Online retailer Newegg has become the victim of a month-long data breach, with the payment details of thousands of customers potentially acquired by hackers, by adding code to the store's payments page in a similar manner to other recent attacks.
The breach, discovered and verified by security firm Volexity in collaboration with RiskIQ, appears to have been in operation since August 14 and ran until September 18, reports TechCrunch. The attack, which injected just 15 lines of code into the payments page, allowed for credit card information to be skimmed and stored on a private server during the checkout process.
The attackers created a website with a similar name to Newegg's store, titled in such a way as to avoid suspicion, and was even issued its own HTTPS certificate. When alerted, Newegg removed the JavaScript from the site and started to alert customers.
Newegg chief executive Danny Lee advised to customers in an email the company has not yet determined which accounts were affected, with the size of the attack largely unknown. As a major retailer earning 2.65 billion in revenue in 2016 and having more than 45 million monthly unique visitors, the number of affected customers who shopped at Newegg during the period could be quite high.
The attack hit both desktop and mobile versions of the Newegg site, but it is unclear if mobile users were affected by the breach at all.
According to RiskIQ, the attack is a continuation of a string of compromises known as "Magecart," which has impacted a number of major businesses. Analysis of the attack reveals it to be similar to those hitting British Airways' booking system and Ticketmaster, with each targeting booking and payment systems by acquiring the data before it reaches the company's servers, rather than attacking the servers directly.
The similarity of the code between the British Airways and Newegg attacks suggest it to be from the same code base, and possibly from the same hackers. Few elements were changed in the code, but the length of the JavaScript code was shorter in Newegg's version due to only needing to serialize one form, rather than the multiple forms used by the airline.
The relative ease and length of time the breach can exist for certainly suggests future attacks of this type could stick around for some time, and with a wide variety of available targets.
"The breach of Newegg shows the true extent of Magecart operators' reach," advised RiskIQ's Jonathan Klijnsma. "These attacks are not confined to certain geolocations or specific industries - any organization that processes payments online is a target."
 Malcolm Owen
Malcolm Owen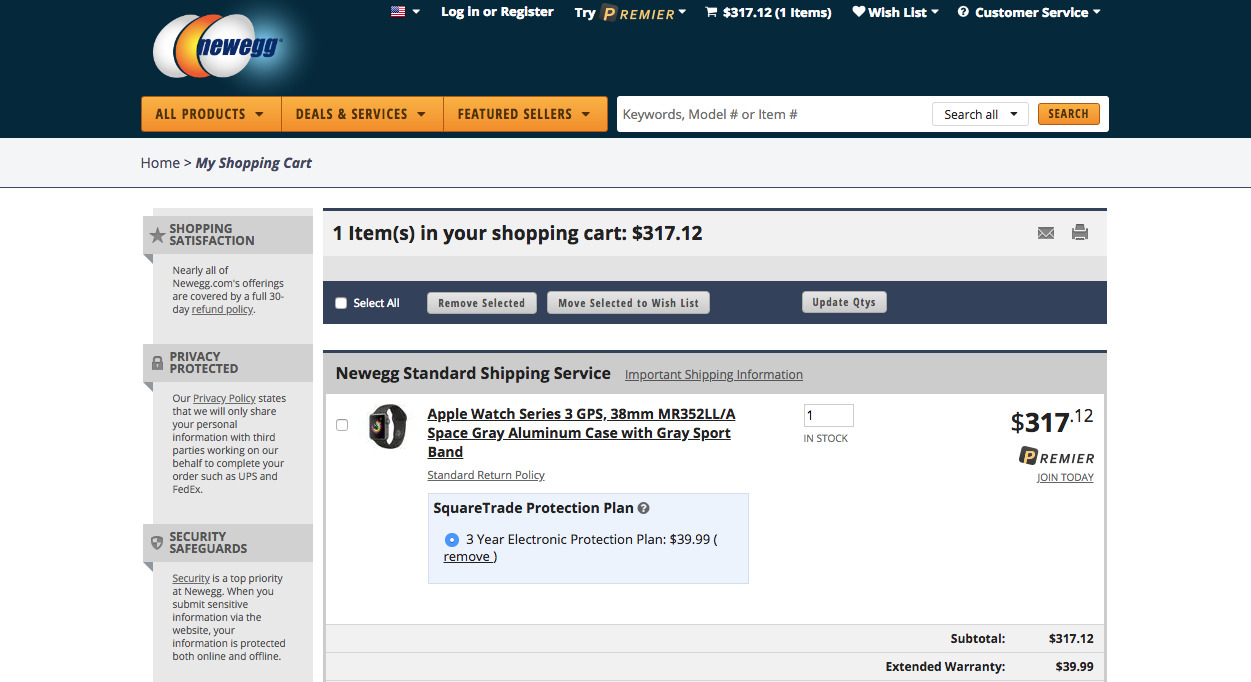







-m.jpg)






 Marko Zivkovic
Marko Zivkovic
 Christine McKee
Christine McKee
 Andrew Orr
Andrew Orr
 Andrew O'Hara
Andrew O'Hara
 William Gallagher
William Gallagher

 Mike Wuerthele
Mike Wuerthele
 Bon Adamson
Bon Adamson




-m.jpg)



6 Comments
This is one reason among many to only buy direct from Apple. The other is that way, Apple doesn't hhave to share any money with third parties. They get it all.
I always use Apple Pay with Newegg.