iOS 12.1 Group FaceTime bug allows viewing of a locked iPhone's contact details
A bug has been discovered in the way iOS 12.1 handles Group FaceTime calls, one which can allow a hacker to access the details of a contact stored on an iPhone, without needing to unlock the smartphone at all.
The public release of iOS 12.1 allowed iPhone and iPad users to make Group FaceTime calls, which extends the existing FaceTime functionality to allow up to 32 callers to take part in a video conference. While the change increases the caller limit from two, the mechanism to add contacts also appears to be susceptible to abuse, including when the iPhone itself is locked.
Security researcher Jose Rodriguez discovered the issue, reports The Hacker News, which leverages a number of elements in iOS that Apple permits to be used without unlocking the iPhone.
In the video demonstration, the iPhone being attacked is called by a different iPhone, and the call answered. Once connected, Rodriguez transitions the call to a FaceTime video call, then in the bottom right menu selects "Add Person."
By tapping the plus icon, it brings up the device's contact list as part of the process to add a new user. Rather than adding, using 3D Touch on each contact can bring up more details, including email addresses, phone numbers, and other information.
The attack itself will work on all iPhones running iOS 12.1, including the iPhone XS and iPhone XS Max, but seemingly not the iPhone XR. AppleInsider attempted to perform the same test on an iPhone XR, but while the contact list can be brought up while locked, the lack of 3D Touch means the extra contact data is unavailable.
Rodriguez has previously discovered other ways to access contacts and other data from a locked iPhone, with methods revealed in September and October featuring the VoiceOver screen reader feature and, in one case, the Notes app. The latest discovery is a far simpler process and doesn't require VoiceOver to be active, making it usable on a far wider array of devices.
It is worth stressing that this style of attack on a device is very limited in scope. The attacker has to both physically access the device and call it from another iPhone in order to access FaceTime in the first place, and the information that can be gathered only relates to contacts, so a user's private data stored on the iPhone itself is not at risk.
It is likely that Apple will issue a fix for this vulnerability in a future iOS update, but it is unknown how long users may have to wait before it is released.
 Malcolm Owen
Malcolm Owen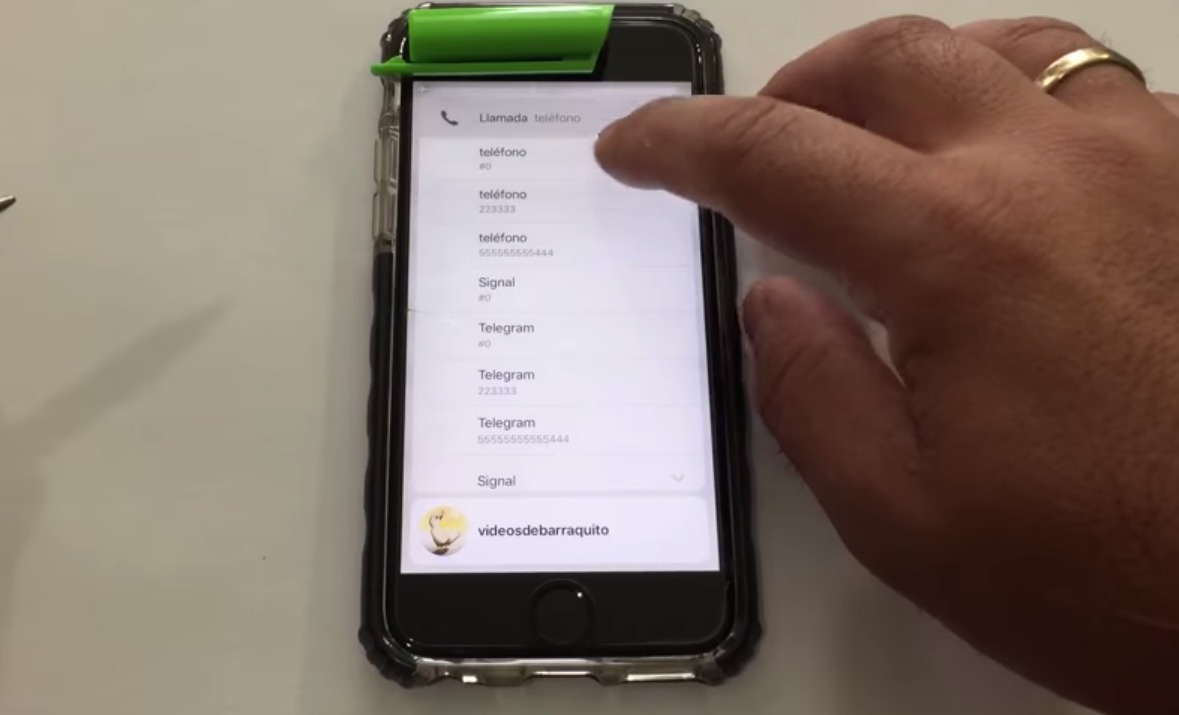











 Andrew Orr
Andrew Orr
 Sponsored Content
Sponsored Content


 William Gallagher
William Gallagher

 Mike Wuerthele
Mike Wuerthele
 Christine McKee
Christine McKee







