The issue, first discovered by security firm Major Security, is an error in how Apple's mobile Safari app in iOS 5.1 handles URLs when using javascript's window.open() method that can be exploited by malicious sites to display custom URLs.
"This can be exploited to potentially trick users into supplying sensitive information to a malicious web site," Major Security explains, "because information displayed in the address bar can be constructed in a certain way, which may lead users to believe that they're visiting another web site than the displayed web site."
The exploit was tested on an iPhone 4, iPhone 4S, iPad 2 and third-generation iPad running iOS 5.1, and it seems that any iDevice running Apple's latest mobile OS is affected by the vulnerability. Users can test the vulnerability themselves by visiting this webiste from a mobile device. After a user clicks the "demo" button on the test page, Safari will open a new window which shows "http://www.apple.com" in the address bar, but that URL is in fact being displayed through an iframe being hosted by Major Security's servers.
By spoofing a URL and adding some convincing images to a malicious site, users can easily be tricked into thinking they are visiting a legitimate website such as Apple's online store.
"Apple" iPad webpage through Major Security servers (left) compared to official Apple site (right).
The vulnerability was originally found in iOS 5.0 and reproduced on iOS 5.1 earlier in March. Apple was made aware of the issue on March 1 and posted an advisory regarding the matter on March 20. A patch has yet to be pushed out, though the iPhone maker is expected to do so in the near future.
 AppleInsider Staff
AppleInsider Staff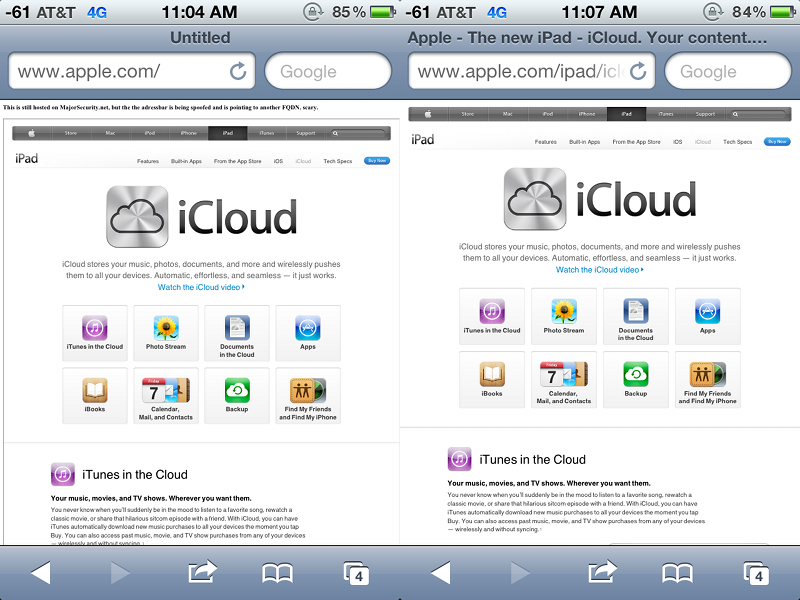








 Amber Neely
Amber Neely
 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Chip Loder
Chip Loder
 Brian Patterson
Brian Patterson

-m.jpg)






14 Comments
Now Apple will patent this and attempt to sue Samsung.
Their demo page doesn't work as stated on my copy of Safari (5.1.3), OS X 10.7.3.
-kpluck
Now Apple will patent this and attempt to sue Samsung.
I think you have that backwards. Samsung will sue Apple after they fix it because once fixed the behavior will replicate the browser already found on Samsung devices which has a patent for being unspoofable.
Their demo page doesn't work as stated on my copy of Safari (5.1.3), OS X 10.7.3.
-kpluck
Mobile Safari not OS X
These types of exploits never seem to get used in phishing scams but it's bad form nonetheless. If this isn't resolved in 5.1.x I'll be surprised.edit: Pipped my mstone.