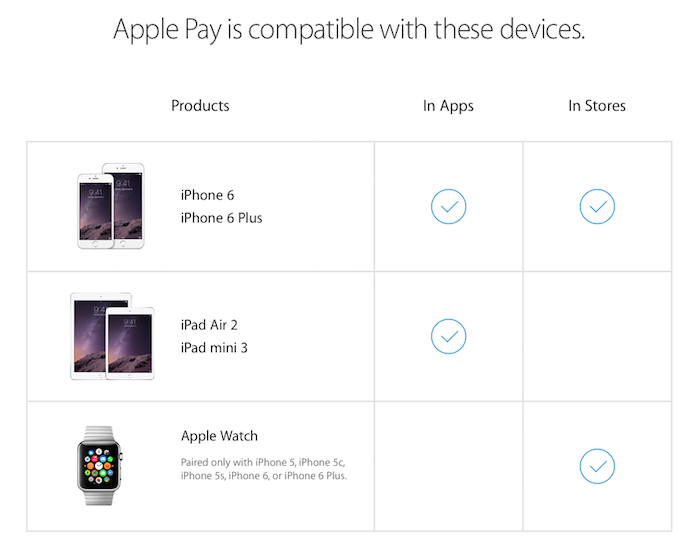
Apple's newest iPads feature one of the same chips used by iPhone 6 and 6 Plus to handle tap-to-pay NFC transactions, but the new iPad Air 2 and iPad mini 3 only support Apple Pay within apps, sparing users the embarrassment of carrying around a gigantic alternative to their credit card.
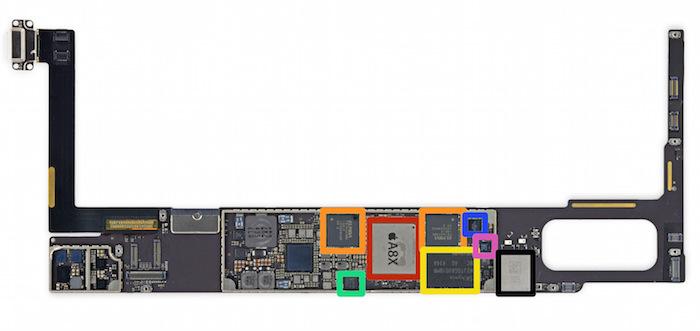
After iFixit.com identified a NFC chip (the NXP 65V10 NFC Controller) in Apple's new iPad Air 2 as being the same as one found in iPhone 6 and 6 Plus (highlighted in green, below), a variety of news sources speculated that this would enable a future software upgrade to NFC proximity Apple Pay transactions.
However, the new iPads lack both supporting logic chips and the antenna required to perform wireless transactions over NFC. This will also prevent merchants from being able to use the new iPad as an NFC "Point of Sale" device to accept Apple Pay transactions.
Fortunately, however, Apple Pay can also be transacted via merchant apps, obviating any need for stores to actually replace all of their existing POS devices with new iPad models in order to begin accepting Apple Pay purchases.
Apple's own retail store app, along with apps ranging from OpenTable and Groupon to Lyft and Uber to Instacart and Hotel Tonight to Panera Bread and Target (and expanding to AirBnb, Disney, Starbucks, Levis, Sephora, Eventbrite Ticketmaster, StubHub and the Major League Baseball app by the end of 2014) have already initiated Apple Pay within their apps, enabling new iPad Air 2 and iPad mini 3 users to make secure purchases via Touch ID just as iPhone 6 and iPhone 6 Plus can.
Because the latest iPads with Touch ID can support Apple Pay in apps, but not at retail stores, they do not have a Passbook app. Instead, they handle all Apple Pay credit card configuration entirely within Settings under "Passbook & Apple Pay" (shown below).
Apple Pay requires an NFC Secure Element
This type of in-app Apple Pay requires an NFC "Secure Element," a special storage block typically built into an NFC controller chip, which securely stores the user's payment information. This chip interfaces directly with the separate Secure Enclave processing core in Apple's A7, A8 or A8X Application Processors to authenticate the user via a fingerprint scan and then unlock the user's payment credentials in the form of a secure token.
This payment mechanism erects firewalls that strictly prevent any apps on the system from being able to sneak any access to either the user's fingerprint-related data or their credit card credentials, even if the user were tricked into installing a malicious app designed expressly to steal their information. In-app Apple Pay requires an NFC "Secure Element," a special storage block typically built into an NFC controller chip, which securely stores the user's payment information
The only way Apple Pay can access the account token from the Secure Element is by verifying a fingerprint with Touch ID. And the most cost effective and secure way to create such a secure environment is to incorporate a Secure Element on a standard chip designed to support NFC payments.
Last year's iPhone 5s has Touch ID and an A7 with the Secure Enclave to secure their fingerprint data (the chip doesn't actually store a fingerprint image, but rather a number derived from the user's fingerprint scan that can be used to verify subsequent scans as coming from the same user and nobody else).
However, the first generation Touch ID phone lacks an NFC chip supplying a Secure Element, so iPhone 5s can't make in app Apple Pay purchases (or of course, NFC in store purchases) unless it is paired with the upcoming Apple Watch, which will incorporate its own NFC wireless radio.
Because Apple Watch verifies the user via a PIN code entry when it is put on, Apple Pay on Apple Watch won't require Touch ID, meaning it will work with both iPhone 5 and iPhone 5s. Once Apple Watch is removed, it erases its PIN and requires the user to again authenticate before making new Apple Pay transactions, a design intended to prevent theft.
All Apple devices capable of running iOS 7 or iOS 8 also support Activation Lock, which prevents thieves from simply erasing and factory resetting stolen iOS devices for easy resale once a passcode is set up.
Apple's Touch ID additionally simplifies the use of passcodes, making it effortless to unlock an iPhone or iPad secured with Activation Lock without constantly retyping one's passcode.
Outside of Apple: activation lock & NFC on Android and Windows Phone
Smartphones from Google and Microsoft are legally mandated to supply a similar anti-theft mechanism by the middle of next year under a new law passed in California. Complying with this law will be complicated by the fact that most non-Apple phones lack a fingerprint sensor for easily unlocking the device, and those that do (like Samsung's Galaxy S5) reportedly do not work well and are not similarly secured by a mechanism like Apple's Secure Enclave.
Additionally, while early Android phones supporting NFC payments via Google Wallet incorporated an NFC Secure Element, Google shifted its proximity payment strategy after gaining very little traction for Wallet (even as it financed and built out much of the existing NFC infrastructure needed to support Apple Pay by iPhone 6 models and Apple Watch) to instead use "Host Card Emulation," which is verified in the cloud rather than against data stored locally in a Secure Element.
This enabled new Android devices to ship without a Secure Element (such as the 2013 Nexus 7) and yet still make NFC purchases.
However, because "HCE" Google Wallet transactions must verify transactions via the cloud, payments only work when the user has data service. In-store Apple Pay does not require data service to function, so it will work for merchants in underground malls or--perhaps in the future--to buy drinks on airplanes, even without logging into Gogo inflight Internet.
This summer, Google Wallet was identified as a built-in Android app susceptible to the Fake ID flaw, which allows any Android app to pretend to be another app, and thereby gain all of its privileges.
Any app pretending to be Google Wallet can gain full access to the user's NFC payment credentials. This sort of NFC exploit is not possible on iOS, firstly because Apple's mobile OS actually verifies app's security certificates, and secondly because there are no apps on iOS that can read the Secure Element without first authenticating through the Secure Enclave built into in Apple's custom Application Processors.