NSO Group employee allegedly stole, attempted to sell 'Pegasus' iOS malware for $50M
A disgruntled employee at NSO Group, an organization that creates tools to exploit iPhones and other mobile devices, allegedly stole the firm's infamous "Pegasus" code and tried to sell it to unauthorized buyers for upwards of $50 million in cryptocurrency.
Located in Israel, NSO markets highly effective malware solutions to governments and law enforcement agencies looking to gain access to smartphones. One of the firm's spyware products, known as "Pegasus," was allegedly stolen earlier this year by an employee, Motherboard reports.
Citing an indictment, reports from Israeli news media outlets claim the unnamed person started work at NSO as a senior programmer in 2017, a position that granted access to highly sensitive, potentially dangerous code. Facing possible termination, the employee downloaded a copy of NSO source code worth "hundreds of millions of [US] dollars."
NSO has security protocols in place that prevent employees from using external storage devices, but the apparently disgruntled employee searched online — namely Google — for ways to disable those security features and save the data cache that included Pegasus, the indictment reads. His search history also revealed queries regarding how and where to sell cyber secrets, and who might be a good buyer.
The cache was peddled on the dark net for around $50 million in crypto before a possible buyer engaged. Instead of following through on the deal, the potential buyer alerted NSO of the theft, who in turn worked with law enforcement to identify the thief. The employee's apartment was raided a few days later.
Publication of the indictment was delayed due to concerns over national security, the report said.
Pegasus made waves a couple years ago before being patched in iOS 9.3.5. Using it, attackers could gain access to an iPhone and steal a nearly endless amount of data.
After clicking a seemingly innocuous link received through a message, the target device would be jailbroken, and malware would be loaded to monitor and steal data. Pegasus allowed attackers to access passwords, messages, calls, emails, and logs from apps including Gmail, Facebook, Skype, WhatsApp, Viber, FaceTime, Calendar, Line, Mail.Ru, WeChat, SS, Tango, and more.
After being patched on iOS, Apple soon after issued a patch for Safari on macOS 10.11. El Capitan to address the vulnerability. The assault package on iOS was able to leverage the same zero-day vulnerability to take over a Mac with a single click.
 Andrew O'Hara
Andrew O'Hara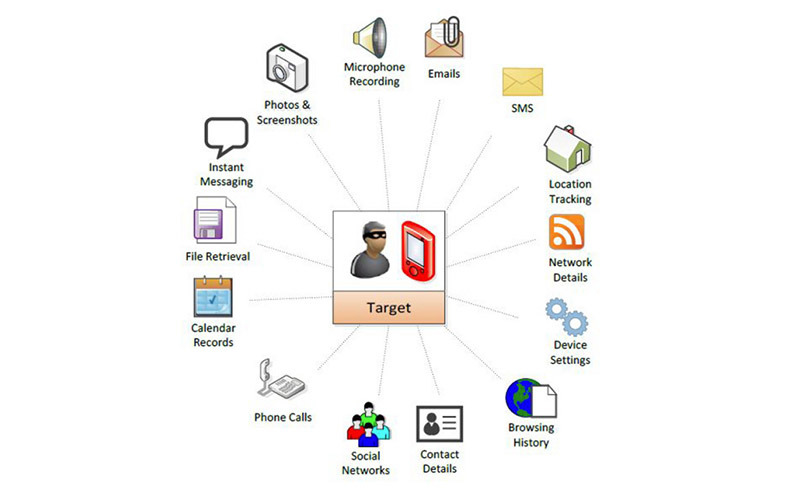









 Malcolm Owen
Malcolm Owen


 William Gallagher
William Gallagher

 Christine McKee
Christine McKee
 David Schloss
David Schloss
 Amber Neely
Amber Neely







