A new strain of malware targeting Mac users is attempting to slip past defenses through a phishing scheme and a signed Apple developer certificate — though in practice, it may still not pose much of a threat.
The code, dubbed "Dok" by security firm Check Point, is said to affect "all versions" of macOS/OS X, and be the first "major scale" malware directed at Mac owners through a "coordinated email phishing campaign." The emails are aimed mostly at Europeans, one example being a German-language message from a supposed Swiss official, claiming problems with the target's tax return.
While Dok's signed certificate allows it to bypass Apple's Gatekeeper, infection is unlikely because victims must not only choose to download an attachment but enter their root password twice during the installation process, for instance after a fake OS X update window pops up asking users to install a security fix.
People who do fall prey, however, will find all of their communications vulnerable to intercept by the responsible hacker(s), even over SSL.
Macs are generally assaulted by malware less frequently than Windows, but incidents have been on the rise as Macs gain in popularity. In recent months a slew of attacks have been reported, some of them with prominent targets, like biomedical research, the defense industry, and human rights advocates.
To help counter threats, Apple has launched a bug bounty program similar to ones at other high-tech firms like Google. Security experts can potentially earn as much as $200,000 for exposing vulnerabilities in the company's code.
 Roger Fingas
Roger Fingas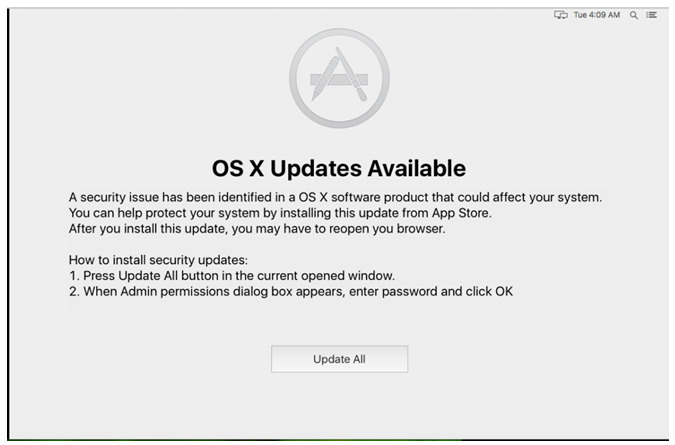


 William Gallagher
William Gallagher
 Amber Neely
Amber Neely
 Oliver Haslam
Oliver Haslam
 Thomas Sibilly
Thomas Sibilly
 Marko Zivkovic
Marko Zivkovic

 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen


-m.jpg)






4 Comments
"While Dok's signed certificate allows it to bypass Apple's Gatekeeper"
So based on this, it's a developer certificate, and since this is now publicized, will be revoked by Apple before the day is out, rendering this so-called "virus" inert.
Another non-story, move along.
What happens if you have a revoked certificate for that app but you have set Gatekeeper to allow apps downloaded from anywhere? Will it warn you? Will it prevent it from running even though it's sort of allowed?