A vast and sophisticated new espionage campaign targeting "military, diplomats, and business execs," discovered by Blue Coat Labs and confirmed by Kaspersky Labs, exploits flaws in Microsoft Windows and seeks to infect Android, Blackberry and iOS devices, but is limited to only infecting iPhones and iPads that are jailbroken.
The newly discovered malware network was covered in detail in a report by Dan Goodin of ArsTechnica, prominently naming "diplomats iPhone's" in the headline, along with "Androids and PCs," as being targeted by the attack.No mention of the fact was made that the malware itself can't be installed on iOS unless the device has been jailbroken first
The malware, targeting diplomats in an "international espionage campaign that's so sophisticated and comprehensive that it could only have been developed with the backing of a well resourced country," was described by the article as targeting "devices running Windows, Android, BlackBerry and iOS," but no mention of the fact was made that the malware itself can't be installed on iOS unless the device has been jailbroken first.
Blue Coat, which coined the name "Inception," based on the stealthy attack's "extremely advanced" layers of obfuscation to hide the identity of the attackers, also addressed iOS as being a target in the campaign in its blog posting without making any mention of the fact that iOS devices need to have their security turned off via jailbreak in order to fall victim to the attack.
The site did advise that to prevent infection, users should "keep software updated, don't jailbreak mobile phones, and don't install apps from unofficial sources," essentially a brutal condemnation of Google's platform goals for Android and a glowing endorsement of the security policies Apple has pursued on behalf of its iOS users.
To infect iOS, sophisticated hackers still require a jailbreak
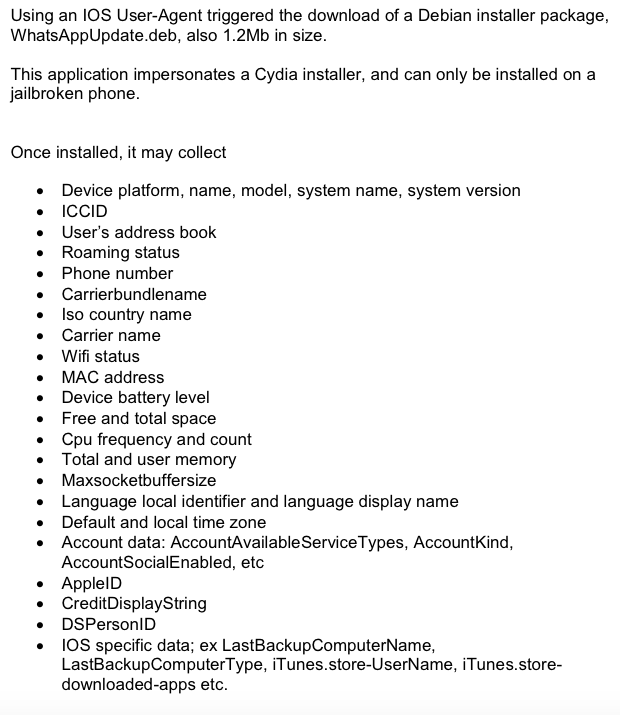
Only in its separate white paper on the subject (PDF) did Blue Coat note that the Inception malware, which posed as a WhatsApp app update, was packaged as a Debian installer package that "impersonates a Cydia installer, and can only be installed on a jailbroken phone."
The paper also noted that the attack has evolved (from its first appearance in 2013, when it was named "Red October" by Kaspersky Labs), now posing as the increasingly popular WhatsApp rather than Microsoft's Skype.
Once installed by a user, the jailbreak-malware can collect an iOS device's serial and phone number; spy on battery levels, memory use and other status information and settings as well as snoop on address book entries and the names of apps iTunes has installed.
Most iOS malware requires a jailbreak
A series of prior malware tools were similarly revealed to require a jailbreak, making them little real threat to the vast majority of Apple's users, particularly those updated to use the latest iOS. Apple actively works to close security exploits that enable jailbreaking, which turns off system security to allow users to "sideload" the installation of software, bypassing the iTunes App Store.
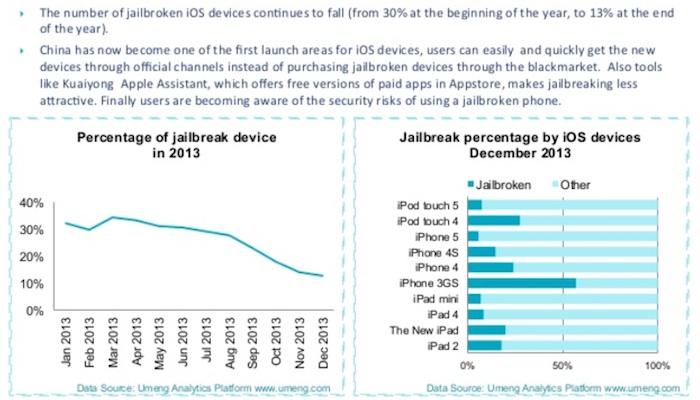
Side loaded apps are typically pirated, but may also include software Apple does not approve for sale in the App Store. The practice of jailbreaking iOS has become increasingly less interesting to users, particularly in China where the once-high percentage of jailbroken iOS phones has plummeted as legitimate app options have become available to customers in that country.
In August, it was revealed that governments and law enforcement groups were using FinFisher spyware by Gamma Group to surveil Android and iOS users, but that malware also required a jailbreak on iOS in order to be installed.
Similarly, in November new WireLurker and Masque Attack malware were detailed, both of which require users to either jailbreak their iOS device or to turn off OS X's Gatekeeper, which similarly limits Macs to only run software signed by a developer verified by Apple.
Google's Android has better malware than iOS
The Inception malware targeting Jailbroken iOS devices appears to be far less useful than the corresponding Android APK package, which also portrayed itself as a WhatsApp update users could install.
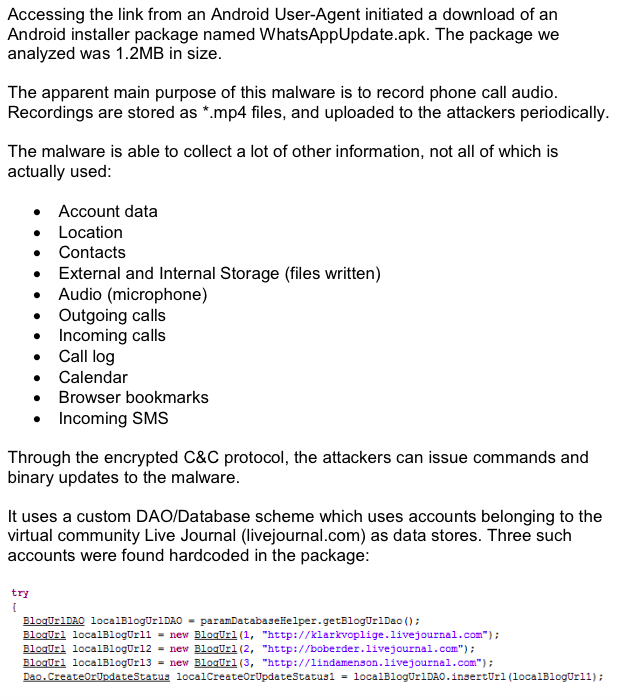
Blue Coat detailed that "the apparent main purpose of this malware is to record phone call audio. Recordings are stored as *.mp4 files, and uploaded to the attackers periodically," using the CloudMe internet storage service.
While unrelated to Apple's iCloud, Steve Jobs negotiated the purchase of the iCloud brand name from Sweden's Xcerion in 2011, just months before he debuted new iCloud features alongside iOS 5 and OS X Lion. The company subsequently rebranded itself as CloudMe. The malware appears to simply be using the cloud service for storage of the data it steals from Android users.
In addition to using the CloudMe service to host recordings of phone conversations stolen from infected Android phones, the Inception malware on Android "is able to collect a lot of other information," the security firm detailed, ranging from the user's account data and location to their contacts and calendar, remote and locally-saved files, audio from the microphone, incoming and outgoing calls, the user's browser bookmarks and incoming texts.
"Through the encrypted C&C protocol," the firm added, "the attackers can issue commands and binary updates to the malware."
Kaspersky Lab also detailed the same espionage network, naming it "Cloud Atlas." The firm notes that the Inception/Cloud Atlas malware campaign appears to be a reanimated version of the similar "Red October" attacks it first described in 2012, although the latest version uses new, more sophisticated measures to avoid detection.
While Inception/Cloud Atlas appears to specifically target diplomats and government agents, Android now has so many active vulnerability exploits that Bluebox Labs has developed a software tool for Google Play uses to scan their devices to identify a series of problems.
Last month, Bluebox examined a dozen new Android tablets currently being promoted by major U.S. retailers as holiday specials, finding "shocking" security flaws, malware and active backdoors installed on every one of the low priced devices.
 Daniel Eran Dilger
Daniel Eran Dilger







-m.jpg)






 William Gallagher
William Gallagher
 Andrew O'Hara
Andrew O'Hara

 Malcolm Owen
Malcolm Owen

 Christine McKee
Christine McKee
 Chip Loder
Chip Loder







75 Comments
The subtitle says Most iOS malware requires a jailbreak implying there is iOS malware that infects normal iOS devices. Name some.
God, imagine you're a hacker and having to analyse all the crap that people to speak to each other to identify something of use. Jeez. Yet another reason not to Jailbreak.
[quote name="TomMcIn" url="/t/183851/massive-sophisticated-inception-cloud-atlas-malware-infects-windows-and-android-but-cant-exploit-apples-ios-without-jailbreak#post_2650734"]The subtitle says Most iOS malware requires a jailbreak implying there is iOS malware that infects normal iOS devices. Name some.[/quote] Well if he wrote "All ios malware requires a jailbreak," some fool would find one obscure one and then label him a fanboy Apple MFer. Still don't jailbreak your phone.
Well, the link to the posted seems to have been taken down. Me think maybe them prominently including iOS there when it really should never have been might have been a bit too much for them? I was gonna write the author a blunt email about his click-bait tactics.
That's the last straw. Time to go back to a feature phone.