Speaking at Mobile World Conference, Google's new Android chief Sundar Pichai admitted that security plays second fiddle to "freedom" in the design and implementation of Google's mobile operation system, exposing Android users to an overwhelming, disproportionate share of malware vulnerabilities.
Android's malware monopoly
Last month, a report by Cisco detailed that 99 percent of mobile malware targets Android, echoing the "staggering rate" of malware growth observed last summer by Juniper Networks in a report that noted that "77 percent of Android's threats could be largely eliminated today if all Android devices had the latest OS. Currently only 4 percent do."
When asked about Android's malware problems, Pichai (the Chrome OS executive who replaced Andy Rubin as the head of Google's Android development early last year) answered by saying that Android is not really "designed to be safe" but rather to provide "freedom."
His comments, reported by French site Frandroid.com translated: "We do not guarantee that Android is designed to be safe; its format was designed to give more freedom. When they talk about 90% of malicious programs for Android, they must of course take into account the fact that it is the most used operating system in the world. If I had a company dedicated to malware, I would also send my attacks to Android."
Android's problems due to a lack of security updates, not due to popularity
While creating an apparent comparison with the role of Microsoft's Windows on PCs over the previous decade, Pichai did not actually address the root cause of malware issues as highlighted by Juniper: the failure of Google and its partners to make security updates broadly available to the platform's users.
Last July, a U.S. Government report titled "Threats to Mobile Devices Using the Android OS" warned that Android "continues to be a primary target for malware attacks due to its market share and open source architecture," and stated that this "makes it more important than ever to keep mobile OS patched and up-to-date."
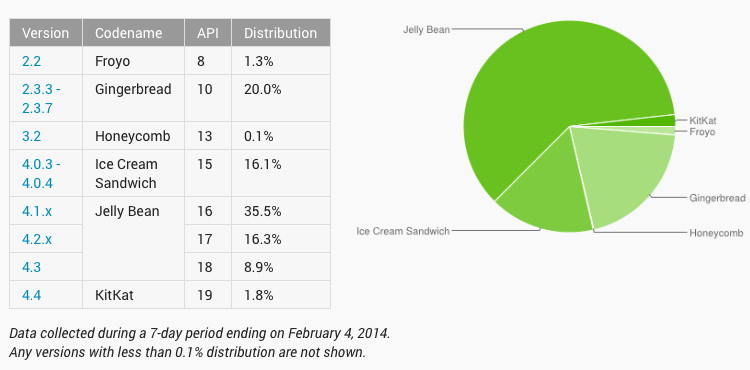
Yet months later, Google still reports that more than 20 percent of active Android users accessing Google Play are still using a "Gingerbread" or older edition of Android dating back to 2011 that, as the government's report noted, still "have a number of security vulnerabilities that were fixed in later versions."
While the Gingerbread figure has ostensibly improved over the past several months (Google also changed how it counts "active" users), the number of new exploits discovered in subsequent editions of Android has put the platform's security at even greater at risk. One recently reported flaw is serious enough to have prompted security researchers to publicly issue an exploit tool with the intention of forcing Google to fix the bug for its users.
So far, only 27 percent of Google's active Android users are running an Android version that addresses that particular flaw, leaving 73 percent of Android users vulnerable to the critical security flaw in Google's WebView that gives malicious users the freedom to remotely control users' devices.
Apple focuses on security as more important than "freedom"
For Apple's users, encountering an actual security flaw is rare enough to be deemed newsworthy. While only 1.8 percent of Google's users are on the latest KitKat version of Android, an overwhelming 82 percent of iOS users now have iOS 7 installed, even though both OS versions were released around the same time last fall.
Additionally, Apple continues to release easy to install, free updates addressing problems found not only in its latest iOS 7, but also for customers still using iOS 6. That, includes those who bought the original iPad back in 2010, a product released nearly a year before Google's still vulnerable, unpatched Android 2.3 Gingerbread was even announced.
Yesterday, Apple outlined its focus on security in iOS in a white paper providing more detail on Touch ID and the Secure Enclave processor core built into its A7 Application Processor. In addition to talking about hardware, Apple noted that it "designed the iOS platform with security at its core."
The document stated, "when we set out to create the best possible mobile OS, we drew from decades of experience to build an entirely new architecture. We thought about the security hazards of the desktop environment, and established a new approach to security in the design of iOS. We developed and incorporated innovative features that tighten mobile security and protect the entire system by default. As a result, iOS is a major leap forward in OS security."
Apple further noted that its design for iOS "protects not only the device and its data at rest, but the entire ecosystem, including everything users do locally, on networks, and with key Internet services." Nowhere in the document does Apple even use the word "freedom."
Among the topics that the document does detail is Secure Boot, which limits "freedom" by preventing the installation of older versions of iOS that contain known security vulnerabilities. But the feature also helps prevent thieves from being able to downgrade the software on a stolen device in order to expose and exploit any known, patched flaws and therefore bypass Apple's latest protections that secure users' data, messages and passwords.
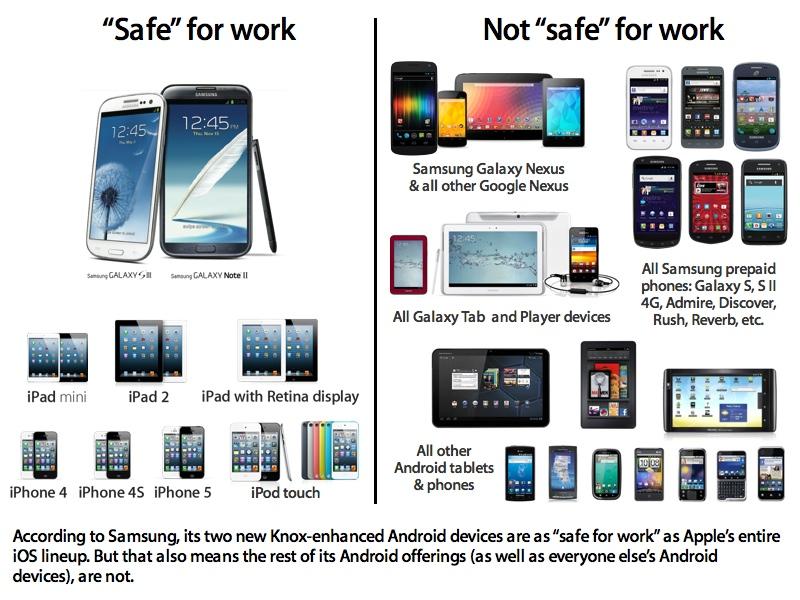
That's a real problem on Android, where a design focused on permissive freedom has also made securing the devices effectively impossible. Samsung has attempted to address this problem for corporate users with Knox, a layer designed to limit Android's freedom and therefore give it a layer of security closer to iOS. However, most of Samsung's smartphones don't even support Knox, rendering the majority of Android device shipments impossible to secure.
Apple benefitting from a differentiated focus on security
Apple's design of iOS "with security at its core" has resulted in an overwhelming advantage in the market. While IDC, Gartner and Strategy Analytics focus on global unit shipments, Apple's iOS share among enterprise, government and education users is dwarfing the adoption of Android.
Enterprise vendor Good Technology has consistently reported landslide iOS adoption rates, giving Apple 73 percent share among mobile devices and reporting that its iPad now makes up 91.4 percent of enterprise tablets. The scale of those numbers are resulting in iOS getting the vast majority of serious custom development among corporate users.
It's not just big firms, vast government agencies and entire school districts that are adopting iOS for security reasons. The results of a Clio study of mostly smaller law offices shows a definite trend toward iOS adoption over the last four years. Since 2010, Apple's share in mobile devices among these users has expanded 24 percentage points from 50 percent to 74 percent last year, while Android has only seen adoption climb 8 percentage points from 10 percent to 18 percent.
Among the same population of users, adoption of Macs as a "primary operating system" has also grown from 55 percent in 2010 to 66 percent last year, while the use of Windows has shrunk from 45 percent to just 34 percent over the same period.
While Google's Pichai drew a parallel between the ubiquitous availability of Android and Windows and the security issues each platform has faced as a result, he failed to address that it was Windows' permissive security problems, from invasive spyware to annoying ad popups, that helped fuel popular interest in Apple's original "Get A Mac" campaign, which helped to ignite the rapid growth in Mac sales over the past decade as users actively rejected a broadly open platform in favor of a secure one that "just worked."
In contrast, no amount of ideological evangelism about "freedom" has generated any real interest among corporations or individuals in Linux as a desktop or mobile platform. Linux primarily made inroads on servers because it was free. In failing to focus on security and leaving its users on their own, Google's Android's faces the prospect of suffering the same platform erosion that Windows suffered for the same reasons, while at the same time earning the same revenues as Linux.
 Daniel Eran Dilger
Daniel Eran Dilger








-m.jpg)






 Amber Neely
Amber Neely
 William Gallagher
William Gallagher
 Malcolm Owen
Malcolm Owen


 Andrew O'Hara
Andrew O'Hara
 Andrew Orr
Andrew Orr


-m.jpg)






84 Comments
I just can't waste time reading these puff pieces anymore. Next.
What no comments yet? Where are all those Android fanboys screaming about hack/cracks/shims & boot loaders? Oh yeah...the 99% malware option kicked in and now they need to restore their phones if they are even able to. It appears the Android/Google have given their customers the royal middle finger (again). Instead of patching every phone properly, they rely on a multi-level patch process that takes months to deploy effectively, so many handsets never get the updates they require, never mind complete Android system upgrades. Google is screaming "we're #1, we're #1" in malware infections. They should be screaming "we hate our customers". That would be more truthful.
I just can't waste time reading these puff pieces anymore. Next.
Why?
It's good to have some balance after all the crap about Apple patching the "glaring" goto flaw, which was never actively exploited by anyone conducting man in the middle attacks.
What no comments yet? Where are all those Android fanboys screaming about hack/cracks/shims & boot loaders?
Oh yeah...the 99% malware option kicked in and now they need to restore their phones if they are even able to.
It appears the Android/Google have given their customers the royal middle finger (again). Instead of patching every phone properly, they rely on a multi-level patch process that takes months to deploy effectively, so many handsets never get the updates they require, never mind complete Android system upgrades.
Google is screaming "we're #1, we're #1" in malware infections.
They should be screaming "we hate our customers". That would be more truthful.
Google love their customers, they make lots of money selling them information on their product users...
...oh, you confused Android users with Google's "customers", a common enough mistake.
Planning for security is great and having data that shows your system has more known malware is nice but the keyword is [I]known[/I]. Let's not forget this is coming awfully fast on the heels of an 18 month-long bug that would all all dumped data from iOS and Mac backups, syncing and Safari usage otherwise thought secure to be read by even a novice hacker. You wouldn't even need to target any Apple device because the data was being sent across the globe from device to server for a year-and-half. We will likely never know if any government was aware and expelling this data, or if anyone after the fact will start trawling though network packet dumps looking for personal information. I haven't even yet heard if Mac and iOS App Store apps also use Apple's SSL implementation. [quote name="SpamSandwich" url="/t/162211/apple-touts-secure-design-of-ios-as-google-chief-admits-android-is-best-target-for-malicious-hackers#post_2478979"]I just can't waste time reading these puff pieces anymore. Next.[/quote] I barely read most of the articles here. I come for the commenters. [quote name="RickFaced" url="/t/162211/apple-touts-secure-design-of-ios-as-google-chief-admits-android-is-best-target-for-malicious-hackers#post_2478993"]Samsung is not going to be happy about this article.[/quote] They can at least be comforted by having the only Android-based devices on the safe list.