In a bold move — or an egregious error — Apple has left the kernel of its recently released iOS 10 beta exposed, laying bare potentially exploitable security flaws ahead of a wide public release this fall.
Discovered by security researchers and reported by the MIT Technology Review, the decision to distribute an unencrypted kernel would be a vast departure from previous iOS releases, which kept the so-called "heart" of the OS closely guarded. Among the many benefits of obscuring access to the kernel is protection from reverse engineering, a key security breaches.
Like many modern computer operating systems, the kernel in iOS is vital to system management, having a hand in almost every facet of runtime operations, from startup to high-level app execution. Importantly, the iOS kernel grants third-party apps access to, and limits use of, hardware assets. By delivering an unencrypted version, Apple is opening its prized OS to the scrutiny of security researchers and hackers alike.
Whether Apple deliberately left the kernel exposed is unclear, though experts find it hard to believe the move was made in error. More plausible, some say, is that Apple intentionally shipped an unencrypted beta version as part of a daring debugging strategy. More eyes on iOS code could result in higher rates of bug and vulnerability discoveries, which might — hopefully — be reported to Apple and fixed.
The method is a risky one, however, as researcher Mathew Solnik discovered the release to include a security measure that protects Apple's kernel from modification. Access to such information could potentially pose a danger to millions of iOS devices if it fell into the wrong hands.
Noted iOS security expert Jonathan Zdziarski said a decision to open the kernel makes sense coming out of Apple's recent data privacy battle with the U.S. government. In that case, the FBI pressed for access to an iPhone 5c linked to last year's San Bernardino terror attack, a request that would force Apple to create a workaround to its own security safeguards. Apple resisted an issued court order to unlock the iPhone, subsequently staging a legal defensive that sparked intense debate over the boundaries between government reach and personal data privacy.
The action was rendered moot after the FBI was able to bypass the handset's lock protection using a zero-day exploit purchased from an undisclosed third party. According to Zdziarski, an open iOS kernel might be an attempt at deflating the iOS exploit market, an entity in large part driven by demand from law enforcement agencies.
 Mikey Campbell
Mikey Campbell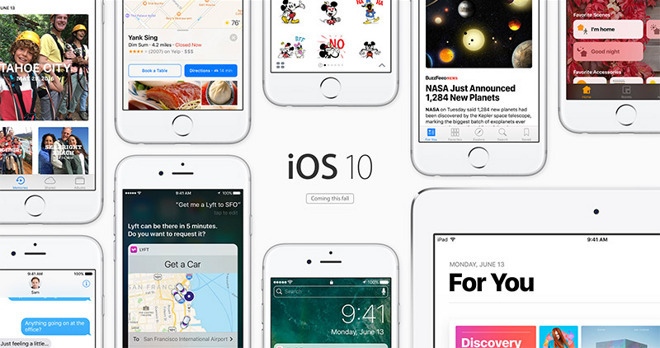







-m.jpg)






 Andrew Orr
Andrew Orr
 Amber Neely
Amber Neely
 Marko Zivkovic
Marko Zivkovic
 William Gallagher and Mike Wuerthele
William Gallagher and Mike Wuerthele


 Mike Wuerthele
Mike Wuerthele








21 Comments
Oops. Maybe we will be getting a new beta quicker than expected.
Uh-oh. Betcha Google is gonna be interested.
This is why you don't put beta software on your production devices.