SF DA initially pleased in antitheft testing of Apple's iOS 7 Activation Lock, Samsung's LoJack
San Francisco's District Attorney George Gascón described the smartphone theft deterrent systems demonstrated by Apple and Samsung as "clear improvements" in the City's efforts to thwart crime.
Last week, Gascón and New York's Attorney General Eric Schneiderman announced efforts to test the two company's new security technologies to "see if they stand up to the tactics commonly employed by thieves" in an program that partnered with experts from the Northern California Regional Intelligence Center.
In a followup report by the San Francisco Examiner, Gascón said he was "very optimistic that they came and were willing to share their technology with us."
He also noted that neither Microsoft's Windows Phone nor Google's Android had similar technology to demonstrate for their own mobile platforms.
Stealing smartphones is a big business, with the US Federal Communications Commission stating that one third of robberies nationally involve a cellphone. In tech savvy San Francisco, the figure is closer to half of all robberies.
Gascón declined to detail how the technologies used by Apple and Samsung work, stating that they are not yet finalized. Apple's "Activation Lock" feature remains under NDA as part of iOS 7, while Samsung has contracted with a third party for a security subscription service.
Apple the first OS vendor to announce platform theft security
Apple's new Activation Lock was however demonstrated this summer at the company's Worldwide Developer Conference.
The new feature involves embedding the users' iCloud account into the device's low level firmware, so that even if thieves attempt to wipe the device, it will refuse to subsequently "activate" until the account and password are entered.
iOS "activation" involves the device contacting Apple's servers, an additional step that the company can tie to a specific iCloud account and device's UUID. Apple can therefore refuse to activate a device that has been reported as stolen until both authentication factors (the device and the account) are supplied.
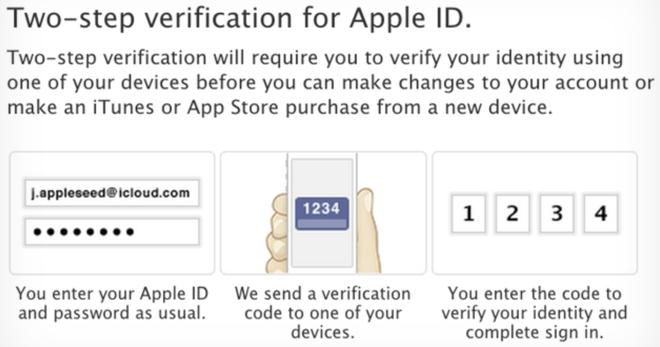
Apple has recently added new layers of security to iTunes and iCloud to support two factor authentication (Apple calls it "two step verification").
This means that a user can configure their account require access to both a verified hardware device and their account credentials password, preventing a remote third party from simply guessing at their credentials or using an illicitly acquired username and password by itself.
Apple is also using this same heightened security to support secure, encrypted sync of users' passwords and credit card numbers via iCloud Keychain in iOS 7 and OS X Mavericks, and will use this security apparatus to secure iOS 7 Activation via iCloud.
Apple's existing "Find My iPhone" feature already allows users to track stolen devices or remotely wipe a device after it is stolen, but it is currently easy for a thief to take a stolen device off the network and erase it to "factory new" condition, allowing for easy resale because iOS 6 doesn't yet tie activation into the users' iCloud account.
Stitching "Find My iPhone" into the low level firmware in iOS 7 means that a thief would at least need to crack the device's security via a jailbreak, a practice Apple actively seeks to make impossible (even as hobbyist crackers work to find security exploits to defeat this, enabling root access and making it possible to pirate stolen third party apps).
It appears that Apple's additional activation steps would also require phone thieves to spoof the device's hardware UUID and install new, modified firmware omitting support the Activation Lock feature, both non-trivial tasks.
Until the feature is released and tested by security experts, it's hard to say how difficult it will be for determined thieves to defeat it. It will, however, provide significant new hurdles for criminals to jump.
iOS 7 users can remove Activation Lock and resell their device; the new buyers will be able to use Activation Lock to tie the device to their own iCloud accounts. However, if a user locked and then forgot their account password, they may be unable to reactivate the device until their account credentials are reset.
Samsung selling an app with firmware ties
Without anything similar provided by Google for Android, Samsung has partnered with third party developer Absolute Software to deliver a "LoJack" branded solution, at least for one model of its smartphone lineup: the Galaxy S4.
Samsung's security app solution is conceptually similar to its use of third party Knox software to shore up Android's missing enterprise security features on certain new Galaxy phones.
Tied into the phone's firmware by Samsung, the LoJack app says it can allow users to remotely lock, wipe and locate a missing device similar to iCloud's Find My Phone, but also says it will "work with law enforcement globally to get the device back."
The service is supplied with a $29.99 annual fee, whereas Apple's iCloud and Find My Phone are free to iOS users.
While Absolute says its LoJack app "cannot be removed by a factory reset once the app is installed by the user and activated," thieves are likely to be savvy enough to go beyond a "factory reset" and perform a ROM flash of the firmware itself after rooting the device, as noted by Android Police
The "openness" of the Android platform in general makes it harder to secure such a firmware-level solution, because Google itself does not oppose rooting and reinstalling an Android system's firmware with new code missing the necessary security app support.
Samsung and other Android licensees often do take efforts to make it more difficult to root some of their devices, just as Apple does, both to secure their software and their business model.
However, removing security elements from Android's core firmware is also much easier than with iOS because the underlying Android software is open source and can be compared against the core Android firmware that lacks such security.
 Daniel Eran Dilger
Daniel Eran Dilger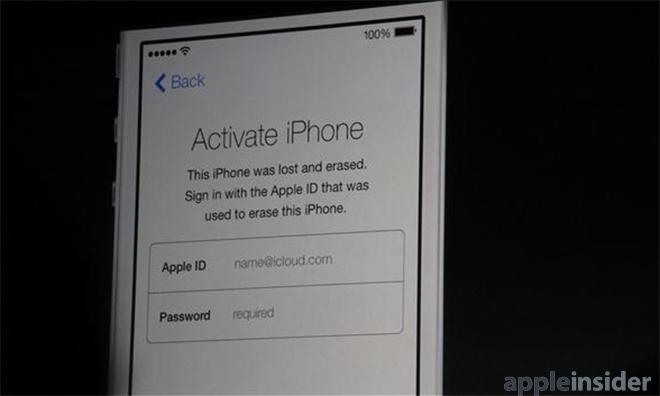












 Christine McKee
Christine McKee
 William Gallagher
William Gallagher
 Andrew Orr
Andrew Orr
 Sponsored Content
Sponsored Content
 Malcolm Owen
Malcolm Owen