Apple on Friday sought to calm OS X users who feared their computers may be at risk from a widespread vulnerability in popular UNIX command interpreter bash — which is included in Apple's UNIX-based desktop operating system — saying that most consumers are not at risk, while advanced users will receive a patch in the coming days.
"The vast majority of OS X users are not at risk to recently reported bash vulnerabilities," an Apple spokesperson said in a statement to iMore. "With OS X, systems are safe by default and not exposed to remote exploits of bash unless users configure advanced UNIX services," the spokesperson added, before noting that Apple is "working to quickly provide a software update for our advanced UNIX users."
The bug, nicknamed "shellshock" by members of the computer security community, is thought to be present in every version of bash since its introduction in 1989. By passing specially-crafted commands to computers running vulnerable releases of bash, an attacker could — without authentication — Â remotely execute arbitrary commands that could modify systems or exfiltrate data.
Because bash is present on nearly every Linux and UNIX system that has shipped in last 20 years, the potential for damage is immense if machines are not quickly patched. Fortunately for most OS X users, their computers are rarely directly exposed to the internet, and even more rarely are they configured to expose potentially vulnerable endpoints — like HTTP servers — Â to the network.
Advanced users who have OS X machines in a situation where they may be remotely exploited, such as systems administrators with internet-facing OS X servers, can mitigate the issue by recompiling bash with the official patches from GNU until Apple issues its own update.
 AppleInsider Staff
AppleInsider Staff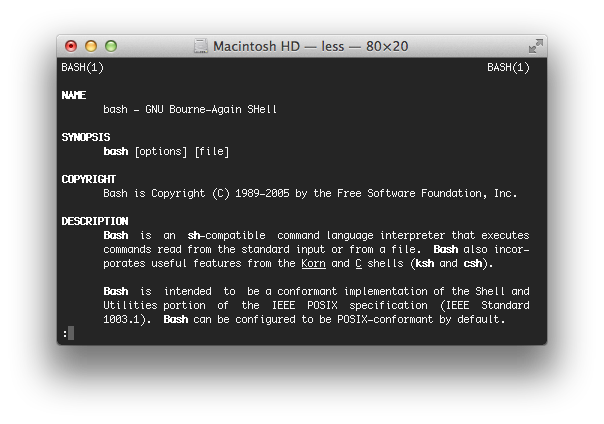


 William Gallagher
William Gallagher
 Andrew O'Hara
Andrew O'Hara
 Wesley Hilliard
Wesley Hilliard

 Malcolm Owen
Malcolm Owen
 Marko Zivkovic
Marko Zivkovic

 Chip Loder
Chip Loder




-m.jpg)




57 Comments
I blame that Maps and 8.0.1 QA guy. They should fire him again for this.
Badly explained article: for someone to exploit bash, they would have to be able to log in first. If a web server allows accessing bash, then the web server must also have an exploit. So unless one has a guest account with shell login or is worried about illegitimate privilege escalation by legitimate users (e.g. students in a computer lab), or is stupid enough to run random shell scripts, then I don't see how this is a problem, certainly not in the way it's phrased, unless there are additional exploits/vulnerabilities besides what's in bash.
Badly explained article: for someone to exploit bash, they would have to be able to log in first.
If a web server allows accessing bash, then the web server must also have an exploit.
So unless one has a guest account with shell login or is worried about illegitimate privilege escalation by legitimate users (e.g. students in a computer lab), or is stupid enough to run random shell scripts, then I don't see how this is a problem, certainly not in the way it's phrased, unless there are additional exploits/vulnerabilities besides what's in bash.
Not what I've read. Applications use terminal-type commands in the background to create log files for one example. These don't require a logon. Look at your log files through Console and see everything that's done. Apple probably uses some bash to create crash reports, which can automatically be sent to Apple. I've seen the same thing with other applications. You're helping them fix their code by sending error messages and crash reports. I'm not saying this is how this exploit works but people need to realize there's a lot of background code that runs that they never see or understand and anything can happen behind the scenes.
One thing that worries me quite a lot is whether or not the OS X DHCP client can/does run scripts. That would make it a very big deal non-advanced users as well. Likewise, I'm curious as to whether iOS uses bash as its underlying shell and similarly concerned about DHCP there. It would be much better if Apple were to be more forthcoming with such information when these kinds of things come up.
I blame that Maps and 8.0.1 QA guy. They should fire him again for this.
This comment wins!
Badly explained article: for someone to exploit bash, they would have to be able to log in first.
If a web server allows accessing bash, then the web server must also have an exploit.
So unless one has a guest account with shell login or is worried about illegitimate privilege escalation by legitimate users (e.g. students in a computer lab), or is stupid enough to run random shell scripts, then I don't see how this is a problem, certainly not in the way it's phrased, unless there are additional exploits/vulnerabilities besides what's in bash.
Yup, that's usually how most exploits work these days. It's no longer, one simple hack and the hacker now has root access. It's now usually a complex dance of exploits strung together in a specific order and way. Read, for example, how hackers have to jailbreak the iPhone (which *still* requires physical access to the device).
So, yes, this requires a vulnerable web server (which is certainly isn't that extraordinary) that also has mod_cgi enabled, which is also a not-out-of-the-ordinary configuration if they're doing some custom development.
That said, the Apple spokesman is right-- vast majority of Mac users wouldn't be running this config on their Macs.