An iOS security white paper published by Apple on Wednesday offers a deeper understanding of the company's Touch ID fingerprint sensing system and the so-called "Secure Enclave" found in the A7 SoC, both of which were introduced with the iPhone 5s.
The security document (PDF link) details a number of iOS hardware and software security protocols, including new information outlining how Touch ID and the Secure Enclave work together to keep user data safe. First spotted by TechCrunch, the white paper was published to Apple's "iPhone in Business" website.
According to the paper, the A7's Secure Enclave is actually a coprocessor built into Apple's latest system-on-a-chip design. With a secure boot sequence and software update mechanism separate from the application processor, the component is responsible for "all cryptographic operations for Data Protection key management and maintains the integrity of Data Protection even if the kernel has been compromised."
Each Secure Enclave is provisioned during fabrication with its own UID (Unique ID) that is not accessible to other parts of the system and is not known to Apple. When the device starts up, an ephemeral key is created, tangled with its UID, and used to encrypt the Secure Enclave's portion of the device's memory space.Additionally, data that is saved to the file system by the Secure Enclave is encrypted with a key tangled with the UID and an anti-replay counter.
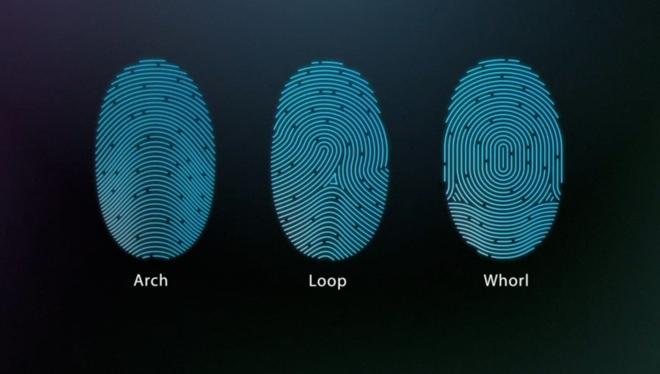
As for Touch ID, Apple notes the iPhone 5s-only technology reads fingerprints from any angle and continuously "learns" a user's fingerprint over time. The paper explains that the sensor expands the stored fingerprint map with each consecutive use by adding newly identified overlapping nodes.
When a user's finger contacts the capacitive steel ring surrounding the home button, the Touch ID sensor performs an 88-by-88-pixel, 500-ppi raster scan that is "temporarily stored in encrypted memory within the Secure Enclave while being vectorized for analysis." The system is sensitive enough that the chance of a random match for one finger is 1 in 50,000.
Once processing and analysis is complete, the data is discarded and is never sent to iCloud, iTunes or Apple.
Explaining how the two technologies work together, Apple says data from the Touch ID module is transferred to the A7 chip via a peripheral interface bus and is subsequently forwarded to the Secure Enclave for decryption.
The application processor cannot read the raw Touch ID data, however, as it is encrypted and protected with a unique session key generated based on a shared key built into the fingerprint sensor and Secure Enclave. Session key exchange uses advanced encryption standard (AES) key wrapping on both ends and AES-CCM transport encryption to provide randomized key generation and enhanced protection.
Unlocking the iPhone 5s is a slightly different process, but uses the same shared secret and data protection key mechanisms:
On iPhone 5s with Touch ID turned on, the keys are not discarded when the device locks; instead, they're wrapped with a key that is given to the Touch ID subsystem. When a user attempts to unlock the device, if Touch ID recognizes the user's fingerprint, it provides the key for unwrapping the Data Protection keys and the device is unlocked. This process provides additional protection by requiring the Data Protection and Touch ID subsystems to cooperate in order to unlock the device.
Decryption keys are stored in memory, meaning the data will be deleted if a device is rebooted. This explains why users must re-enter their password when purchasing an item from the App Store or iTunes. Adding further protection, the Secure Enclave jettisons these keys after 48 hours or five failed Touch ID attempts.
Describing a Touch ID use case in purchasing digital content, Apple explains:
When users choose to authorize a purchase, authentication tokens are exchanged between the device and store. The token and nonce are held in the Secure Enclave. The nonce is signed with a Secure Enclave key shared by all devices and the iTunes Store.
Apple previously detailed a similar shared secret method of authentication in a patent filing pertaining to retail purchases.
The remainder of the white paper focuses on overall iOS security protocols with special attention given to app security layers.
 Mikey Campbell
Mikey Campbell






-m.jpg)






 Malcolm Owen
Malcolm Owen
 Amber Neely
Amber Neely
 William Gallagher
William Gallagher


 Oliver Haslam
Oliver Haslam
 Thomas Sibilly
Thomas Sibilly
-m.jpg)






47 Comments
[quote name="AppleInsider" url="/t/162199/apple-details-touch-id-and-secure-enclave-tech-in-new-security-white-paper#post_2478352"]With a secure boot sequence and software update mechanism separat from the application processor...[/quote] I'm glad it is separat! Keeps hot food hot and cold foods cold. ;)
Coincidence this white paper of a clearly superiour solution has come out right after Samsung introduces their S5 with a fingerprint sensor?
I must say that a lot of thought went into this, it's a very well executed security measure. As it is described in the article I wouldn't say it's unhackable but it certainly is VERY difficult (actually the use of AES which is not without its flaws might be the biggest issue). But I think it's safe to say that the fingerprint fooling 'hack' is a lot easier than the software/hardware hack. Which says a lot.
[quote name="Chipsy" url="/t/162199/apple-details-touch-id-and-secure-enclave-tech-in-new-security-white-paper#post_2478371"]I must say that a lot of thought went into this, it's a very well executed security measure. As it is described in the article I wouldn't say it's unhackable but it certainly is VERY difficult (actually the use of AES which is not without its flaws might be the biggest issue). But I think it's safe to say that the fingerprint fooling 'hack' is a lot easier than the software/hardware hack. Which says a lot. [/quote] I'm sure Apple is aware of the limitations. I think their short-term intention was to get people who normally never use a 4-digit PIN to secure their device to have some security. I think this nails it in one of the few examples of increased security actually being more of a convenience than the previous method. I've even enabled the complex passcode option so I get the full keyboard when I restart my iPhone 5S. And even if one doesn't want to go that route but would instead just use the dial pad with a longer (or shorter) PIN they can do that too by enabling the complex passcode option. Previously, when you enabled that option and only used numbers you would still get the QWERTY keyboard on screen.
Coincidence this white paper of a clearly superiour solution has come out right after Samsung introduces their S5 with a fingerprint sensor?
I posed the question about how Samsung plans to secure the fingerprint data on this site yesterday, and I've seen similar questions popping up on other articles about the Galaxy S5. Samsung has made a big deal out of having their fingerprint reader available to third party apps, including an announced alliance with PayPal. But, they have not made any details available concerning security. Features like showing the fingerprint scan on-screen as you swipe might add flashiness, but it certainly doesn't give me any confidence in how well Samsung might have secured the fingerprint data.
The iOS security paper does a good job of explaining the steps that Apple has taken to secure the fingerprint data using Secure Enclave. It burnishes Apple's message that it takes fingerprint data security seriously, and muddies the waters a bit over what security shortcuts Samsung might be taking in filling out its feature checklist.
But, I think the timing of the paper (which was actually dated February 14) is actually more in line with the iOS 7.0.6 release, and the fallout from the SSL vulnerability. TechCrunch spotted it today, but who knows when Apple actually posted the paper to their website.