Twitter confirms staff manipulated for high-profile account access by hackers
Twitter's employees were manipulated into providing access to the social network's internal systems to attackers, the company has revealed in an update to its investigation into a recent Bitcoin scam, one that affected prominent accounts including Apple.
Published late on Friday, the update details what Twitter's security teams believes happened on July 15, which saw a number of Twitter accounts with high follower accounts post a tweet designed to take Bitcoin payments from the account's readers.
Twitter's summary of events seemingly confirms early reports claiming some sort of social engineering was attempted, the microblogging service believes attackers targeted "certain Twitter employees" and was successful with a small number. Credentials acquired via the scheme were then used to access Twitter's internal systems, including getting through the company's two-factor protections.
As of the time of the update, Twitter believes only 130 accounts were targeted in the attack, which included Apple and personalities such as Tesla's Elon Musk and Amazon's Jeff Bezos. For 45 of the accounts, attackers were able to "initiate a password reset, login to the account, and send tweets."
Up to eight of the accounts were also subjected to an extra step, where the attackers used the "Your Twitter Data" tool to acquire more details about the account and the user. Interestingly none of the eight accounts this happened to were verified accounts.
Following the discovery of the attack, Twitter's incident response team secured and revoked access to the systems to prevent any further damage. Other preemptive measures were also taken by the team, including preventing accounts from tweeting or changing passwords "to prevent the attackers from further spreading their scam as well as to prevent them from being able to take control of any additional accounts" while the investigation was in progress.
Multiple teams are said to be working around the clock and with law enforcement on the investigation, and determining longer-term actions Twitter needs to implement to improve its security.
In terms of the information that the attackers were able to access, Twitter believes the private details for the "vast majority" of accounts wasn't accessed. For the known 130 accounts, Twitter knows the attackers were not able to see previous account passwords as they were not stored in plain text nor available in tools, but they were able to view personal information including email addresses and phone numbers.
Twitter claims it is "actively working on communicating directly with the account-holders that were impacted" by the breach.
Along with restoring account access to still-locked accounts, continuing the investigation, and increasing system security, Twitter will be instigating company-wide training to "guard against social engineering tactics," furthering training received through onboarding and its regular self-instigated phishing exercises.
"We're acutely aware of our responsibilities to the people who use our service and to society more generally," the update concludes in its apology. "We know that we must work to regain your trust, and we will support all efforts to bring the perpetrators to justice."
The update ends "We hope that our openness and transparency throughout this process, and the steps and work we will take to safeguard against other attacks in the future, will be the start of making this right."
 Malcolm Owen
Malcolm Owen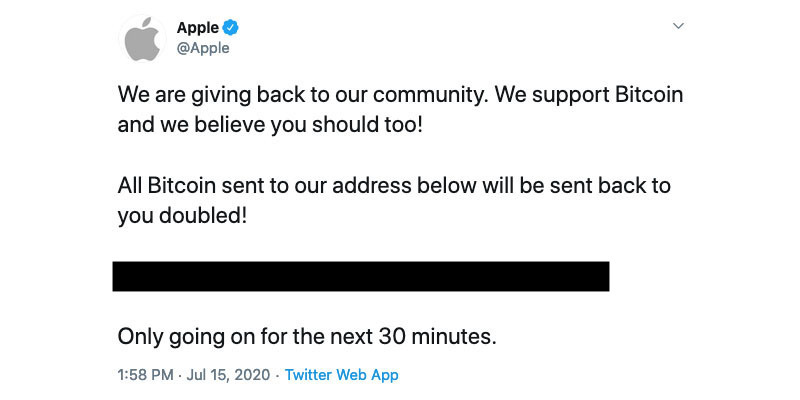











 Andrew Orr
Andrew Orr
 Sponsored Content
Sponsored Content


 William Gallagher
William Gallagher

 Mike Wuerthele
Mike Wuerthele
 Christine McKee
Christine McKee







