Apple tech support 'socially engineered' in hack of journalist's iCloud account
The hack was first thought to be a simple brute force attack on Honan's seven-digit alphanumeric iCloud password, which he has used for "years and years," though in the process of reconfiguring accounts it was confirmed that the issue wasn't a password, but the "social engineering" of an Apple tech support employee.
In recounting the experience on his blog, Honan first realized something was amiss when his iPhone rebooted to the default setup screen. He couldn't log in to iCloud to restore the handset's previous settings from the device itself, so Honan connected the iPhone to his MacBook Air which displayed an iCal error message before its screen went gray and asked for a four digit PIN.
"I didn’t have a four digit pin," Honan wrote. "By now, I knew something was very, very wrong. I walked to the hallway to grab my iPad from my work bag. It had been reset too. I couldn’t turn on my computer, my iPad, or iPhone."
Things got progressively worse from there as Honan's Google account was deleted, the only way to restore it would be via text message to the iPhone he no longer had access to. The tech writer's Twitter feed, along with his previous employer Gizmodo's, were also compromised. Perhaps most troubling was that his MacBook Air was being remotely wiped, along with his iPad and iPhone, using Apple's Find My Device feature. The wipe may be recoverable, however, as Honan stopped the process by powering the MacBook Air down before an over-write began.
Find my iPhone on iOS 5.
Honan noted in a blog update that a person claiming to be the hacker made contact and told him "[I] didn't ur password or use bruteforce. i have my own guide on how to secure emails."
From Honan's blog:
I know how it was done now. Confirmed with both the hacker and Apple. It wasn’t password related. They got in via Apple tech support and some clever social engineering that let them bypass security questions. Apple has my Macbook and is trying to recover the data. I’m back in all my accounts that I know I was locked out of. Still trying to figure out where else they were.
In the last update to Honan's saga, AppleCare was able to confirm the hacker's claims of bypassing iCloud's password protection by going through an employee. A more detailed account of how this was done will be made public in a Wired report on Monday.
Honan reached out to Apple Corporate as well as the company's PR team, though no response has been given at the time of this writing.
 Mikey Campbell
Mikey Campbell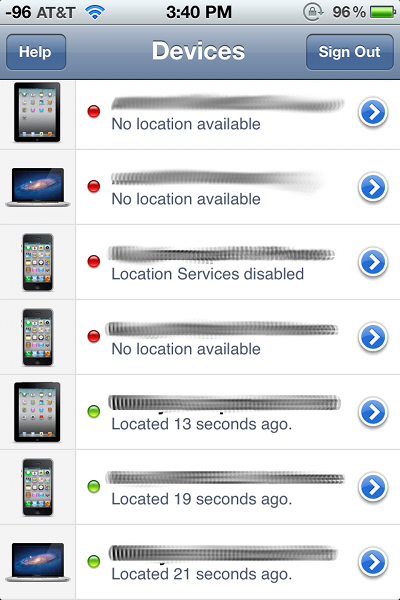











 Andrew Orr
Andrew Orr
 Malcolm Owen
Malcolm Owen

 William Gallagher
William Gallagher

 Mike Wuerthele
Mike Wuerthele
 Christine McKee
Christine McKee