Researchers reverse-engineer Find My, detail potential privacy & security issues
A team of security researchers managed to hack Apple's Find My protocol to test its security and privacy, and they've created an open-source app that allows users to create their own "AirTags."
The app, called OpenHaystack, is a framework for tracking Bluetooth devices using Apple's Find My system developed by researchers from the Secure Mobile Networking Lab at the Technical University of Darmstadt. It actually leverages Apple's network of devices, such as iPhones, to allow users to track non-Apple products offline.
"All you need is a Mac and a BBC micro:bit or any other Bluetooth-capable device. By using the app, you can track your micro:bit tag anywhere on earth without cellular coverage," the creators wrote. "Nearby iPhones will discover your tag and upload their location to Apple's servers when they have a network connection."
Like Apple's proprietary offline tracking, OpenHaystack works by setting a beacon to send out specific Bluetooth signals. Nearby iPhone devices receive these signals, assume that the beacon is lost, and send their geolocation data to Apple via end-to-end encryption. OpenHaystack then downloads and decrypts these reports and sends them to the Mac framework.
Users can create their own Bluetooth tracking tags using the system, including from Bluetooth dongles and other devices. From there, they can see a tag's most recent location on a map. Although the system only current supports a micro:bit device, its creators say it's possible to implement it on any Bluetooth Low Energy device.
OpenHaystack works in two parts: a macOS app and a firmware image that can be flashed onto Bluetooth devices to make them discoverable by nearby iPhones. The Mac app requires macOS Big Sur or later.
The team, including security researchers Alexander Heinrich and Milan Stute, developed the framework when reverse-engineering Apple's closed-sourced Find My protocols as part of a broader privacy and security analysis. As they note, Apple has released a partial specification of the Find My protocol, but has never detailed all of its components.
As part of that analysis, the team also discovered two vulnerabilities in Apple's crowd-sourced Find My system. The researchers outlined their privacy and security findings in a research paper.
"While we find that [offline finding's] design achieves its privacy goals, we discover two distinct design and implementation flaws that can lead to a location correlation attack and unauthorized access to the location history of the past seven days, which could deanonymize users. Apple has partially addressed the issues following our responsible disclosure. Finally, we make our research artifacts publicly available," the researchers wrote.
One of the flaws has been patched by Apple, although another remains a problem. Despite being credited for discovering it, the researchers said they never received a bounty.
The OpenHaystack framework, as well as related documentation and other information, is available over at Github.
 Mike Peterson
Mike Peterson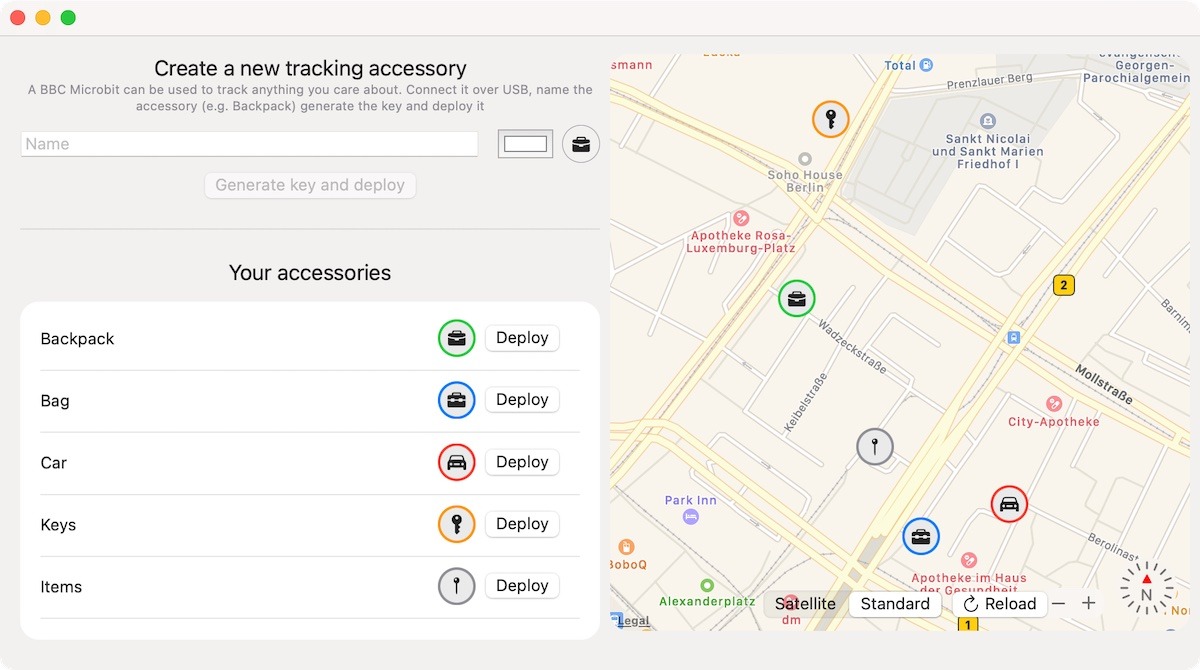











 William Gallagher
William Gallagher

 Andrew Orr
Andrew Orr

 Marko Zivkovic
Marko Zivkovic
 Malcolm Owen
Malcolm Owen
 Christine McKee
Christine McKee








