38 million records left exposed on public databases thanks to weak Microsoft Power App defaults
Many companies use Microsoft's Power App platform, and sensitive data for 38 million records was left exposed to the public for months, thanks to weak default security settings.
Research conducted by Upguard showed that a concerning number of Power App users were not securing their databases. Further investigation revealed that this issue was created by weak default security settings, leaving data exposed if users took no manual action.
According to a report from Wired, data was left exposed from sources like American Airlines, Ford, New York City public schools, and multiple state's COVID-19 contact tracing databases. The initial discovery by Upguard was made in May 2021, but a fix from Microsoft wasn't fully rolled out until August.
"We found one of these that was misconfigured to expose data and we thought, we've never heard of this, is this a one-off thing or is this a systemic issue?" says Greg Pollock, UpGuard's vice president of cyber research. "Because of the way the Power Apps portals product works, it's very easy to quickly do a survey. And we discovered there are tons of these exposed. It was wild."
Upguard began investigating a large number of Power App portals that should have been private — even apps made by Microsoft were misconfigured. However, despite being open to the public, none of the data is known to have been compromised.
The core of the problem lies in default security settings. For example, when setting up the Power App and connecting APIs, the platform defaulted to make corresponding data publicly accessible.
Thanks to an update in August, Power Apps will default to secure settings to keep data private. Upguard made an effort to communicate with platforms with sensitive data left in the open, but the scale of the security issue was too broad to account for every business.
"Secure default settings matter," says Kenn White, director of the Open Crypto Audit Project. "When a pattern emerges in web-facing systems built using a particular technology that continue to be misconfigured, something is very wrong. If developers from diverse industries and technical backgrounds continue to make the same missteps on a platform, the spotlight should be squarely on the builder of that platform."
Exposed data included several Covid-19 contact tracing platforms, vaccination sign-ups, job application portals, and employee databases. Anything from social security numbers to names and addresses were left in open databases.
Again, Upguard says the none of the data is known to be compromised.
The Microsoft Power App security settings problem echoes many other platform's issues in this sector. Companies like Amazon and Google have frequently dealt with weak default settings leading to data exposure.
 Wesley Hilliard
Wesley Hilliard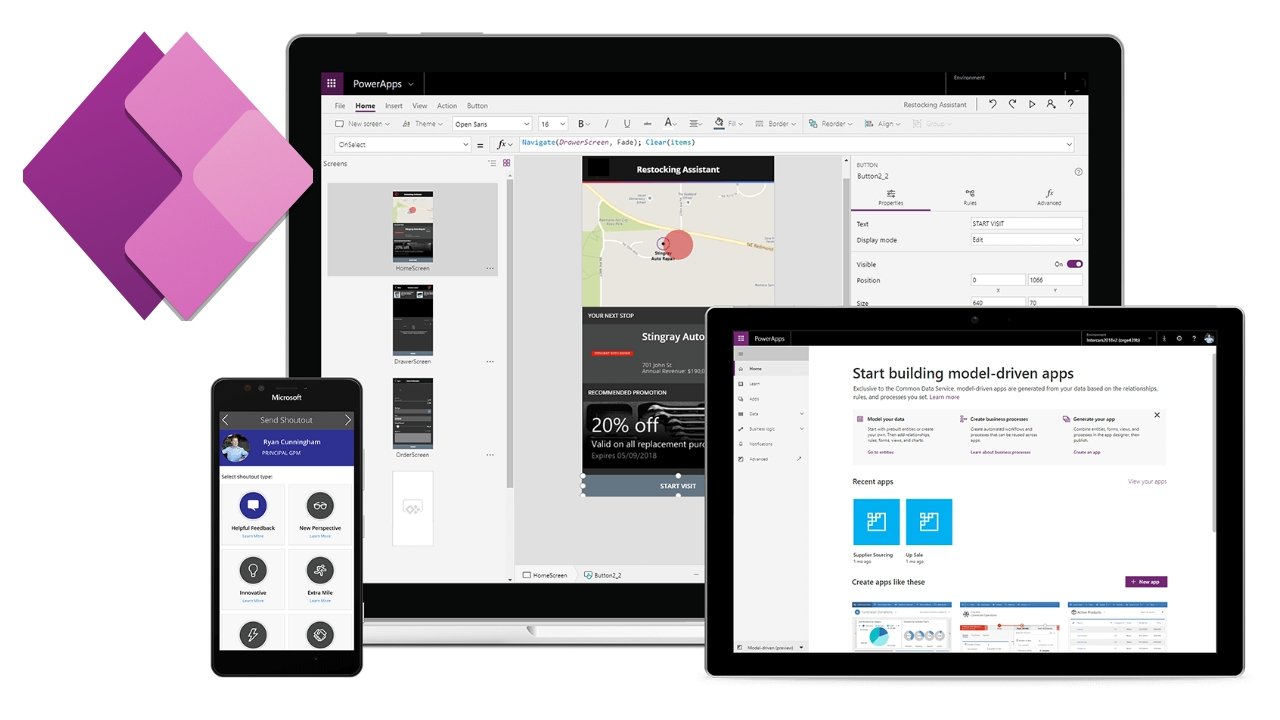









 Marko Zivkovic
Marko Zivkovic
 Amber Neely
Amber Neely
 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen
 Mike Wuerthele and Malcolm Owen
Mike Wuerthele and Malcolm Owen

 William Gallagher
William Gallagher








