Dropbox recently notified users of a potential forced password reset after its security team discovered a batch of account credentials believed to have been obtained from a known 2012 data breach. While the initial announcement failed to specify the exact number of impacted users, a report on Tuesday puts the number at well over 68 million.
In a set of files obtained through sources in the database trading community and Leakbase, Motherboard found evidence relating to 68,680,741 Dropbox accounts, including email addresses and hashed, or salted, passwords. An unnamed Dropbox employee verified the data's legitimacy.
It is unclear how many users have been impacted by the hack dating back to 2012, but today's report is the first to offer detail on the previously disclosed breach.
Last week Dropbox sent out emails alerting an unknown number of users that they might be prompted to change their password if they had not done so since mid-2012. The company said the measure was "purely preventative," apologized for the inconvenience and directed users looking for further details to a Help Center webpage. The FAQ runs through the password reset process and, about halfway down the page, reveals the impetus behind the new protocol.
Our security teams are always watching out for new threats to our users. As part of these ongoing efforts, we learned about an old set of Dropbox user credentials (email addresses plus hashed and salted passwords) that we believe were obtained in 2012. Our analysis suggests that the credentials relate to an incident we disclosed around that time.Based on our threat monitoring and the way we secure passwords, we don't believe that any accounts have been improperly accessed. Still, as one of many precautions, we're requiring anyone who hasn't changed their password since mid-2012 to update it the next time they sign in.
Within Motherboard's cache of user data, almost 32 million of the passwords are secured using the "bcrypt" hashing function, while the remainder are protected by what is believed to be salted SHA-1 hashes.
"We've confirmed that the proactive password reset we completed last week covered all potentially impacted users," said Dropbox's Head of Trust and Security, Patrick Heim. "We initiated this reset as a precautionary measure, so that the old passwords from prior to mid-2012 can't be used to improperly access Dropbox accounts. We still encourage users to reset passwords on other services if they suspect they may have reused their Dropbox password."
 AppleInsider Staff
AppleInsider Staff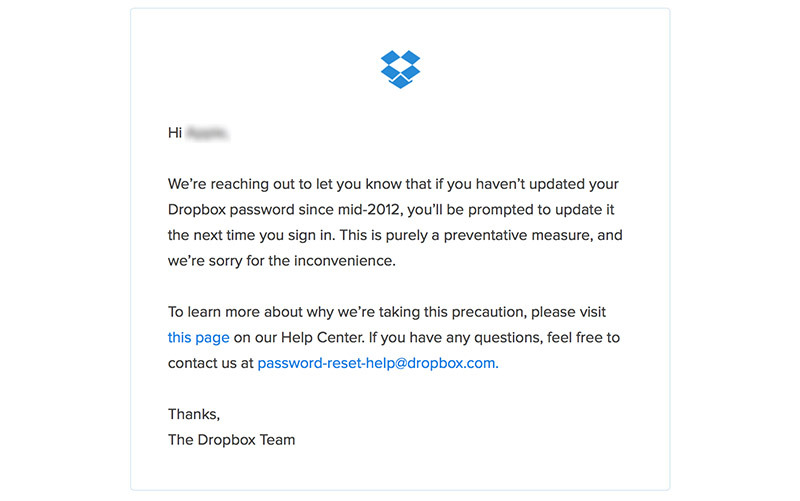







-m.jpg)






 William Gallagher
William Gallagher
 Andrew Orr
Andrew Orr
 Mike Wuerthele
Mike Wuerthele
 Bon Adamson
Bon Adamson
 Marko Zivkovic
Marko Zivkovic
 Wesley Hilliard
Wesley Hilliard
 Amber Neely
Amber Neely





-m.jpg)



19 Comments
Lucky I don't use dropbox. I can't trust any cloud beside Apple iCloud.
I trust Dropbox, but it hasn't been without its issues. Years ago, it would be stuck on the sync process ("Updating" or "Downloading") without explanation, but that hasn't happened recently. I do find it strange that they are responding to this incident (a second time?) 4 years later. Something is suspicious and it feels like they are deliberately leaving out some details while trying to remain innocent. Being forthcoming about everything is absolutely critical to maintain trust.
I've been prompted for several of my accounts, but none of them have prompted me to choose a new password upon login. That leaves one feeling puzzled in and of itself.
Interesting.
I knew there was a reason why I've been avoiding Dropbox.
I just plain give up. There is not one company (except for Apple maybe) that is responsible enough to put an emphasis on security. I was one of the affected DropBox users. It's still superior in just about every area (for me) and each time I use iCloud, I continue to revert back to DropBox.
It is inexcusable for a company like Dropbox to drop the ball like they did. Really. I didn't even know anything about a breach back in 2012. What measures were in place since then to now to ensure that no one hacked into my account and did something nefarious in there?