Google has confirmed a recent update to Chrome was to patch a zero-day issue in the popular browser, an exploit that was actively used in attacks, and has recommended all Chrome users on Mac, Windows, and Linux update their installations as soon as possible.
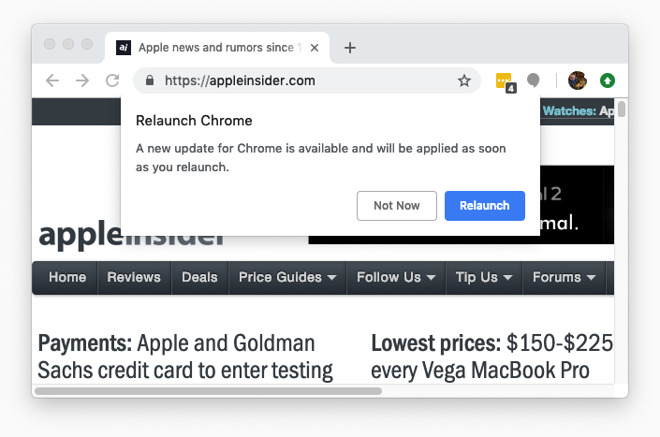
Chrome's update dialog box when a patch is ready to install
A patch for Chrome shipped on March 1 consisting of a fix for a security flaw, identified as CVE-2019-5786. The update, which only fixed the issue without making other changes to the browser, brought Chrome on all three operating systems up to version 72.0.3626121.
While the security flaw affected all desktop versions of Chrome, it was especially a problem for Windows users, as it formed part of a more complex attack against Windows 7. The older Microsoft operating system had its own zero-day flaw identified at the same time as the Chrome version, with the browser's flaw actively used as part of a more complex attack against Windows, reports CNET.
Also, seriously, update your Chrome installs... like right this minute. #PSA
-- Justin Schuh (@justinschuh) March 6, 2019
Google updated its announcement for the patch to advise the exploit against Chrome "exists in the wild." Justin Schuh, head of Google's Chrome Security, posted to Twitter advising of both the exploit's existence and advising users to update their browser with the new patch.
The issue lies in a memory management error for Chrome's FileReader API, which allows web apps to read local files on a desktop. Specifically, it is a memory error known as a "use-after-free" vulnerability when a web app attempts to access memory that had been freed or deleted from Chrome's allocated memory, with the flaw enabling malicious code to be executed.
Clement Lecigne of Google's Threat Analysis Group is credited as the researcher who found the bug.
Google Chrome for iOS is not affected by the security flaw.
