Apple allayed customer concerns over a recently discovered iOS bug on Tuesday, noting an exploit that leveraged Siri and 3D Touch to gain unauthorized access to a user's Contacts and Photos has been fixed. However, the apparent server-side Siri update now requires a passcode or Touch ID authentication to search Twitter.
In a statement to The Washington Post, an unnamed Apple representative confirmed a fix was installed earlier today, saying that the solution does not require users to update their system software. From the scant information provided, it is speculated that the flaw was patched on Apple's end, likely through an adjustment to Siri's search handling permissions.
AppleInsider has confirmed the patch is indeed in effect, with Siri now requiring a passcode or Touch ID authentication prior to conducting Twitter searches. Since Apple chose to optimize Siri and not patch the associated on-device 3D Touch Quick Action vulnerability, the new search authentication requirement likely extends to other integrated apps.
The patch comes less than one day after a proof-of-concept video was posted to YouTube detailing a new lock screen exploit. In the example scenario, a nefarious user first asks Siri to conduct a Twitter search for a known tweet containing an email address, which in turn triggers iPhone's data detectors feature. Performing a 3D Touch gesture on the resulting actionable link allowed access to Contacts, and from there a user's photo library.
Whether Apple will integrate a more elegant fix into a future iOS point release is unknown, though the current resolution adds an unnecessary level of complexity to Siri's user experience. It also prohibits users from searching Twitter, and potentially other apps, via the "Hey Siri" handsfree feature.
 AppleInsider Staff
AppleInsider Staff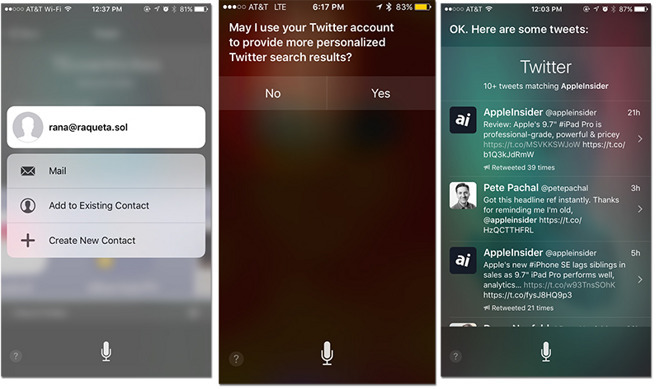








 Marko Zivkovic
Marko Zivkovic
 Mike Wuerthele
Mike Wuerthele
 Christine McKee
Christine McKee
 Amber Neely
Amber Neely
 Sponsored Content
Sponsored Content
 Wesley Hilliard
Wesley Hilliard

 William Gallagher
William Gallagher








5 Comments
This is what's so great about Apple.
Slight clarification... You can't use the "Hey Siri" voice command to search with Siri from the lockscreen without Siri asking you to unlock the phone first. The exploit worked by long-pressing the Home key (with your fingernail - or a non-registered finger) and making the voice search of Twitter
"...the current resolution adds an unnecessary level of complexity to Siri's user experience." It's unnecessary only if you don't care about the exploit.
lets talk some more about how apple software sucks today, and how there were never any bugs back in the good ole days.