Apple's bug bounty program hindered by low payouts, report says
Apple's invite-only bug bounty program is off to a slow start as security researchers in search of high payouts are saving discovered exploits for high-price sales on the gray market.
In a series of interviews conducted by Motherboard, researchers invited to participate in Apple's initiative said iOS bugs are too valuable to report.
Notably, participants are reluctant to report discovered system flaws because the bugs are either worth more on the gray market or they prohibit work on other areas of the operating system. So far, researchers invited to the program have yet to publicly claim a single bounty.
"People can get more cash if they sell their bugs to others," said Nikias Bassen, a security researcher at Zimperium who joined Apple's program last year. "If you're just doing it for the money, you're not going to give [bugs] to Apple directly."
Of the ten researchers Motherboard interviewed, none had filed a report with Apple.
Announced at a Black Hat conference in 2016, Apple's bug bounty program was created to uncover zero-day flaws in hopes of shoring up defenses of high-level computing assets and first-party security elements. Maximum payments top out at $200,000 for exploits related to secure boot firmware components and quickly drop off to $100,000 for the extraction of confidential material protected by the Secure Enclave Processor. Lower payouts include $50,000 for execution of arbitrary code with kernel privileges, $50,000 for unauthorized access to iCloud account data on Apple servers and $25,000 for access from a sandboxed process to user data outside of that sandbox.
Private companies like Zerodium pay upward of $1.5 million for a full set of bugs that can jailbreak an iPhone, the report said. Other firms will accept iOS exploits for $500,000, depending on their intrinsic value. These companies claim to operate within legal borders, and peddle the discovered zero-day exploits to corporations looking to protect their networks or law enforcement and intelligence agencies.
Hackers might also be leery of reporting bugs to Apple as doing so would jeopardize their own research. Because iOS is so well protected, it takes multiple bugs to access other flaws hidden deep within the operating system. Presenting a bug to Apple ensures the flaw will be patched, thus limiting a potential avenue of access for researchers.
Security researchers invited to attend a bug bounty brief last year asked Apple for special iPhones, or "developer devices," that lack certain restrictions normally present on public models, the report said. These devices would allow hackers to report bugs while continuing investigation into the deep recesses of iOS. Apple declined to provide such devices.
 Mikey Campbell
Mikey Campbell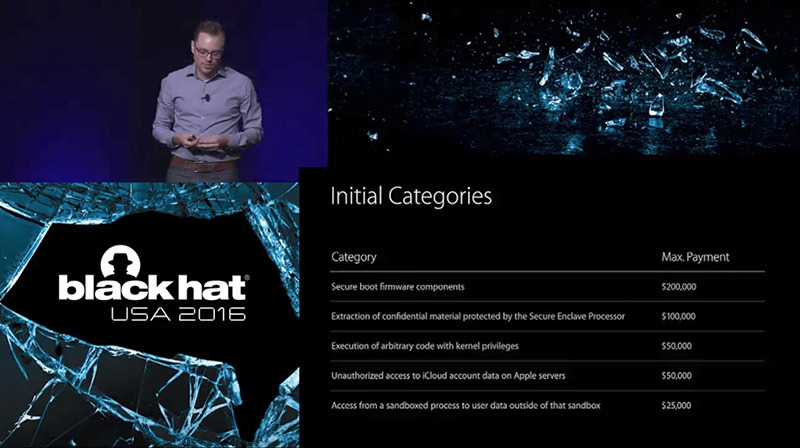











 Malcolm Owen
Malcolm Owen
 William Gallagher and Mike Wuerthele
William Gallagher and Mike Wuerthele
 Christine McKee
Christine McKee
 William Gallagher
William Gallagher
 Marko Zivkovic
Marko Zivkovic