Jeremiah Grossman revealed on his blog this week that users who have the "AutoFill web forms" feature enabled on Safari versions 4 and 5 is vulnerable to malicious code. The AutoFill feature is enabled by default in Apple's Web browser.
The feature automatically fills online text forms that have specific, common names, such as "name," "company," "city," "state," "e-mail," and more. The information is automatically grabbed from the user's personal record included in the operating systems' address book. That means the information could be obtained without the user even entering it into the Safari browser.
"All a malicious website would have to do to surreptitiously extract Address Book card data from Safari is dynamically create form text fields with the aforementioned names, probably invisibly, and then simulate A-Z keystroke events using JavaScript," Grossman wrote. "When data is populated, that is AutoFill'ed, it can be accessed and sent to the attacker."
He also created a proof-of-concept to show how it takes "mere seconds" to obtain the personal information. Grossman said the data could be used to send e-mail spam or conduct a phishing attack.
"Fortunately any AutoFill data starting with a number, such as phone numbers or street addresses, could not be obtained because for some reason the data would not populate in the text field," he said. "Still, such attacks could be easily and cheaply distributed on a mass scale using an advertising network where likely no one would ever notice because it's not exploit code designed to deliver rootkit payload."
Safari 5, the latest version of Apple's Web browser, was released in June. It added extensions and expanded HTML5 support for the desktop software.
 Slash Lane
Slash Lane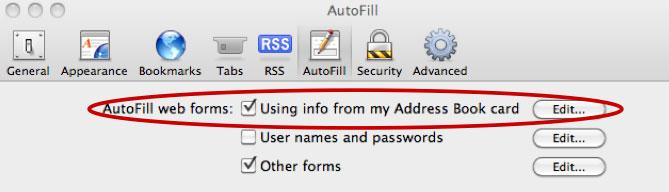








 Charles Martin
Charles Martin
 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher

 Christine McKee
Christine McKee
 Wesley Hilliard
Wesley Hilliard

 Andrew Orr
Andrew Orr








27 Comments
The autofill feature found in Apple's Safari Web browser could be used by a hacker to illegally obtain a user's personal information, including their name and e-mail address, a security researcher has discovered.
Yikes that is a bad one. I unchecked it right now.
I've always made sure that these two are unchecked.
I will be interested to hear the Apple response to this. I find it almost too obvious to be plausible. What malicious code has been proven to access this so far? I did disable it though
Tested this, is confirmed (and scary). Luckily I switched over from Firefox+Safari to Chrome+Firefox a while ago. It does not seem to work on either of those 2 (I have autofill off on both though).
It would take about 30 seconds of so to find out your name, email, address, which means a video site or a long article site would be the best place for this to wok.
I will be interested to hear the Apple response to this. I find it almost too obvious to be plausible. What malicious code has been proven to access this so far? I did disable it though
Yep. Javascript and Ajax, the savior of the of the web.
I just tested the fields that have numbers. When you start the phone with a "(" it does give you a drop down list presumably using Javascript. So if you could figure out the innerHTML being used, one might be able to get that info as well. Same thing with the address field. You get a drop down select list.
I have to do some more testing. I'm curious whether SSL prevents it, but signed certificates would at least be more trustworthy.