Small $500 device shown to brute force hack iPhone 7 lock screen passcodes, but could take days to work [u]
A unique new exploit is said to take advantage of just Apple's iPhone 7 and iPhone 7 Plus running recent firmware, utilizing a small device to brute force hack and bypass the iOS lock screen passcode of up to three handsets at a time.
The hack was demonstrated on video by YouTuber "EverythingApplePro," who noted that the exploit does not work on older devices like an iPhone 6s or iPhone SE. In addition, it's specific to iOS 10.3.3 or the latest iOS 11 beta.
The hardware is sandwiched between two panes of glass, and features three full-size USB ports to attempt to crack three iPhone 7 units at a time. It also has a micro USB port and even an Apple Lightning port that can be used to power the hardware.
As for how it works, the hack apparently takes advantage of the update process in iOS.
"They found a loophole in the data recovery state that allows you to use as many passcode attempts as you want," the YouTube creator explained.
If the iPhone 7 is running an earlier version of iOS 10, it must be updated to iOS 10.3.3 for the hack to work. And if the device is running the latest firmware, an update to iOS 11 beta will also do the trick.
Interestingly, a download from iOS 11 beta to iOS 10.3.3 is also a suitable way for the crack to work, meaning virtually any iPhone 7 would be vulnerable — if, of course, a hacker were to get their hands on the phone, and also have the $500 device.
While such updates or software downgrades usually require the user to unlock their iPhone, another hack is utilized to get around that requirement.
In the video, "EverthingApplePro" shows a process that involves connecting the iPhone 7 to a MacBook Pro running Windows. The iPhone is placed in DFU mode and an app called 3uTools is used to force the handset to update without a passcode.
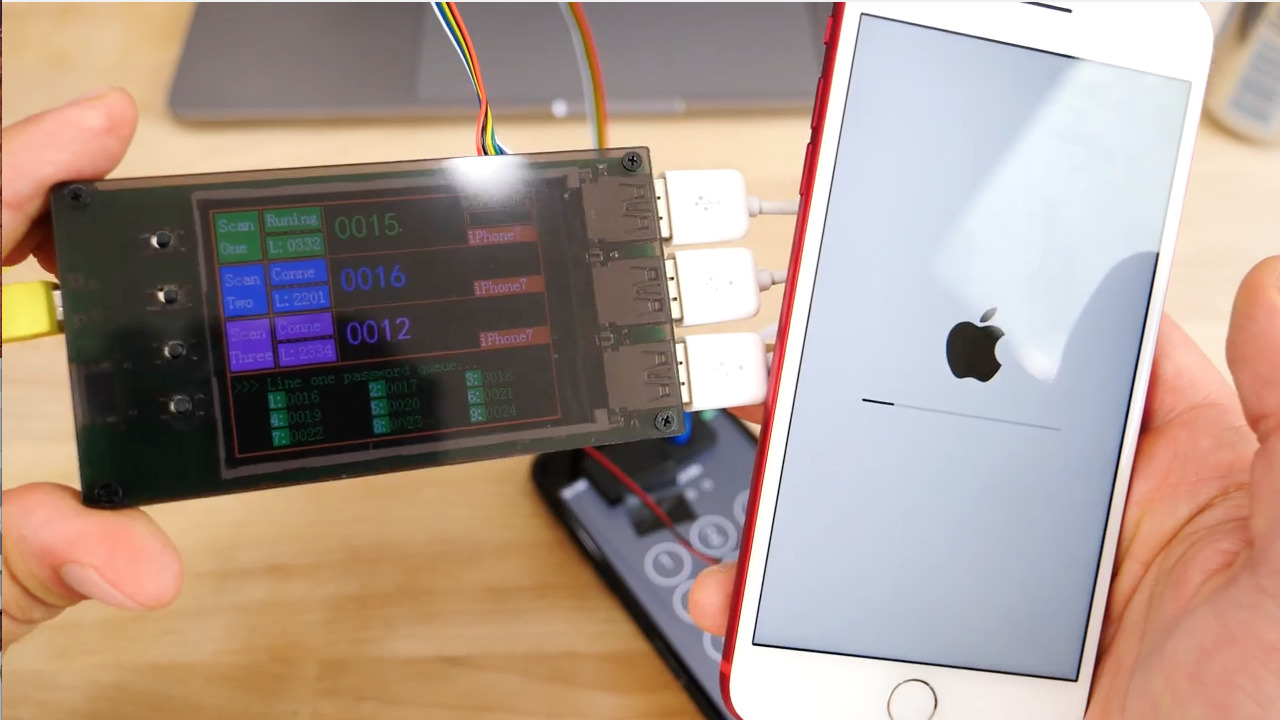
The $500 box takes advantage of the white "press home to recover" screen that is displayed after a new iOS install. Once users are at this screen, they can begin the brute force hack.
The hardware even includes an array of light sensors that ensure the iPhone display stays turned on while the hack is in progress.
That's important, because the hack itself could take days, depending on the complexity of the passcode. For the purposes of the video, a simple passcode of "0016" was used to allow the brute force hack to work more quickly.
At first the device attempts a new passcode every 50 or so seconds, but that gradually ramps up to every 10 seconds. Still, with the sheer number of passcode possibilities (which are even greater if the user has a six-digit or alphanumeric passcode), it would take a number of days to crack an iPhone.
Given Apple's focus on security for its devices, it's likely that this exploit will be patched relatively soon. And considering the investment required, and the fact that the hardware must be in hand for the hack to work, and that it's limited to the iPhone 7 and iPhone 7 Plus, the exploit is unlikely to ever affect the vast majority of iPhone users.
iPhone hacks are rare, but they do happen. This latest hack is particularly noteworthy because it only applies to Apple's latest hardware.
Earlier this week, separate efforts managed to crack the secure encryption key for Apple's iPhone 5s. Twitter user "xerub" released an extraction tool for the device's Secure Enclave firmware — though there are not currently any known exploits utilizing the tool.
Even before Apple began utilizing a secure hardware enclave with Touch ID in the iPhone, its security measures have stifled law enforcement and hackers alike. Last year, following the San Bernardino terrorist attack, the U.S. Federal Bureau of Investigation allegedly paid $900,000 to an Israeli security firm to have them crack an iPhone 5c, because the FBI could not do it themselves.
Update: Apple confirmed to TechCrunch that the discovered loophole will be patched in the final version of iOS 11. Further, the behavior is already fixed in the latest iOS 11 beta 4.
 Neil Hughes
Neil Hughes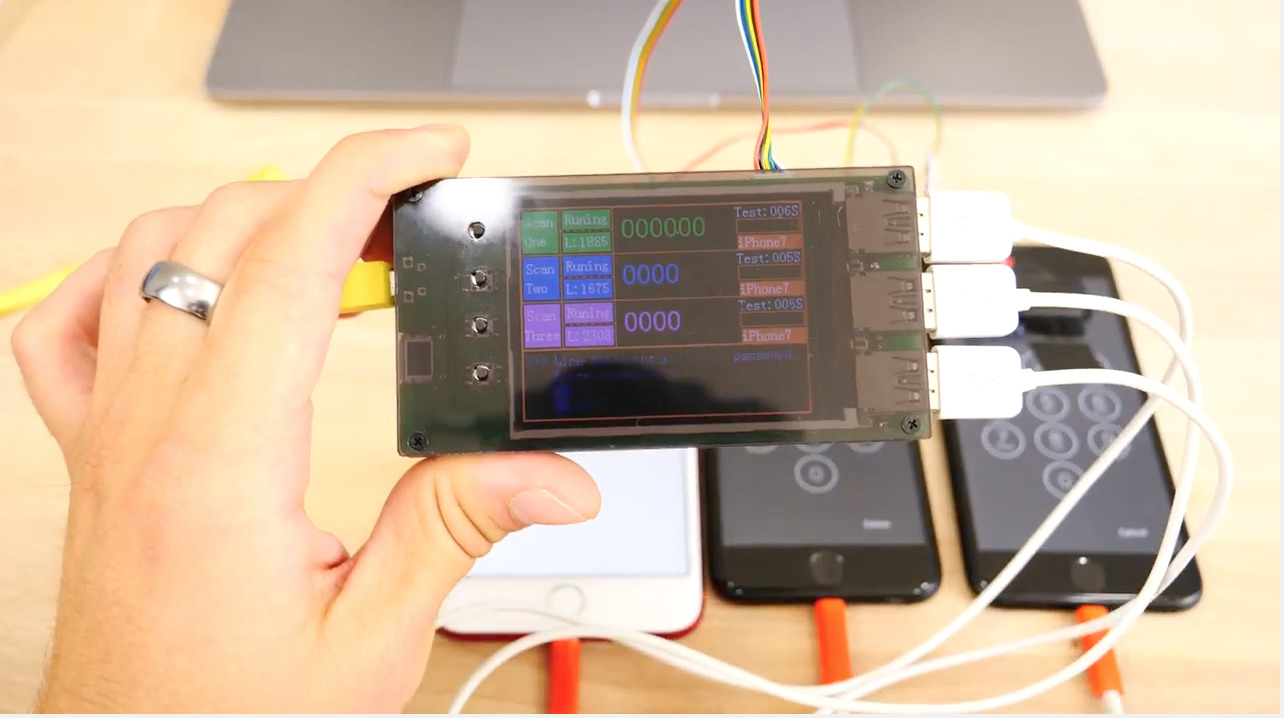









 Marko Zivkovic
Marko Zivkovic
 Amber Neely
Amber Neely
 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen
 Mike Wuerthele and Malcolm Owen
Mike Wuerthele and Malcolm Owen

 William Gallagher
William Gallagher








