DNS server routing and receipt spoofing method outlined in previous reports to fool apps into validating dubious in-app purchases.
The system requires a user to install local certificates on their Mac and route purchases to a specially-created DNS server hosted by Borodin. The server, set up to be a replica of the Mac App Store, then sends back a spoofed receipt verification.
Screenshot of Borodin's "In-Appstore for OS X" exploit in action. | Source: The Next Web
According to Borodin some over 8.46 million transactions have been made with his spoofing method, though it is not clear if that number includes the new system targeting OS X. Apple has the option to push out a fix through Software Update and the Mac maker is on the verge of releasing its new OS X Mountain Lion with a host of security protocols including the Gatekeeper security system later in July.
On the same day of the OS X app hack's release, Apple sent out emails inviting iOS app developers to use the company's new protected receipt validation system to thwart last week's in-app purchasing exploit ahead of permanent solution expected in iOS 6.
 Mikey Campbell
Mikey Campbell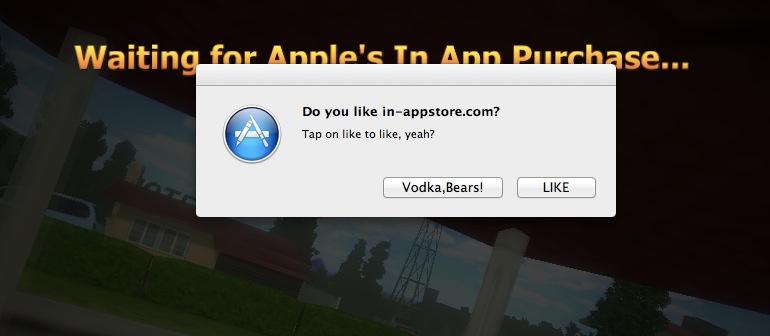









 Marko Zivkovic
Marko Zivkovic
 Amber Neely
Amber Neely
 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen
 Mike Wuerthele and Malcolm Owen
Mike Wuerthele and Malcolm Owen

 William Gallagher
William Gallagher








