A unaddressed bug in Apple's Mac OS X discovered five months ago allows nefarious hackers to bypass the usual authentication measures by tweaking specific clock and user timestamp settings, granting near unlimited access to a computer's files.
While the security flaw has been around for nearly half a year, a new module created by developers of testing software Metasploit makes it easier to exploit the vulnerability in Macs, renewing interest in the issue, reports ArsTechnica.
The bug revolves around a Unix program called sudo, which allows or disallows users operational access based on privilege levels. Top tier privileges grant access to files belonging to other users' files, though that level of control is password protected.
Instead of inputting a password, the flaw works around authentication by setting a computer's clock to Jan. 1, 1970, or what is referred to as the Unix epoch. Unix time starts at zero hours on this date and is the basis for calculations. By resetting a Mac's clock, as well as the sudo user timestamp, to epoch, time restrictions and privilege limitations can be bypassed.
"The bug is significant because it allows any user-level compromise to become root, which in turn exposes things like clear-text passwords from Keychain and makes it possible for the intruder to install a permanent rootkit," said H.D. Moore, founder of the open-source Metasploit and chief research officer at security firm Rapid7.
Macs are especially vulnerable to the bug as OS X does not require a password to change these clock settings. As a result, all versions of the operating system from OS X 10.7 to the current 10.8.4 are affected. The same problem exists in Linux builds, but many of those iterations password protect clock changes.
While powerful, the bypass method has limitations. In order to implement changes, an attacker must already be logged in to a Mac with administrator privileges and have run sudo at least once before. As noted by the National Vulnerability Database, the person attempting to gain unauthorized privileges must also have physical or remote access to the target computer.
Apple has yet to respond or issue a patch for the bug.
"I believe Apple should take this more seriously but am not surprised with the slow response given their history of responding to vulnerabilities in the open source tools they package," Moore said.
 AppleInsider Staff
AppleInsider Staff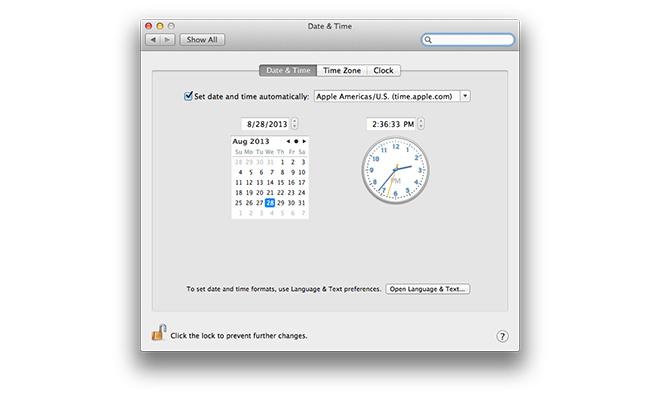







-m.jpg)






 Marko Zivkovic
Marko Zivkovic
 Christine McKee
Christine McKee
 Andrew Orr
Andrew Orr
 Andrew O'Hara
Andrew O'Hara
 William Gallagher
William Gallagher

 Mike Wuerthele
Mike Wuerthele
 Bon Adamson
Bon Adamson




-m.jpg)



70 Comments
It was discovered 5 months ago and apple hasn't fixed this yet? How is that possible? I would think they would want to be on top of the security there.
[quote name="AppleInsider" url="/t/159254/old-unpatched-os-x-security-flaw-can-give-attackers-root-access-to-] In order to implement changes, an attacker must already be logged in to a Mac with administrator privileges and have run sudo at least once before. As noted by the National Vulnerability Database, the person attempting to gain unauthorized privileges must also have physical or remote access to the target computer. [/quote] Dude, that's a pretty high bar. I think the ho-hum response from Apple is pretty reasonable.
Ok, it's a bug, but it's hardly a major security concern if the hacker has to already have administrator access to my computer, either physically or remotely, to do it! So what product is Metasploit trying to sell with this fear-mongering?
Requires admin access and at least one prior sudo plus physical access or remote access. So not something you can randomly do to someone. Aka FUD
So what product is Metasploit trying to sell with this fear-mongering?
Their penetration testing software.