Three new malware strains infect 20k apps, impossible to wipe, only affect Android
A new adware scourge injecting itself into popular apps such as Facebook and Twitter is also "virtually impossible to uninstall," requiring infected users to replace their phones. Because it only affects users of Google's open-store Android app model, the device replacement requirement may accelerate the trend of users switching to iOS.
"A new trend for adware and an alarming one at that"
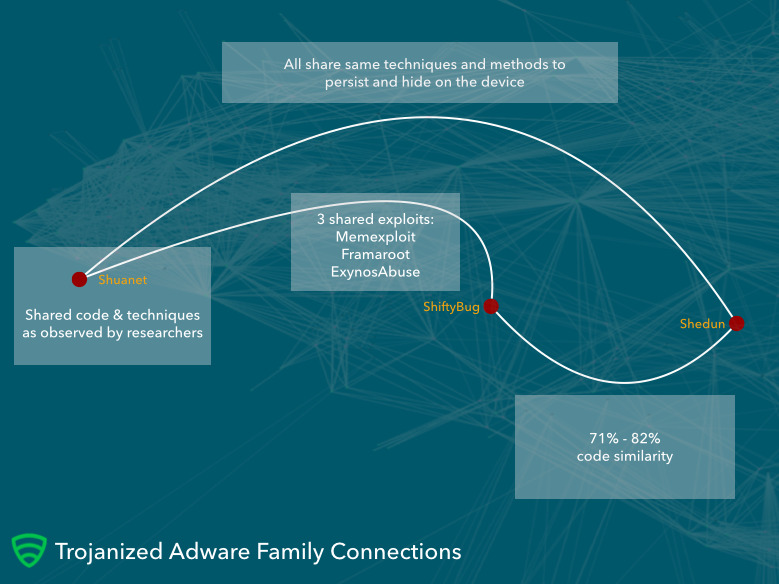
Three new families of "auto-rooting adware," detailed by security researchers at Lookout, are "a worrying development in the Android ecosystem" because each can root the device and install itself as a system application, making the contamination virtually impossible to remove as the infection is designed to survive even a "factory data reset" device wipe.
The group found infections among more than 20,000 popular apps, with many contaminated apps appearing to be legitimate, working titles ranging from Candy Crush to Facebook to Snapchat, WhatsApp, The New York Times and even Google Now. The infection is designed to survive even a "factory data reset" device wipe
The three malware families (named Shedun, Shuanet and ShiftyBug) are closely related but appear to be independently authored. Each relies on "publicly available exploits that perform the rooting function" and their "authors used the same pieces of code to build their versions of the auto-rooting adware," the researchers noted, leveraging the ecosystem of powerful and easy to find tools for attacking Android devices.
"For individuals, getting infected with Shedun, Shuanet and ShiftyBug might mean a trip to the store to buy a new phone. Because these pieces of adware root the device and install themselves as system applications, they become nearly impossible to remove, usually forcing victims to replace their device in order to regain normalcy," noted researcher Michael Bentley."Getting infected with Shedun, Shuanet and ShiftyBug might mean a trip to the store to buy a new phone," - Lookout
The discovered app infections were concentrated in "United States, Germany, Iran, Russia, India, Jamaica, Sudan, Brazil, Mexico and Indonesia," a series of countries where Apple is already experiencing significant switcher growth from Android.
Tim Cook specifically noted Indonesia and India among the emerging markets where he said he was "really impressed last quarter with our progress."
Apple's iPhone has previously had limited exposure in India, where according to a recent report by the Financial Times, it has maintained just 1 to 2 percent share of smartphone by units (albeit a 10 percent share by value).
An attack on the permissive software model of Android
The contaminated apps Lookout found were harvested from Google Play, infected with a payload and then republished on third party app sites enabled by Google's open app model allowing Android users to find and download apps from multiple stores.
Apple has repeatedly maintained that Android's permissive software installation "features" were a security risk, but Android's architects, partners and enthusiast users denied this while portraying Apple's App Store model— providing a single, vetted source for iOS apps— as being an unnecessarily restrictive "Walled Garden."
In addition to being a problem for individuals, Lookout also noted that the auto-rooting malware is a special concern for business users, "especially if those devices were rooted by a repackaged version of a legitimate and popular enterprise app.
"In this rooted state, an everyday victim won't have the proper interface to control what apps on the phone request root access. The problem here is that these apps may gain access to data they shouldn't have access to, given their escalated privileges."
Google's Android software model not only facilitates the increasingly large business of copying legitimate apps and distributing them with a malware payload, but also makes Android a ripe platform for piracy and counterfeiters, a reality that has hurt its ability to foster legitimate commercial app development.
The current problems posed by Shedun, Shuanet and ShiftyBug are difficult for Google to address because it has no effective control over third party app stores, apart from advising Android users not to use them— after spending years claiming that third party stores would be a feature, not a peril.
It's also a defamation problem for legitimate app developers, as many users won't understand why legitimate-appearing software, branded as coming from Facebook, known game developers or even Google, is damaging their phone to the point of requiring a replacement.
"We believe more families of adware trojanizing popular apps will emerge in the near future and look to dig its heels into the reserved file system to avoid being removed," Lookout noted.
Apple has continued to block efforts to root iPhones, addressing jailbreak exploits in new releases of iOS that make it increasingly difficult— and increasingly unpopular— to seek apps from any source outside of the official App Store. That's enabled the company to address problems quickly by banning apps that overstep Apple's curation policies, including malware and data collection, as it recently did to contain XcodeGhost.
 Daniel Eran Dilger
Daniel Eran Dilger









 Marko Zivkovic
Marko Zivkovic
 Amber Neely
Amber Neely
 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen
 Mike Wuerthele and Malcolm Owen
Mike Wuerthele and Malcolm Owen

 William Gallagher
William Gallagher







