Last week's release of iOS 8.4.1 brought more than just Apple Music fixes — it also patched a previously undisclosed hole in the app sandbox that made it possible for iOS devices operating in managed environments to unknowingly leak configuration and credential data to other third-party apps.
Dubbed "Quicksand" by its discoverers at security firm Appthority, the vulnerability stemmed from a permissions issue in the managed app configuration system. This system — Â introduced with iOS 7 — makes it easier for enterprises to administer iOS devices by providing a built-in mechanism for distributing and storing customized app configuration data, such as server URLs and corporate network information.
For example, a network administrator could pre-load a configuration file for an enterprise messaging app that includes the company's hosted server URL and access token. Once installed, the app could read that file and automatically configure itself without user intervention.
While the system was designed to limit access to those files to the apps for which they're intended, Appthority found that the files were actually readable by any app installed on the device.
This meant that attackers could exfiltrate the configuration data — Â which often includes sensitive access credentials or other secret company information — Â by creating a legitimate app, distributed through the App Store, that was designed to read the configuration files from other popular enterprise apps and then phone home.
Appthority worked with Apple to patch the problem in iOS 8.4.1, but the security firm says that as many as 70 percent of enterprise iOS devices are not updated for months after a new iOS version is released. For corporate administrators who are unable to update iOS, Appthority recommends that they reconsider storing sensitive data in the managed app configuration system and use other means — Â such as custom URL schemes — Â to provision the data after app installation.
 Sam Oliver
Sam Oliver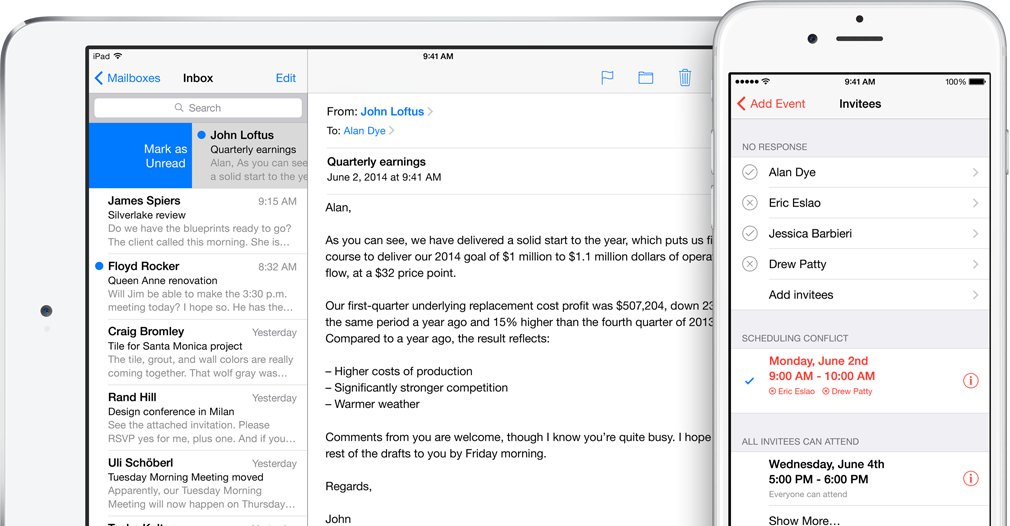


 William Gallagher
William Gallagher

 Andrew O'Hara
Andrew O'Hara
 Wesley Hilliard
Wesley Hilliard

 Malcolm Owen
Malcolm Owen
 Marko Zivkovic
Marko Zivkovic





-m.jpg)




5 Comments
iOS has been approved for government use. I know they have lots of security-related people testing systems and configurations (I worked in one of those departments) so why didn't they find this bug? Maybe because they continue to only work on Windows security, some linux, and leave anything from Apple for the last. Apple can't fix everything so it relies on users, just like every other software firm, but something like this should have been found a long time ago. It was there in iOS7, which also was approved for government use, so security people have had time to find it. Maybe the risk of an exploit was low enough to not worry about it. (Risk management of the 21st century)
Updates for your equipment - advantage Apple.
That is strange, it still looks like the facebook app have access to my contacts even though I have never enabled anything which would allow it to have that.
Good to see a responsible approach from Appthority: talked privately with Apple, waited for the fix to be available before going public. Then they quite rightly got the kudos for finding the problem. Nice to see that there are some grown-ups left following the Tedesco foolishness.
[quote name="rob53" url="/t/187810/with-ios-8-4-1-apple-patches-app-sandbox-vulnerability-that-could-lead-to-enterprise-data-theft#post_2763958"]iOS has been approved for government use. I know they have lots of security-related people testing systems and configurations (I worked in one of those departments) so why didn't they find this bug? Maybe because they continue to only work on Windows security, some linux, and leave anything from Apple for the last. Apple can't fix everything so it relies on users, just like every other software firm, but something like this should have been found a long time ago. It was there in iOS7, which also was approved for government use, so security people have had time to find it. Maybe the risk of an exploit was low enough to not worry about it. (Risk management of the 21st century) [/quote] You've got 20/20 hindsight vision - but if you had really ever worked in one of those departments, you'd understand that it's impossible to test everything and some things (like this) seem completely obvious AFTER it's been discovered but BEFORE the vulnerability is known it could be VERY difficult to find - even by the best security experts in the world. It's ignorant to imply that these people were not doing there job properly because YOU think that this should have been an easy thing to find. Good job though to the person/people that did discover it and I'm happy to hear they did the responsible thing by reporting it privately so it could be fixed instead of posting it publicly and putting us all at greater risk.