A recently discovered AirTag weakness allows would-be attackers to redirect users to a malicious webpage when the device is scanned in Lost Mode, effectively turning the tracker into a Trojan horse.
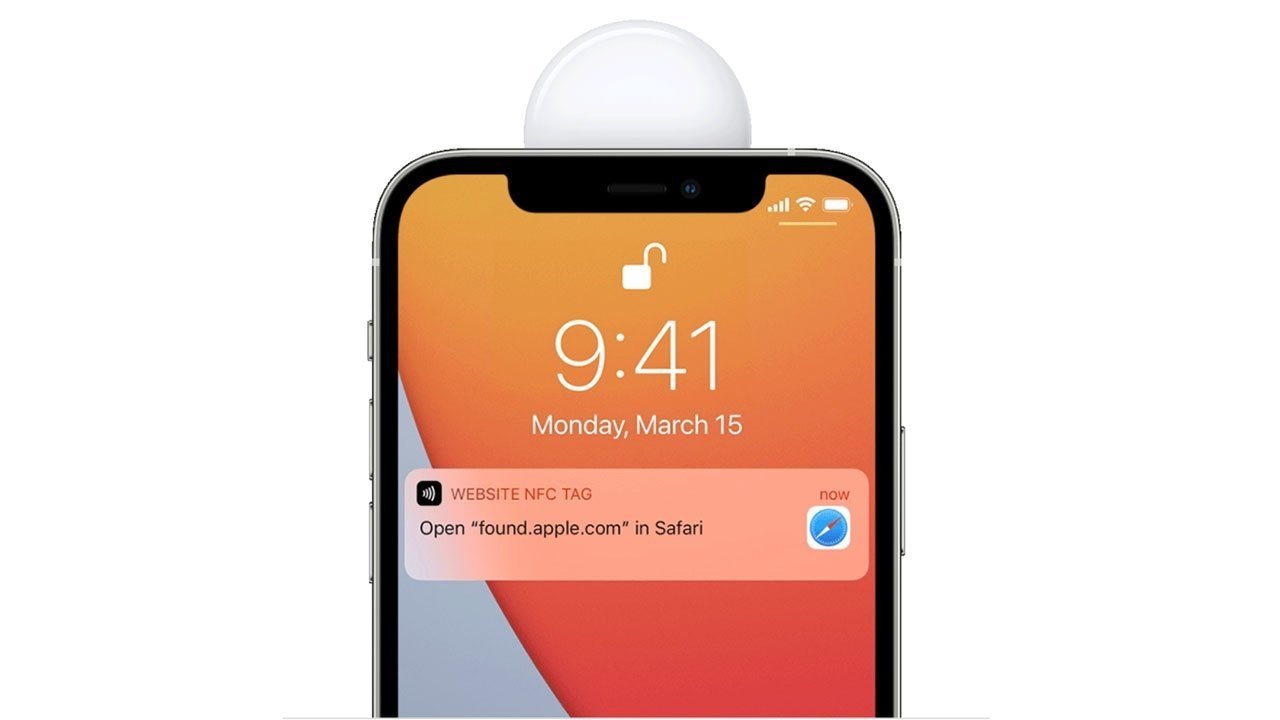
Lost Mode is a tentpole AirTag capability that, when activated, allows anyone with an NFC-capable device to scan the tracker and read a programmed discovery message that can include an owner's phone number. The feature assists in the return of lost items like car keys if the Find My network fails to locate a lost AirTag.
Researcher Bobby Rauch has uncovered a vulnerability that turns Lost Mode into a potential attack vector.
As outlined by Krebs on Security, Lost Mode generates a unique URL at https://found.apple.com, where owners can enter a personal message and phone number should the device be found. Rauch discovered that Apple's systems do not prevent injection of arbitrary code into the phone number field, meaning unsuspecting good Samaritans who scan the device can be sent to a malicious website.
"I can't remember another instance where these sort of small consumer-grade tracking devices at a low cost like this could be weaponized," Rauch said.
In a Medium post published today, Rauch explains that a Stored XSS exploit can be carried out to inject a malicious payload that redirects to a phishing site that gleans sensitive credentials using a keylogger. Other XSS exploits like session token hijacking and clickjacking can also be deployed, Rauch says.
The researcher informed Apple about the vulnerability on June 20 and said he planned to make the information public in 90 days, as per typical disclosure protocols. He received little information since then beyond statements saying that the company is still investigating the flaw. Apple failed to answer questions about progress on a solution and did not say whether Rauch would be credited in a future security advisory, the report said. The company also did not comment on whether the flaw was eligible for a payout through Apple's Bug Bounty Program.
Last Thursday, five days after the 90-day disclosure protection window expired, Apple contacted Rauch to say that the weakness will be addressed in an upcoming update and asked that he not talk about the bug publicly.
"I told them, I'm willing to work with you if you can provide some details of when you plan on remediating this, and whether there would be any recognition or bug bounty payout'," Rauch said. "Their response was basically, We'd appreciate it if you didn't leak this.'"
Rauch went public to protest Apple's lack of communication, the report said.
A number of other researchers have aired frustrations about Apple's bug reporting program, including security researcher Denis Tokarev. Last week, Tokarev detailed his experience with the Bug Bounty Program, saying he identified and reported four flaws to Apple, but only one has been patched. Apple later apologized for the delay and said it is still investigating the issues.
AirTag has been an area of interest for the security research community since its launch in April. Shortly after the device debuted, researchers found a method by which AirTag can be leveraged to send short messages through the Find My network.
