Security researchers have discovered new malware for macOS called 'MacDownloader,' which is believed to have been created by Iranian hackers to try and attack individuals and companies involved in the US defense industry.
Claudio Guarnieri and Collin Anderson, researchers analyzing online threats stemming from Iran, discovered the malware on a site that impersonated the US aerospace firm "United Technologies Corporation." The site — which referenced Lockheed Martin, Sierra Nevada Corporation, and Boeing — claimed to offer "Special Programs and Courses," in an attempt to try and attract potential defense targets.
The fake site was previously used as part of an earlier spearphishing attempt, which tried to spread Windows malware to victim systems. The host, thought to be "maintained by Iranian actors," has also been used for other phishing attempts, with fake sites for a dental office and a U.S. Air Force training page created for the attacks.
Visitors to the current fake site would be provided with malware for either Windows or macOS, depending on the detected operating system. In MacDownloader's case, it creates a fake Adobe Flash Player dialog that offers to update the Flash player, or to close the window.
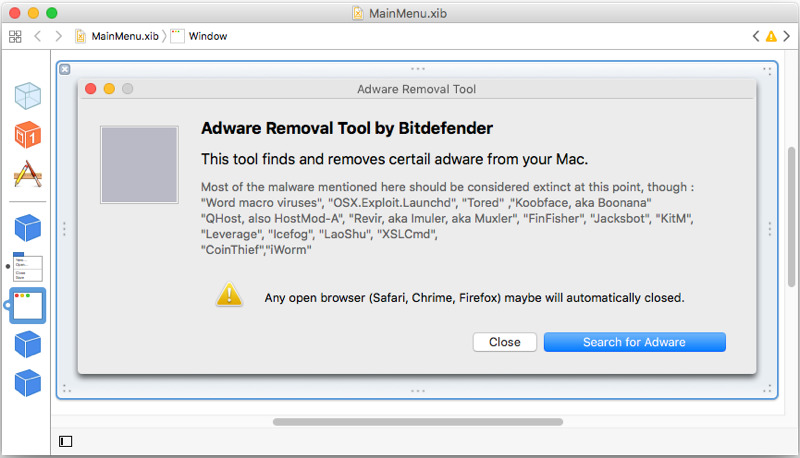
Upon accepting the update, a second dialog would appear, claiming to be an "Adware Removal Tool by Bitdefender," and offering to search for adware. The researchers suggest MacDownloader was originally designed as a fake virus removal tool, but was repackaged as a fake Flash Player update as part of another social engineering effort.
Once installed, the malware attempts to harvest data from the infected Mac, sending the user's Keychain to the attacker's server among other items. The malware can also prompt a fake System Preferences dialog to try and acquire the username and password, which can then be used to access the encrypted Keychain data.
It is noted by the researchers that the code is "poorly developed" by the hackers, and is likely the "first attempt from an amateur developer." Aside from spelling and grammar issues, as well as the change from Flash to Bitdefender in the dialog boxes, code behind the malware is claimed to have been copied from other sources, such as the use of code from a "cheat sheet" for the simple task of downloading a remote file.
The code also reveals the developer initially intended to install a persistent process, one that would have been able to automatically run at start up, download a file, and run new commands. The "poorly-implemented shell script" is unused by the malware, with remote server calls using Apple's Core Services framework instead.
"Based on observations on infrastructure, and the state of the code, we believe these incidents represent the first attempts to deploy the agent, and features such as persistence do not appear to work," the researchers write. "Instead, MacDownloader is a simple exfiltration agent, with broader ambitions."
Aside from targeting the US defense industry, the malware has also reportedly been used to attack a human rights advocate, suggesting the malware could be used to attack other communities that may be of interest to state-sponsored hackers in the future.
While Windows is considered the main target for malware attacks, due to its high usage by companies and individuals, the researchers note communities such as those involved in human rights and security tend to use Apple devices instead. Anecdotally, the researchers claim these communities focused on activities in Iran are "strongly dependent on Apple devices."
The status of Mac as a minority platform compared to Windows does provide some level of protection from attacks, though more is also being done to thwart such efforts. Taking a cue from Google and other tech companies, Apple started a bug bounty program last year, offering rewards to those who find weaknesses in the company's operating systems.
 Malcolm Owen
Malcolm Owen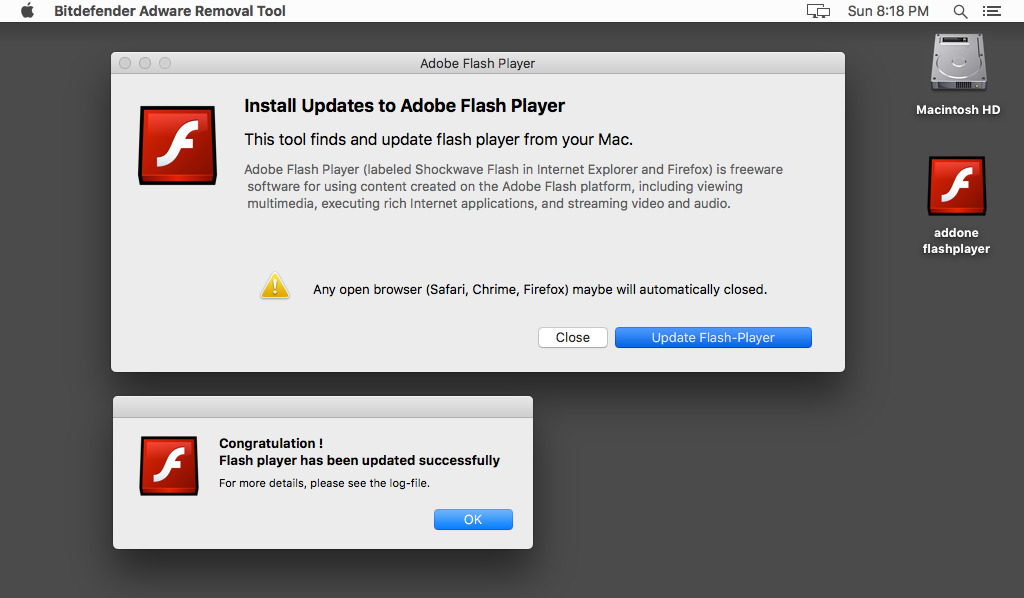







-m.jpg)






 William Gallagher
William Gallagher
 Christine McKee
Christine McKee
 Marko Zivkovic
Marko Zivkovic
 Mike Wuerthele
Mike Wuerthele

 Amber Neely
Amber Neely
 Sponsored Content
Sponsored Content
 Wesley Hilliard
Wesley Hilliard









23 Comments
This thread is about to become political
Another reason to not install Flash. Come on Adobe, you know your software is the (current) largest method of spreading malware. Do something about like shutting it down.
As if the real Flash were not bad enough, now we have something falsely claiming to be it.