Apple on Wednesday confirmed that the removal of a pesky Recovery Key security mechanism will be one of the changes coming to its two-factor authentication solution when iOS 9 and OS X 10.11 El Capitan are released this fall.
Currently, the Recovery Key system in Apple's "two-step" protocol works as a failsafe for accessing an Apple ID when registered trusted device or phone number is unavailable. Under the existing setup, losing both a trusted device and Recovery Key renders the account inaccessible, which has in the past forced some users to abandon their Apple IDs altogether.
With higher level integration in iOS 9 and El Capitan, Apple's new method, now referred to as "two-factor," does away with 14-character Recovery Keys, to be replaced by a live customer support recovery process, an Apple spokesperson confirmed to MacWorld. The feature removal is just one modification Apple plans to apply when two-factor authentication rolls out later this year.
Other security enhancements were revealed in a support document published today, including longer six-digit verification codes and more intuitive authentication alerts that work across iOS and OS X platforms. For example, when users sign in to their Apple ID on a new device — or browser in the case of iCloud — with a password, a verification code is automatically pushed to all trusted devices. Text message and phone call verifications to trusted numbers will also remain available.
Because the system is built in to iOS 9 and El Capitan, devices running older iOS and OS X versions will not display the new six-digit verification codes. Once a user enables the new two-factor protocol, attempting to access an Apple ID using an iOS 8 device, for example, will send the six-digit code only to compatible devices. In lieu of a dedicated code entry mechanism, users might be prompted to log in again and append the six-digit number to the end of their password.
The new opt-in two-factor protocol is currently rolling out to a limited number of beta testers and will gradually become available to more users as Apple builds up backend support.
 AppleInsider Staff
AppleInsider Staff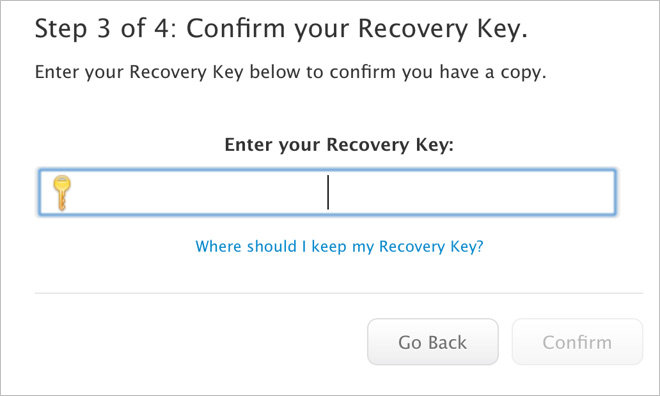







-m.jpg)






 Brian Patterson
Brian Patterson
 Charles Martin
Charles Martin


 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Marko Zivkovic
Marko Zivkovic







16 Comments
Look forward to the social engineering attacks used against the customer service reps to get around the two-factor authentication going forward.
^^^^ like the one with the Apple ID?
Look forward to the social engineering attacks used against the customer service reps to get around the two-factor authentication going forward.
Reading the support document, I suspect the method to prevent that is time. During the "several days", they'll probably send out account warnings and look for activity. For example, if you need to recover because your trusted phone is lost, and they see the phone connect to their servers as normal, then they know they're being tricked.
Bring it Especially smoothing the interaction of security between devices. One thing to note if you haven't experienced it yet. The tie in of security and Apple ID means - If for some reason you need to change your Apple ID, not a new account, but change your existing account and you have a bunch of devices then get ready for an evening of IT over a few beverages of your choice. You have to disable all iCloud stuff and sign out of everything on everything so that none of your devices are related to your Apple ID anymore in any way. Then you change via browser. Then you have to go through and reconnect and activate everything. If you don't you end up locked out of your own devices or with broken services. I REALLY hope in these new OS releases they have streamlined this. I did it in the correct manner a couple months ago now and while it did "just work" the process to do achieve it wasn't "it just works" rather it was more "it's just for nerds"
Darn. I've used my recovery key so often that I had recently memorized it. Oh well.