A new version of the long-running Genieo adware has brought with it a new technique for accessing the OS X Keychain without user intervention, a security gray area that could be used by other malicious actors to make off with sensitive data stored in the Mac credential manager.
The adware depends on an OS X feature that is designed to prevent users from being forced to enter their account password multiple times in quick succession. As discovered by Malwarebytes, the Genieo installer asks users to authenticate with their password prior to installation — Â but it later mounts a special app that asks for keychain access, prompting a different dialog that asks the user whether to allow or deny that access.
This secondary dialog does not prompt for a password, and the installer simulates a mouse click on the "Allow" button. The entire process takes just a fraction of a second.
Many users are unlikely to notice the window, and even those that do could be prone to ignore it.
Because this behavior does not rely on an OS X flaw, it is particularly dangerous and comes with a high potential for abuse. Such a request could be embedded in any seemingly innocuous file and is difficult to guard against without changing the behavior of the Keychain request dialog.
Even more worrying, OS X apps can, by design, request access to any Keychain entry they desire. It's left up to the user to decide whether that app should be allowed to have access, so this technique could be used to steal nearly anything that has a known Keychain entry.
Apple has not yet responded to these reports, though they may address the problem before the release of OS X El Capitan.
As always, users should follow common-sense security practices: do not download files from unknown sources, and be wary of e-mails or websites that seem suspicious or non-authentic.
 Sam Oliver
Sam Oliver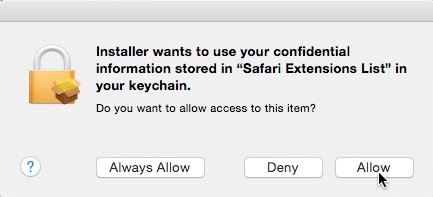








 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen
 Marko Zivkovic
Marko Zivkovic

 Andrew Orr
Andrew Orr
 Andrew O'Hara
Andrew O'Hara
 William Gallagher
William Gallagher





-m.jpg)



20 Comments
"Such a request could be embedded in any seemingly innocuous file like a photo" I'm totally lost on how that could be initiated.
Absolutely heinous.
Because this behavior does not rely on an OS X flaw, it is particularly dangerous and comes with a high potential for abuse.
Actually it is a design flaw, but not a software bug. The design is defective.
Windows, since NT 3.1 (which derived it from a similar feature from VMS), has had a trusted path. In the early versions, you had to press control-alt-del to enter your password or change it. Vista enhanced this for UAC, which is why the desktop grays out when you need to elevate. The whole point of this is to prevent any application from intercepting keyboard input or manipulating the GUI, solving the exact weakness you see here.
[quote name="AppleInsider" url="/t/187985/new-adware-scripts-mouse-clicks-to-access-os-x-keychain-could-lead-to-password-theft#post_2769599"]...the Genieo installer asks users to authenticate with their password prior to installation...[/quote] So...don't give it?
So someone entering their password to authenticate is required? Not really a design flaw. If I give access to something like that, I'm at fault not the OS. The fact it's required says Apple did their job.