Security researchers at Johns Hopkins University have demonstrated a unique new attack that can force the iSight cameras in legacy MacBook and iMac models to capture images without turning on the camera's accompanying LED.
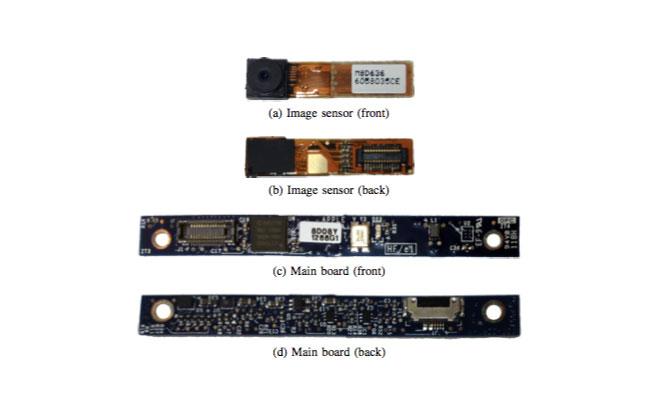
The individual parts of the iSight camera that was the subject of the attack
Researchers Matthew Brocker and Stephen Checkoway outline the attack, which targets the firmware inside the iSight camera's controller chip, in a paper entitled "iSeeYou: Disabling the MacBook Webcam Indicator LED." The paper was first reported by the Washington Post.
Apple designed the iSight camera system with a "hardware interlock" between the camera sensor and the indicator LED that was intended to make it electrically impossible for one to be activated without the other. According to the paper, the LED is connected directly to the standby pin on the camera sensor --Â when the camera comes out of standby mode, the LED automatically turns on.
Brocker and Checkoway were able to bypass the hardware interlock by reprogramming the firmware on the camera's microcontroller to ignore standby signals sent by the USB interface that the camera uses to communicate with the rest of the computer. In this way, the LED remains off --Â because it is still obeying the USB standby signal -- even though the camera sensor is active.
The attack is particularly worrisome because it does not require administrator-level privileges or physical access to the laptop, though at this time it only affects MacBooks and iMacs manufactured prior to 2008 with built-in iSight cameras, and the researchers indicated that there are at least two methods of mitigating the vulnerability that can be rolled out to existing hardware.
Apple's Gatekeeper application sandbox, introduced with OS X Mountain Lion, could be updated to deny untrusted applications access to the camera and its USB controller. Another strategy, which Brocker and Checkoway have developed a proof-of-concept for, would extend OS X's kernel to disallow specific instructions from being sent to the camera in the first place.
The researchers disclosed the hack to Apple's security team earlier this summer, according to the paper. "Apple employees followed up several times but did not inform us of any possible mitigation plans," the duo wrote.

