A set of six collegiate researchers are set to unveil details on a Key Reinstallation Attack (KRACK Attack) for WPA-2 Wi-Fi security, which if legitimate can allow attackers to undermine encryption on any wi-fi connection utilizing the security method — including Apple hardware connecting to Airport Extreme and Airport Express routers. AppleInsider explains what it is, and how to cut down on the potential for attack until patches are rolled out.
The exploit, published on Monday, takes advantage of a four-way handshake between a router and a connecting device to establish the encryption key. Properly executed, the third step can be compromised, resulting in the re-use of an encryption key — or in some cases in Android and Linux, the establishment of a null key.
US-CERT, the division of the Department of Homeland Security responsible for computer safety has become aware of "several key management vulnerabilities" used in the attack. The agency has declared that the vulnerability includes lack of proper encryption, content hijacking, HTTP injection, and other problems. In the advisory issued on Monday, US-CERT says that "most or all correct implementations" of WPA-2 are affected by the vulnerability — meaning every consumer device, and most enterprise access points.
The researchers claim that the attack vector completely opens up an Android 6.0 and later device. Other operating systems, including iOS and macOS are less impacted, but "a large number of packets" can still be decrypted from all.
At present, there are no patches for consumer-grade devices, and only a few commercial manufacturers have issued updates. A large percentage of network equipment will likely not see updates — so a properly patched operating system will be essential for users.
The attack uses one or more of 10 different exploits. The details of the exploit were submitted for review on May 19, and a conference presentation will be delivered on Nov. 1.
Fixes can be made by vendors on either the client or router level, and only one of the pair needs to be patched for the vulnerability to be ineffective. A patched computer can connect to an un-patched router and not be vulnerable, and vice-versa. Updates to either will prevent an encryption key from being reused.
How to mitigate the issue until a patch is issued
Most networks in single-family homes are probably safe. However, in apartment buildings and thickly-settled areas, there remains the potential of attack — if the exploit is as easy to implement as the researchers claim it is.
When and if a patch becomes available for your computers, routers, or other Wi-Fi gear — implement it. If you're not on macOS Sierra, macOS High Sierra, or iOS 11, it might be time to get there.
Avoid public Wi-Fi. That will cut down on exposure vectors for most users while patches are being rolled out.
The researchers note that they cannot retrieve data downloaded from a "properly configured HTTPS site" — but a "significant fraction" aren't well set up. Avoid transmitting sensitive data to non-HTTPS sites.
While networks not broadcasting SSID, or network name, can still be sniffed out by the determined, still consider not having a publicly broadcast network name. If somebody is just looking to stir up some trouble, a less visible network is less likely to be attacked than a publicly broadcasting one.
To secure your own home network, ensure that home servers and network attached storage devices all have non-default passwords for file sharing and other services, and use Ethernet whenever possible. Additionally, to prevent an attack on a printer possibly resulting in hundreds of pages of garbage being printed, consider turning off printers when not in use.
 Mike Wuerthele
Mike Wuerthele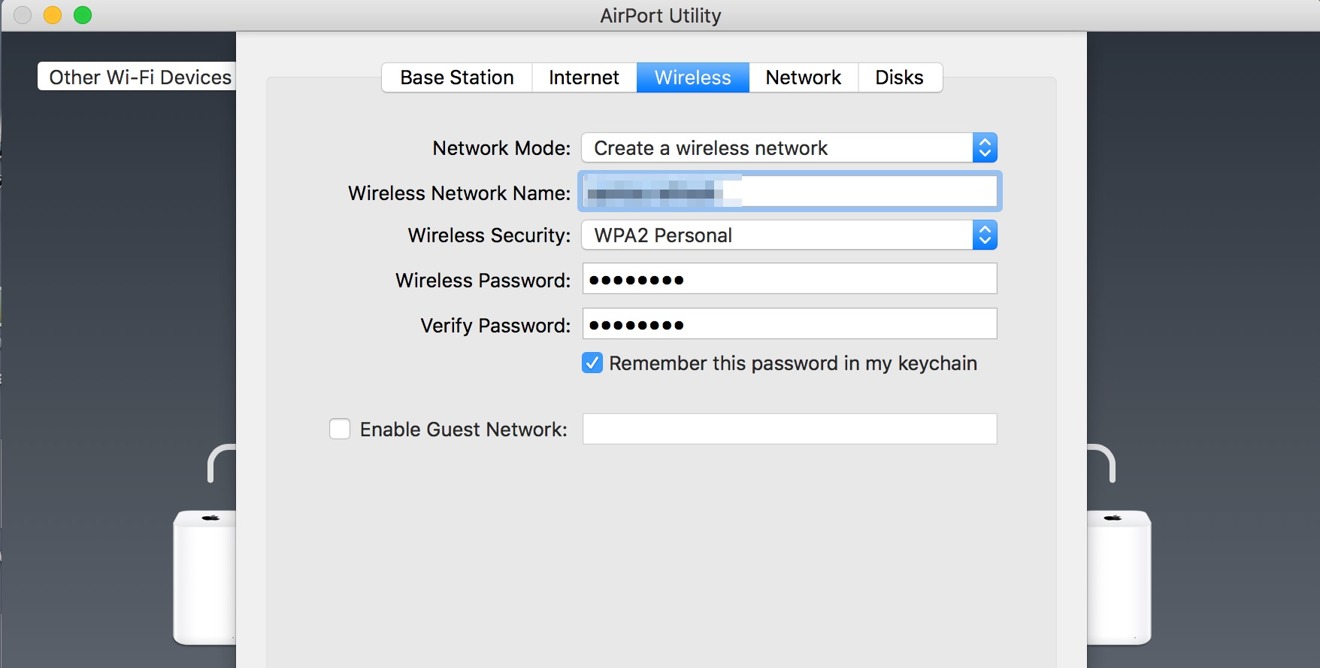

-m.jpg)






 Andrew O'Hara
Andrew O'Hara
 Wesley Hilliard
Wesley Hilliard

 Malcolm Owen
Malcolm Owen
 Marko Zivkovic
Marko Zivkovic

 Chip Loder
Chip Loder
 Christine McKee
Christine McKee




-m.jpg)




29 Comments
Those in large apartment buildings or using public Wi-Fi (bad idea to begin with IMHO) would appear to be most at risk, and bored teens are the ones I'd personally worry about most. Yes turning off Wi-Fi connected printers too when not in use, particularly in a high-density area, sounds like good advice.
The list of affected routers and the current patch status is here:
https://www.kb.cert.org/vuls/byvendor?searchview&Query=FIELD+Reference=228519&SearchOrder=4
Given the way they work, I imagine VPNs render the attacks useless as well.