Unsurprisingly, Miller was able to use his exploit to immediately win the event's "Pwn2Own" contest, generating headlines that suggested that Macs are inherently less secure, despite the fact that every browser involved in the contest failed on the first day.
This year's contest arranged for two test computers. According to the CanSecWest event's official website, which is oddly littered with typos, the "Browsers and Associated Text PAltform" [sic] were a Sony Vaio PC running a prerelease Windows 7 beta with Internet Explorer 8, Firefox, and Google's new Chrome browser, and a MacBook running Safari and Firefox.
In each of the three days of the contest, the exploit rules were intended to be progressively relaxed, starting only with exploits that attacked the browser itself, then adding Flash, Java, .Net and QuickTime to the mix on day two, and then "popular apps such as Acrobat Reader" on the third day.
Finding vulnerabilities
The Pwn2Own contest is being presented as a shootout between Mac and Windows browsers. Last year's contest also included Linux, but attendees with the ability to crack Linux "didn’t want to put the work into developing the exploit code that would be required to win the contest," according to a report by IDG.
That fact highlights that, in reality, the platforms and browsers involved aren't targeted by a series of equal attacks. Instead, researchers arrive with exploits they hope to use against vulnerabilities they are aware of in specific platforms or browsers, but have not yet reported. Were they to report the exploits in advance, they would be patched by the vendor. There's no money in that, so the contest provides an incentive to report vulnerabilities.
In exchange for the winning prize, Miller granted the reporting rights to the discovered flaw in Safari to TippingPoint’s Zero Day Initiative, which will coordinate the handling of the disclosure and the patch release process with Apple. When a vulnerability is reported to Apple, the company credits the discoverer with finding the problem when issuing a patch for it.
Last year, Miller's winning attack on Safari actually targeted the open source Perl Compatible Regular Expressions library used by WebKit’s JavaScript engine, an exploit he also made headlines with for using against the iPhone. Apple's extensive use of open source software makes it far easier for researchers to discover exploits for at their leisure, compared to closed proprietary software. It wasn't Apple's proprietary code in Safari that was cracked.
At the same time, proprietary, closed code isn't invulnerable due to its opaque "security through obscurity." Windows Vista was cracked in last year's contest due to a flaw in the Adobe Flash plugin, which is not open source but which security experts were still able to exploit.
Patching vulnerabilities
At the same time, Apple's use of open source also enables the company to issues more security patches and operating system updates than Microsoft does, according to a study of Windows and Mac OS X releases conducted by the Swiss Federal Institute of Technology.
That group found that in the years between 2002 and 2007, Apple released 815 patches compared to 678 by Microsoft. In that timeframe, Apple shipped five paid reference releases of Mac OS X (Jaguar, Panther, Tiger, Tiger for Intel, and Leopard) and 33 free updates, including eight for Jaguar, nine for Panther, eleven for Tiger, and one for Leopard, a total of 38 significant feature and security releases, excluding Mac OS X Server, the iPhone, and standalone security patches.
In contrast, Microsoft only released a total of seven updates over that period, including Windows XP SP1 and SP2; Windows Server 2003, SP1, R2, and SP2; and Windows Vista. In the year since, Microsoft has released two service packs for Vista and one for XP. Apple has released five additional free updates for Leopard, again not counting Mac OS X Server patches or iPhone updates.
"Simplifying security to the point of uselessness"
The oversimplification of the Pwn2Own contest's results by the media has resulted in criticism of how the contest is portrayed and conducted. The Pwn2Own contest is "simplifying security to the point of uselessness," according to comments by Jeff Jones, the director of Microsoft's security group.
Last year, Jones addressed CanSecWest in a blog post which stated, "I don't really care for 'hack the box' contests. If a machine doesn't get hacked, it does not mean it isn't breakable. If it does get hacked, it just shows us what we already know - any machine can be broken under the right circumstances. So, don't read too much into the PWN 2 OWN results. I don't."
Last year's contest was also distorted by the arbitrary timing of patches, with Miller's successful exploit for Safari happening to miss Apple's patch cycle, while other researchers armed with exploits for Windows Vista were stymied by the last minute application of the then-new Vista Service Pack 1.
The contest is also somewhat removed from reality due to the fact that it pits the current release of Mac OS X with new versions of Windows that do not reflect what the vast majority of Windows PC users are actually running. Last year, Vista was only in use by a small fraction of early adopters (and even now, less than a quarter of the installed base is using it), and SP1 was so new and problematic that PC World was advising users not to install it until "the wrinkles are ironed out."
This year, the use of the prerelease Windows 7 operating system, which security researchers have had limited access and time to study, combined with the fact that Microsoft expressly warns users not to use it in production environments, tends to create the impression that Pwn2Own is more about theoretical games than real world security issues relevant to end users.
Security in the real world
The real world security problems that affect today's Windows users relate to the fact that there are not only more discovered flaws on Windows, but that these flaws are being actively exploited to develop viruses, spyware, adware, and other malware. Further, there are vast numbers of machines that are not promptly updated with the patches that do exist, resulting in fleets of vulnerable botnets that actively distribute new attacks to other systems. These two problems aggravate each other to create the Windows security crisis.
While pundits like to talk about numbers of discovered vulnerabilities, often failing to correctly compare similar code on each side (with Mac OS X inheriting the vulnerability counts in optional open source server programs, Java, and other components that are not considered on the Windows side), the real problem is active exploits. Mac OS X continues to have no real viruses, while Windows users continue to be plagued by viruses, adware, and other security problems.
At the same time however, the tech media is promoting the CanSecWest event as a "security shootout," with at least one report noting that browsers on the Windows box were "still standing" after Miller successfully applied his exploit attack to the Mac, as if the Windows box had somehow successfully dodged Miller's exploit rather than simply never having been aimed at by his open source attack.
Internet Explorer 8 on the Windows machine was exploited shortly afterward by a different researcher calling himself Nil, followed by his demonstration of a successful crack of the Firefox browser.
 Prince McLean
Prince McLean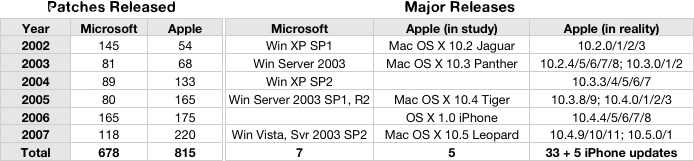







-m.jpg)






 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Thomas Sibilly
Thomas Sibilly
 Wesley Hilliard
Wesley Hilliard
 Marko Zivkovic
Marko Zivkovic












81 Comments
Once again, Miller needed actual access to the machine through admin privileges, just like last year. Nothing to see here, move along.
Once again, Miller needed actual access to the machine through admin privileges, just like last year. Nothing to see here, move along.
Don't be so fast to shrug it off. Users need stories like this as a reality check: Your computer isn't safe from your other personality.
Don't be so fast to shrug it off. Users need stories like this as a reality check: Your computer isn't safe from your other personality.
How is it a feat when you need admin privileges to do anything? Why is it that CanSecWest never advertise this bit much, nor that people spend months preparing their "exploits" that do nothing on day 1, which is real world tests anyway...
That's it, the internet cannot be trusted. Call Al Gore, tell him to turn it off.
How is it a feat when you need admin privileges to do anything? Why is it that CanSecWest never advertise this bit much, nor that people spend months preparing their "exploits" that do nothing on day 1, which is real world tests anyway...
It's not a feat. Hence the laughing smiley and the loose Jekyll and Hyde reference. Worrying about turning into an evil hacking monster when you're logged into your admin account is silly, just like tests that normally succeed.