Google's initial Android Stagefright patch inadequate, forced to issue second fix
The first software patch designed to mitigate the high-profile Stagefright vulnerability in Google's Android mobile operating system was insufficient, one security researcher discovered, leading to the issuance of yet another update.
Last week, security expert Jordan Gruskovnjak found that one version of the Stagefright patch — Â which allows a malformed MP4 file to cause an integer overflow — Â did not fully address the problem, and was able to bypass the fix with a new proof of concept. Google was notified on August 7, and has already begun distributing another update.
"We've already sent the fix to our partners to protect users, and Nexus 4/5/6/7/9/10 and Nexus Player will get the OTA update in the September monthly security update," a Google spokesperson told Threatpost.
Wireless carriers in the U.S. have also chipped in, working to block transmission of MMS messages that contain exploitable payloads.
First revealed publicly in late July, the Stagefright exploit relies on a bug in Android's media handling library. It allows attackers to craft a malicious MMS message that would execute arbitrary code whenever received by or opened on an Android device.
"Attackers only need your mobile number, using which they can remotely execute code via a specially crafted media file delivered via MMS," the flaw's discoverers explained at the time. "A fully weaponized successful attack could even delete the message before you see it. You will only see the notification."
Last week, Google announced plans to begin issuing regular monthly security updates for Nexus users. LG and Samsung have signed on to distribute those patches to their devices as well.
 AppleInsider Staff
AppleInsider Staff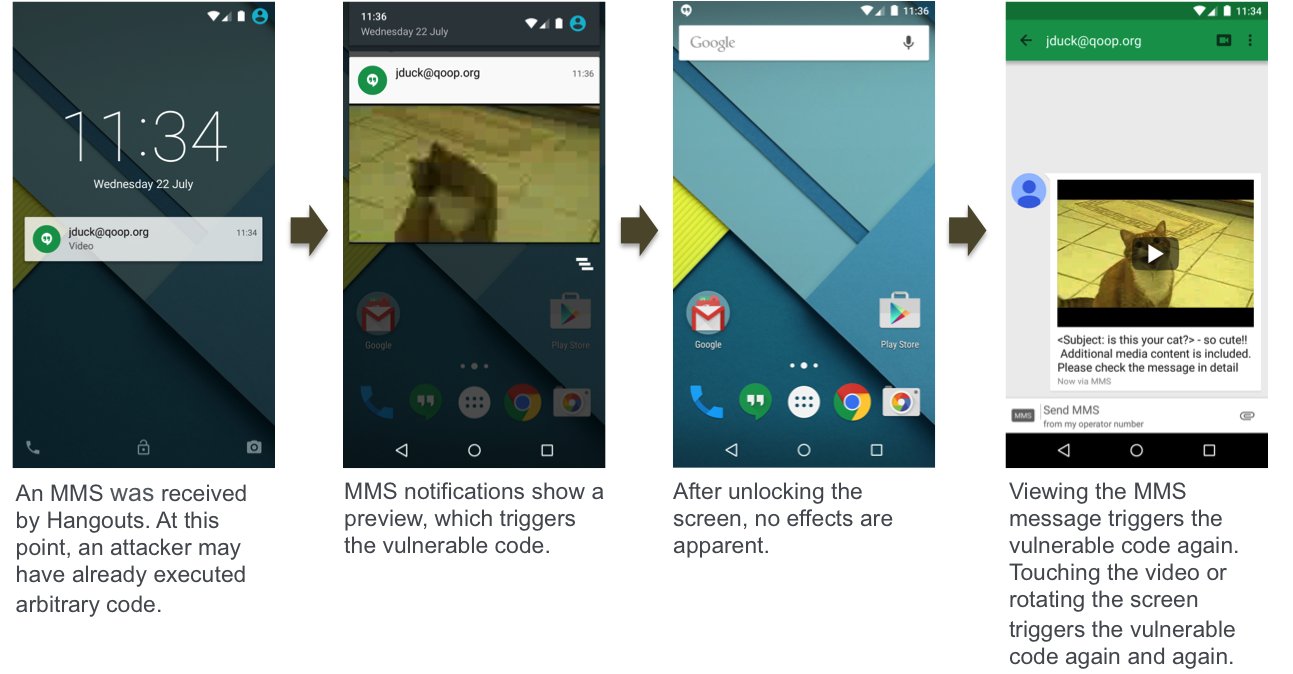











 Malcolm Owen
Malcolm Owen
 William Gallagher and Mike Wuerthele
William Gallagher and Mike Wuerthele
 Christine McKee
Christine McKee
 William Gallagher
William Gallagher
 Marko Zivkovic
Marko Zivkovic









