Popular iOS apps use Glassbox SDK to record user screens without permission [u]
A number of popular iOS apps paying data analytics services for so-called "session replay" technology have the ability to record and play back user interactions, often without asking permission, according to a new report.
According to an investigation conducted by TechCrunch, analytics firm Glassbox, and other companies like it, allow customers to embed session replay technology into their respective apps. These tools capture
screenshots and user interactions, including on-screen taps and in some cases keyboard entries, which are sent back to app developers or Glassbox servers for further examination.
Though not as polished as the video-enabled screen recording function built into iOS 12, session replay technology effectively screenshots an app's user interface at key moments to determine whether it is functioning as designed, the report said.
"Glassbox has a unique capability to reconstruct the mobile application view in a visual format, which is another view of analytics, Glassbox SDK can interact with our customers native app only and technically cannot break the boundary of the app," a Glassbox spokesperson told the publication. More specifically, when a keyboard overlay appears above the native app, "Glassbox does not have access to it."
Glassbox customers include big-name corporations like Abercrombie & Fitch and sister brand Hollister, Hotels.com, Expedia, Air Canada and Singapore Airlines.
While user monitoring is nothing new, and in many cases should be expected, mishandling of session replays can lead to leakage of sensitive information.
Citing a recent report from The App Analyst, TechCrunch notes Air Canada's app was found to be sending session replay data containing exposed passport and credit card numbers. This could be a problem, as some companies opt to send app data directly to Glassbox's cloud and not their own servers.
In its own study, which employed man-in-the-middle software to monitor data being sent from target apps, the publication discovered data transmitted to Glassbox was "mostly obfuscated," though some screenshots contained umasked email addresses and postal codes. Of the apps listed above, Abercrombie & Fitch, Hollister and Singapore Airlines passed session replay data on to Glassbox, while Hotels.com and Expedia siloed data on their own domains.
Further, none of the apps reviewed as part of the investigation make clear in their respective privacy policies that Glassbox technology is being employed to record users' screens.
In response to the TechCrunch report, Glassbox said it is a strong supporter of user privacy and provides customers with tools to obfuscate "every element" of personal data. The company believes that its customers should make users aware that their data is being recorded.
"Glassbox and its customers are not interested in "spying" on consumers. Our goals are to improve online customer experiences and to protect consumers from a compliance perspective," the company said in a statement provided to AppleInsider.
Glassbox went on to say that its platform is secure, encrypted and meets security and data privacy standards and regulations like SOC2 compliance and GDPR. No data is shared with third parties, the company said.
Still, as some Glassbox customers currently do not include mention of user monitoring in Apple-mandated disclosures, and with Glassbox itself lacking requirements of its own, end users are largely unaware that their actions are being so closely observed. More concerning, however, is that iOS app makers are in some cases funneling sensitive data to a third party without express user permission and absent of proper encryption protocols.
Updated with response from Glassbox
 Mikey Campbell
Mikey Campbell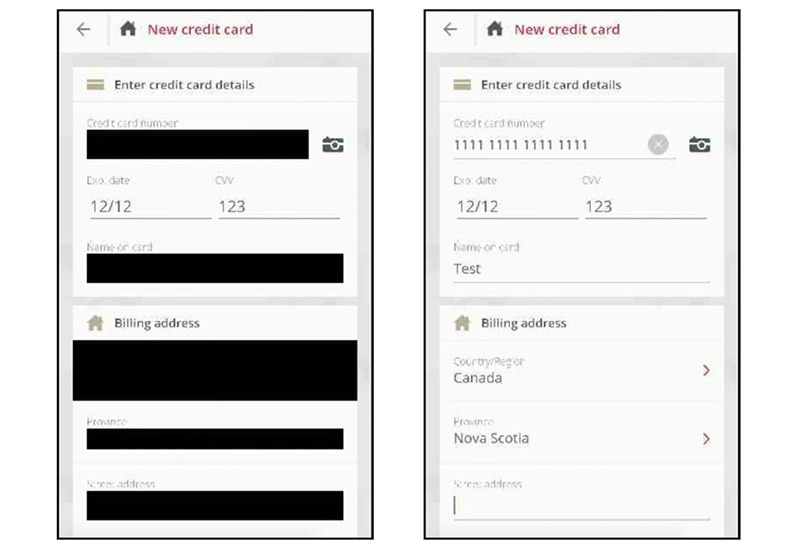









 William Gallagher
William Gallagher
 Malcolm Owen
Malcolm Owen
 Amber Neely
Amber Neely

 Marko Zivkovic
Marko Zivkovic

 Andrew Orr
Andrew Orr








