Secret documents that anonymously leaked from global surveillance firm Gamma Group detail broad powers to spy on Android users via its FinSpy tool sold to law enforcement, but note that the tools lack the ability to infect iPhones unless they have been jailbroken.
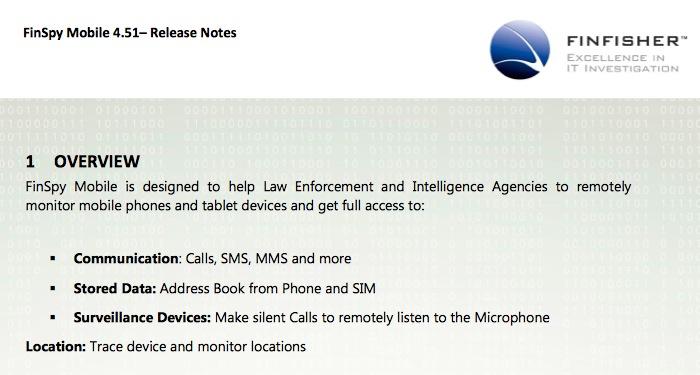
One of the leaked documents described FinSpy Mobile as being "designed to help Law Enforcement and Intelligence Agencies to remotely monitor mobile phones and tablet devices and get full access to:
"Communication: Calls, SMS, MMS and more; Stored Data: Address Book from Phone and SIM; Surveillance Devices: Make silent Calls to remotely listen to the Microphone; and Location: Trace device and monitor locations."
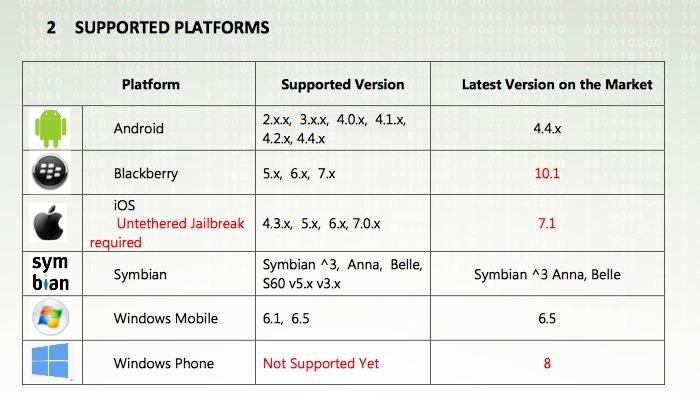
The regularly updated software tool supports all releases of Android, devices running BlackBerry OS prior to the newest BB10, Symbian and Windows Mobile phones, but notes that in order to spy on an iPhone, the user must jailbreak their device, a step that disables Apple's security.
A report by the Washington Post noted that the tool is "capable of listening to calls on targeted devices, stealing contacts, activating the microphone, tracking your location and more. But for FinSpy to hack into an iPhone, its owner must have already stripped away much of its built-in security through a process called 'jailbreaking.'"
The site stated, "This is good news for people with iPhones, and perhaps for Apple as well," but added that "it's ironic" that "a different mobile operating system - Google's Android - has emerged as the global standard," noting of Android phones that "they're cheaper. But, it's increasingly clear, they are more vulnerable to the Gammas of the world, and from the police and intelligence services that use their tools."
The Surveillance Gap
The Post described the security chasm between Android and iOS as a "growing 'Surveillance Gap,'" stating, "Some civil libertarians have begun pointing out that the people on the safer side of that gap - with stronger protections against the potential for government abuse - are the relatively affluent people who already favor Apple products.
"Those willing to pay a premium for an iPhone or iPad, perhaps for their design elegance or ease of use, are also getting disk encryption by default, an instant messaging system that resists eavesdropping and an operating system that even powerful surveillance companies have trouble cracking."
The paper observed that "most shoppers likely think little about security when choosing their consumer electronics. Yet the consequences can be serious if a government anywhere in the world decides to target you with FinSpy, or if a police officer or border patrol agent attempts to browse through your smartphone -- or worse still, copy its entire contents for later examination."
Android is the favored platform of Al-Qaeda, making it obvious why government surveillance teams seek to target the platform. However, the ease in exploiting Android is also directly related to severe security lapses Google has made in designing its mobile platform.
Maintained by Google primarily a way to display its ads, Android is distributed via an "open" community alliance of competing hardware makers and mobile carriers that makes patching major problems across the Android installed base extremely challenging--and impossible for the hundreds of millions of Android users who don't access Google Play.
Spyware on Macs
The Post also noted that "just because Gamma Group has trouble getting FinSpy onto iPhones doesn't mean they are impregnable. Other surveillance companies may have better intrusion technology. Or an intelligence service could hack into the computer that syncs up with an iPhone."
Gamma also licenses its desktop spyware, which can target both Macs and Windows PCs, although other leaked documents show that its desktop software is limited to exploiting OS X via modules that spy on the shell, install a keylogger, share the screen or webcam or exploit Microsoft's Skype.
Under Microsoft's Windows, the company's software advertises broad powers to access, change or delete files, and supplies modules that handle forensic tools, keyloggers, and use the microphone, printer, scheduler, Skype, screen and webcam as well as VoIP.
The software is also regularly updated to avoid detection by malware scanners including Microsoft Security Essentials and Avast AntiVirus, as noted by NetworkWorld.
The leaked details were provided via a spoof account on Twitter sarcastically identifying itself as @GammaGroupPR. The leaked documents have been archived by privacy advocates including Wikileaks and German site netzpolitik.org.