An Apple patent application discovered on Thursday describes an authentication system for portable media devices much like the solution used in the company's Lightning cable, the iDevice-centric successor of the venerable 30-pin dock connector.
Source: USPTO
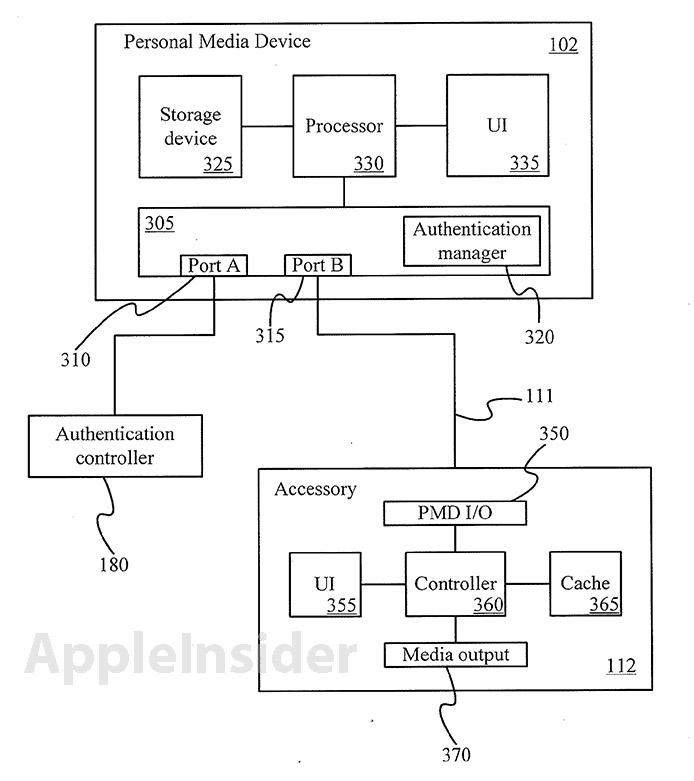
The patent, titled "Cross-transport authentication," requires authentication controllers to be located at either the ports on a portable device and attached accessory, or the transport connector which can be a wire or cable. As seen with Apple's Lightning connector, the authentication module can take the form of a chip integrated at one side of the cable, providing the necessary permissions for an accessory to interface with a portable device.
In order to function, the authentication controller in the cable communicates a cross-transport request from the accessory or portable device and the subsequent permissions to interface or control said device. Because the authentication controller in the connector can be coupled to a number of communication channels, it can transmit audio, video and control signals along with the necessary permissions.
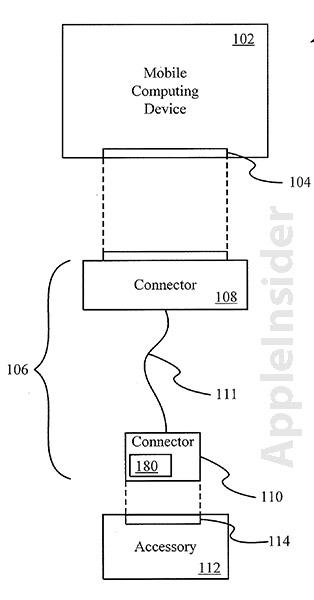
Embedded authentication controller (180) in cable.
Other embodiments are described in which authentication controllers are present at both the portable device and the accessory, however it appears that Apple has chosen to rely on security embedded into the cable itself.
From the patent application's abstract:
In one embodiment, authentication controller is implemented on a single integrated circuit, for example, on a single chip. By providing authentication controller on a single integrated circuit, external access to private key and/or authentication algorithm may be substantially reduced. As a result, the authentication process may not only be cryptographically secured but also physically secured by limited physical access.
The filing's summary offers a glimpse at why Apple chose to use authentication embedded in the new Lightning connector rather than use more conventional security options:
Existing interface protocols allow a portable media device (PMD) to control whether and how an accessory accesses functionality of the PMD. Such protocols restrict and/or limit access by third party devices that are error prone, disruptive, resource draining, and/or damaging to the media player. Moreover, such protocols may provide copy protections to media resources that are subject to copy restrictions.
Sample implementation of patent application.
While physical authorization controllers may be a better fit for Apple's latest connector, the solution is not bulletproof, as evidenced by purported "cracked" authentication chips making their way out of China. Unauthorized third-party manufacturers are already producing cheap "knock-off" cables that are fully-functional, and may cut into Apple's profits if already constrained supplies aren't boosted.
It is unclear how the unlicensed parts will affect Apple's plans to collect royalties on "Made for iPhone/iPad/iPod" accessories, but it seems that the company's attempts to maintain total control over the third-party accessory cottage industry has been thwarted even before the first licensed products roll off the assembly line.