Researchers in a pair of reports that surfaced this week claim to have successfully bypassed Apple's Activation Lock security feature using a heretofore unknown bug, potentially leaving iPad and iPhone devices open to attack.
Security researcher Hemanth Joseph was first to document the vulnerability in November, saying he stumbled across the bug while trying to bypass Activation Lock on an iPad he purchased from eBay. In short, Joseph discovered a method of crashing the security software layer by entering an excessively long string of characters in iPad's Wi-Fi setup text fields.
Activation Lock was designed and deployed with iOS 7 to prevent thieves or other unauthorized users from accessing a stolen or lost iOS device. Enabled automatically when Find My iPhone is activated, the system stores an owner's Apple ID on an offsite activation server for later verification.
Once enabled, any user wishing to gain device access, turn off Find My iPhone, erase the device or reactivate it must input the correct credentials. Since the deactivation process cross-checks Apple ID and password information with Apple's servers, an internet connection must first be established. This is where Joseph discovered a workaround of sorts.
When a locked device is turned on, iOS will prompt a user to connect to a nearby Wi-Fi network. Joseph was able to create an overflow error in the Activation Lock layer by selecting "Other Network" and entering a long string of text in the "Name," "Username" and "Password" fields, each of which contains no character limit.
A single overflow error, which freezes iOS, is apparently not enough to bypass Activation Lock. However, Joseph was able to crash the security app layer completely by closing and opening iPad's Smart Cover, which in turn granted him access to the device home screen.
Apple remedied Joseph's Activation Lock bypass with the release of iOS 10.1.1 in October, but SecurityWeek reports researchers at Vulnerability Labs were able to recreate the exploit using iOS screen rotation and Night Shift mode.
In the proof of concept video above, the bypass variant only allows home screen access for a brief moment, but Vulnerability Labs founder Benjamin Kunz-Mejri said that time window can be extended by quickly pressing the power button. Further, Kunz-Mejri claims the Activation Lock workaround also works on iPhone.
Whether Apple is aware of the bypass and subsequently closed the security hole in its upcoming iOS 10.2 release is unknown at this time.
 Mikey Campbell
Mikey Campbell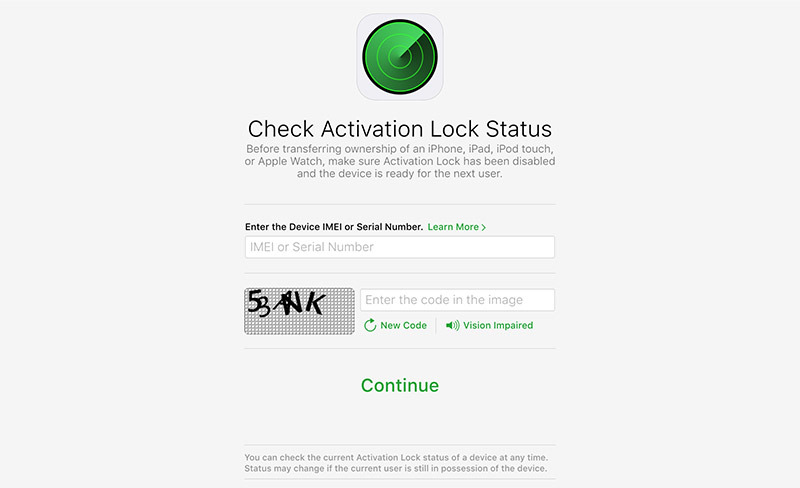




-xl-m.jpg)


-m.jpg)





 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher

 Amber Neely
Amber Neely
 Andrew Orr
Andrew Orr









12 Comments
On the face of it, the ability to use an excessively long sequence of text characters to break into a device seems absurd. How does a bug like this even exist in the first place, let alone not get caught?
Worrisome, it seems Apple doesn't address basic software security practices and also doesn't check its code.
There is always a hole somewhere, it's just a matter of finding them AND determining impact. What the article doesn't make clear, is what is the impact of this hole? Is your personal information at risk? Or, it is that a thief will be able to re-use your device after he steals it? Activation lock has reduced iOS device theft, and this appears to suggest that the impact here is not to your personal data, but to your stolen device being of some value because it can be setup again. Not great, but not putting your personal information at risk.
Part of this vulnerability has already been fixed. The second part says it only gives access to the home screen for a brief moment, even with repeated pressing of the power button, so what can someone do with brief access? Probably nothing. It's almost like the number keys showing up as TouchID is delayed finishing its logon process.
As far as Apple not finding this, give me a break. None of you complainers are programmers or you'd understand it is nearly impossible to find and test every possible action of software. The fact this is all they got demonstrates how well Apple programmers are doing, not the other way around.
@sog35 Get a life.
Still a million times more secure than Android so what ya gonna do? Buy a Windows phone?