After supposedly tricking Apple's Face ID security system earlier this month with a $150 mask, Vietnamese security firm Bkav on Monday said it has repeated the process with a second 3D-printed mask that can also bypass iPhone X's attention detection safeguard.
In its first video, Bkav demonstrated a proof of concept Face ID attack involving a 3D-printed frame covered in makeup, a silicone nose, 2D images and a large "specially processed" area.
At the time, skeptics called Bkav's methodology into question. Notably, the security firm failed to record the Face ID enrollment process, meaning Bkav could have enrolled the mask as the device's primary user. Alternatively, Face ID might have adjusted to authenticate the original mask over the course of multiple unlock attempts as the system "learns" from consecutive successful unlocks, a feature designed cope with natural changes to a user's face.
Bkav's latest video, however, runs through the entire enrollment process without cuts, suggesting the new mask — 3D printed from stone powder with eyes represented by 2D infrared images — did indeed circumvent Face ID's protections.
Seen in the short clip, a human user erases the enrolled Face ID profile in system settings and sets up a new account in real time. The user unlocks the handset using his own face, locks it and carefully positions it in front of the mask dubbed the "artificial twin." Bkav's double successfully unlocks iPhone X not once, but twice.
Perhaps more impressive is that Bkav was able to bypass Face ID's attention detection feature, an optional safeguard that monitors a user's eyes to verify that they are looking at their phone before unlocking it.
In a blog post detailing the procedure, Bkav said the new mask cost about $200 to produce using materials and tools readily available to casual users.
"About 2 weeks ago, we recommended that only very important people such as national leaders, large corporation leaders, billionaires, etc. should be cautious when using Face ID," said Ngo Tuan Anh, VP of cyber security at Bkav. "However, with this research result, we have to raise the severity level to every casual users: Face ID is not secure enough to be used in business transactions."
According to the firm, fingerprint-based biometric security systems are superior to facial recognition solutions like Face ID. Fingerprints, the firm says, cannot be collected at a distance, while photographs can. That said, it is unclear what data Bkav used to create its second mask. Traditionally, 3D printed objects are rendered from highly accurate CAD files or three-dimensional scans run through specialized software.
Whether Bkav was able to extrapolate dimensioning data from 2D photographs is unknown.
Bkav's video is the latest in a string of attempts to defeat Face ID. Earlier this month a video showing a 10-year-old unlocking his mother's iPhone X surfaced, offering evidence that Face ID is sometimes unable to distinguish between family members who strongly resemble each other. Other unscientific tests involved twins, some of whom were able to unlock a sibling's device.
 Mikey Campbell
Mikey Campbell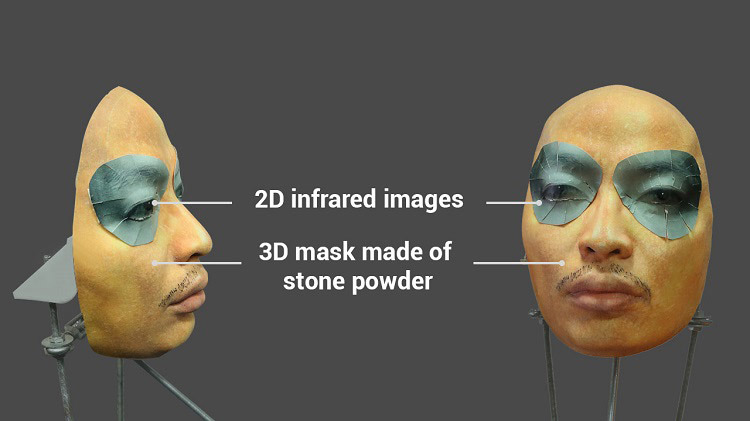







-m.jpg)






 Amber Neely
Amber Neely
 Malcolm Owen
Malcolm Owen


 Christine McKee
Christine McKee

 William Gallagher
William Gallagher


-m.jpg)






94 Comments
So are people going to walk around wearing $200 masks of me, somehow getting the exact dimensions of my face? I think this is kinda stupid and worthless.
From Mashable: "Bkav researchers said that making 3D model is very simple," the blog post noted. "A person can be secretly taken photos of in just a few seconds when entering a room containing a pre-setup system of cameras located at different angles. Then, the photos will be processed by algorithms to make a 3D object."
So, to unlock an iPhone X using this hack, you need to do one of two things: 1) Steal a phone and then capture a bunch of photos of the owner without his/her knowledge, print a mask using stone dust and some kind of infrared printer, all within 48 hours (or less) to get under the phone's biometric time limit, or 2) do all of that stuff BEFORE you steal the phone so the mask will be ready when you have the phone in your custody.
Oh yeah. You iPhone X owners should be petrified with concern.
Weird, after scanning his face without actually looking at the camera (his eyes were glancing down), the lock icon was unlocked when he first tried having the mask unlock it, then the lock changed to locked and he said it was unlocked.
I wish people would use standard test practices instead of having both the test mask and the real face in the room in the same general area at the same time. If I was running this test, I'd encode my face in another room, test to make sure it unlocks, then restart the phone, enter my pin, lock the phone then unlock with my face again to make sure the normal, entire process works.
Once this is done I'd lock the phone and give the phone to a different person who takes it into a separate room and tries unlocking it with the mask.
I would think Apple's algorithms would notice a 2D print of the eyes and the lack of realistic 3D around the eyes. A person can not make the exact "face" twice in a row so the software should sense the lack of change in facial muscles from one attempt to the next. Until someone actually runs a proper test, I will still believe in Apple's FaceID product.
The missing detail is the step by step procedure to get the data for the scan. Documented in real-time.
A bland declaration of “easy” doesn’t cut it.
If I'm not mistaken, the Apple FaceID learns the user's face and get better over time. So providing it will initial data then testing it may not be the best way to test the security of FaceID. Other users have noted that after doing the initial FaceID scan there are instances where they have to unlock using the PIN to confirm that it was their face that was scanned based on subtle changes, such as a hat, glasses, etc.