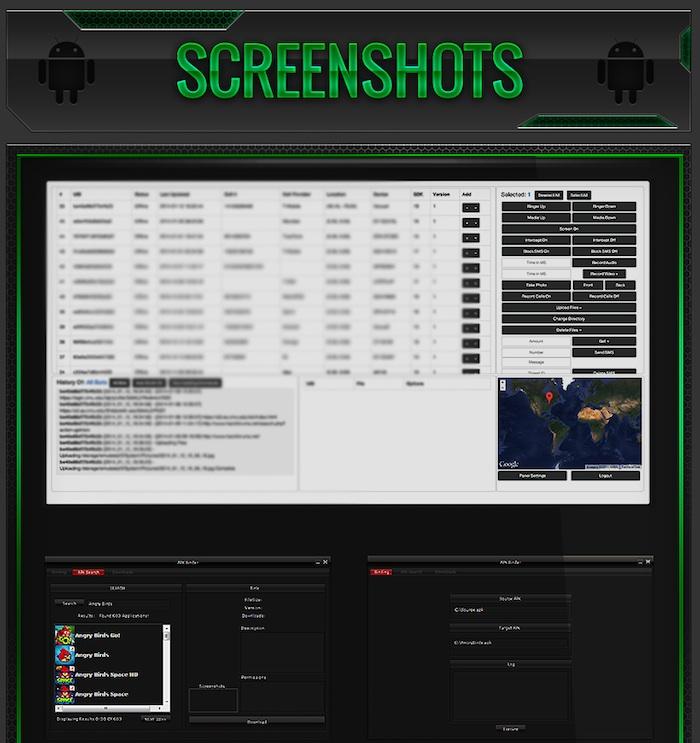
An easy to use new "Remote Administration Tool" malware package for Android offers to infect users, steal their photos and text messages, secretly capture audio or video, record their calls, download their web browser history and steal their email, Facebook and VPN account information.
The practice of selling such a malware package targeting Android is so common it has a pet name among security researchers: an "Android RAT," for Remote Administration Tool.
However, the latest RAT is raising eyebrows in the security community because of its low cost (just $300 for unlimited use, paid for via untraceable currencies such as Bitcoin) and its ability to sneak past Google's automated malware scanner in the Google Play app market, where legitimate appearing, RAT-infected apps can hide out undetected.
Dendroid infects Google Play, gnaws at user data
Known as Dendroid, the new Android RAT package is being sold as an "APK Binder," which can take any original or stolen Android app and incorporate its own malware as a Trojan payload. After distributing the infected app, Dendroid's RAT customers can monitor the spread of their infection via web based tools.
RAT infected Android devices can be remotely zombified by the perpetrator, allowing virtually unlimited access to photos, data and messages on the device. The Dendroid RAT provides full access to infected devices' camera and microphone, and can place calls or listen in on a user's phone conversations or text messages.
Distributing Dendroid is easy because, as a report by security firm Lookout stated, "it looks as if Dendroid was designed with evading Play Store security in mind."
The firm noted that, "Amongst its numerous features, Dendroid features some relatively simple — yet unusual — anti-emulation detection code that helps it evade detection by Bouncer, Google's anti-malware screening system for the play store."
Google's Bouncer scans for malware by emulating submitted apps to review their functionality for telltale, illegal behaviors. Dendroid-infected Android apps are designed to be smart enough to avoid executing their malware code while being run in emulation by Google's Bouncer scanning process.
Malware is Android's primary exclusive app
Most malware is incentivized by commercial activity, often by presenting ads or spreading spyware that can harvest valuable marketing data. In addition to these, Dendroid also offers to earn its keep as a tool for generating massive Denial of Service attacks across the population of its infected devices.
A report by Lucian Constantin for IT World cited Bogdan Botezatu, a senior e-threat analyst at Bitdefender as saying that "Dendroid is a much improved remote access tool that is definitely aimed for commercial purposes," adding that "Although it roughly does the same as Androrat [an older Android RAT], it appears to be much more stable and allows cybercriminal groups to better manage the pool of mobile bots." Android malware has pretty much followed in the footsteps of Windows malware
Constantin noted that "Android malware has pretty much followed in the footsteps of Windows malware," again citing Botezatu as stating that "Cybercrime is all about making easy money with minimum of effort. Creating a piece of malware that is stable, tested and does not crash the host device requires a lot of work and skill."
How to avoid Dendroid
Android users can adopt the same protections that Windows PC users did during the malware crisis that plagued Microsoft's platform ten years ago. That includes not installing apps from untrusted sources and installing third party malware scanner tools.
Over the past ten years however, a significant portion of Windows users have simply switched from the wide open, malware saturated Windows platform to Apple's Macs and iOS devices. Macs never became a significant malware target, an advantage Apple advertised and worked to preserve.
When it introduced iOS in 2007, Apple incorporated a new security model that attempted to destroy the low hanging fruit supporting the malware market on previous mobile devices.
Apple stated that it "designed the iOS platform with security at its core," detailing that, "when we set out to create the best possible mobile OS, we drew from decades of experience to build an entirely new architecture. We thought about the security hazards of the desktop environment, and established a new approach to security in the design of iOS. We developed and incorporated innovative features that tighten mobile security and protect the entire system by default. As a result, iOS is a major leap forward in OS security."
Apple has since brought many of these protections to its desktop Mac platform, from signed apps to a secure app market and regular free software updates that target and solve vulnerabilities faster than malware authors can build a business around them.
In stark contrast, Google simply recreated Microsoft's malware-harboring platform among mobile devices via Android, allowing third party developers to release "open" apps that can obtain inappropriate access to user content and data.
Google maintains no accountability for the devices that ship with Android, and most devices ship with outdated versions with known security vulnerabilities. Most of these will never receive security updates.
 Daniel Eran Dilger
Daniel Eran Dilger





-xl-m.jpg)


-m.jpg)






 Thomas Sibilly
Thomas Sibilly
 Wesley Hilliard
Wesley Hilliard
 Christine McKee
Christine McKee
 Amber Neely
Amber Neely
 William Gallagher
William Gallagher
 Malcolm Owen
Malcolm Owen

 Mike Wuerthele
Mike Wuerthele







186 Comments
yikes
Any stats on infection rates and geographic locations of those most at risk? No? I wonder why that could be.
The denial of service capabilities available to the RATs can affect anyone regardless of which platform they use. With the possibilities of millions or even billions of infected Android devices, no one is immune from their DDOS attacks.
An app that at least appeared to have Dendroid code actually made it into Google Play, It was caught before it had been downloaded more than 50 times according to ARS. There's attacks coming at us from all directions anymore. http://arstechnica.com/security/2014/03/malware-designed-to-take-over-cameras-and-record-audio-enters-google-play/
Troubling indeed.