A new security flaw in macOS High Sierra has been discovered by researchers — one that can grant users access to the system administrator account on a target machine, enabling access to the account without requiring a password.
Posted on Twitter by software engineer Lemi Orhan Ergin, the vulnerability requires relatively few steps to accomplish, and takes advantage of a section within the System Preferences menu. AppleInsider is not publishing the full set of instructions for the sake of security, but staff tests have confirmed it to be functional, and extremely simple to follow.
Dear @AppleSupport, we noticed a *HUGE* security issue at MacOS High Sierra. Anyone can login as "root" with empty password after clicking on login button several times. Are you aware of it @Apple?
— Lemi Orhan Ergin (@lemiorhan) November 28, 2017
Once the few steps were performed, AppleInsider staff discovered the "root" System Administrator account on the Mac mini with macOS 10.13.1 being used for testing was enabled, despite having been previously disabled. After disabling the account, following the same instructions re-enabled the account.
The flaw exists in all versions of High Sierra, including Beta 5 that was released earlier on Tuesday.
Granting access to the System Administrator account allows users free reign to the macOS desktop, including the ability to view all files stored on the computer in all user accounts, edit the credentials of other users, and alter other settings on the device.
It is unclear if Apple was advised of the security issue before Ergin's Twitter disclosure, but his query to Apple Support asks "Are you aware of it @Apple?" suggesting no such advance warning was made.
While a major vulnerability, it still requires access to the computer either locally or with a Remote Access connection. It also needs an authorized user to be logged in to generate the Root account with no password. Disabling the Guest account provides a level of protection, by requiring users to have a presumably secure password to access the computer in the first place.
In a support page, Apple says that the Root user is not intended for routine use, with the user getting privileges that allow changes to files that are required by the Mac.
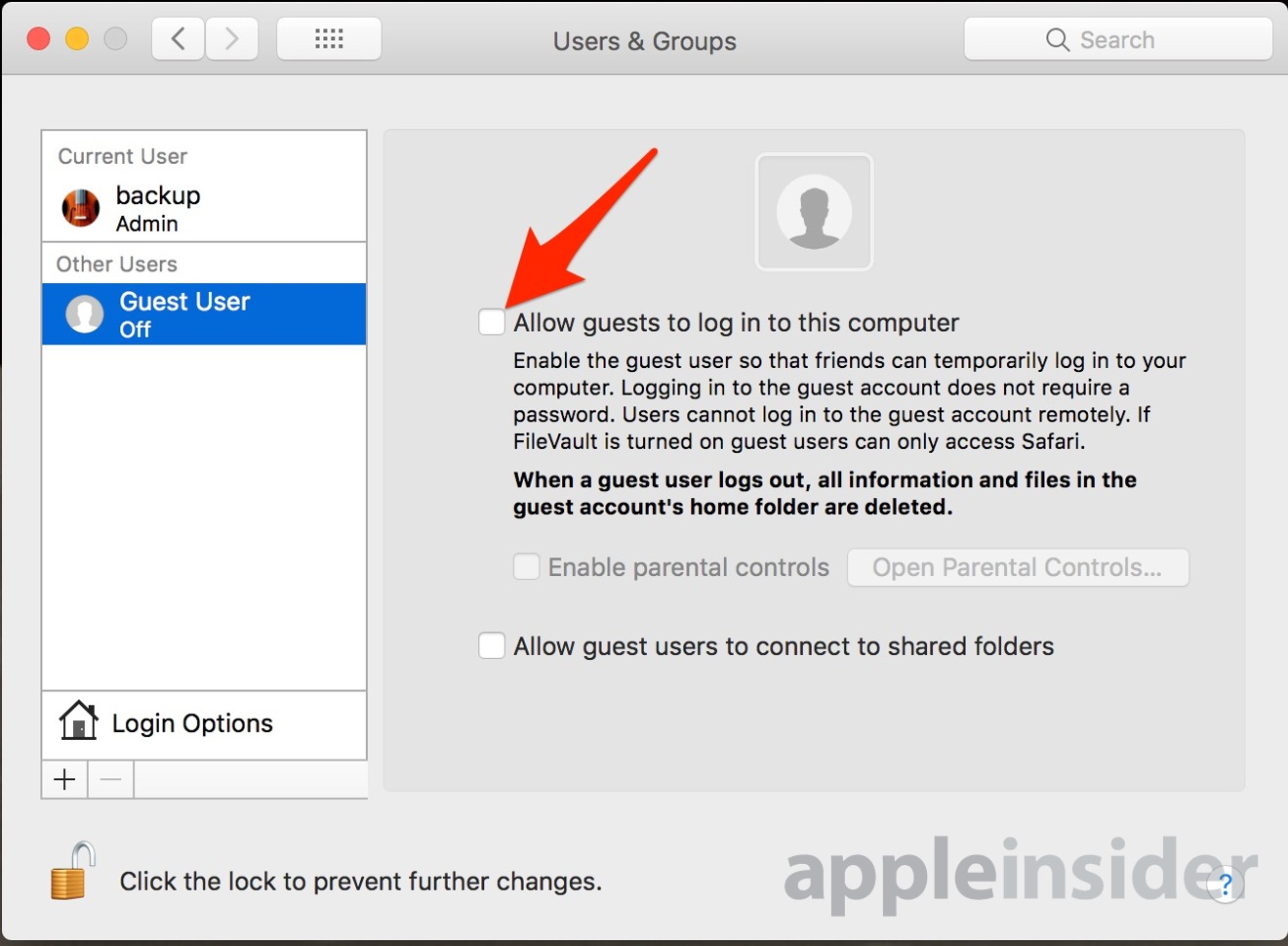
The ultimate protection against the exploit is to disable Guest access. This can be accomplished by opening up System Preferences, and turning off Allow guests to log in to this computer
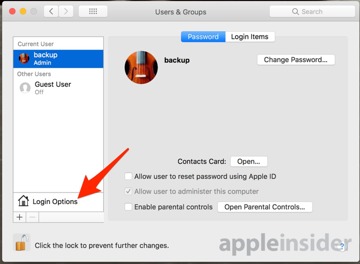
To disable the Root user, select System Preferences, then click Users & Groups.
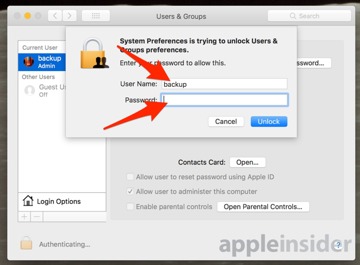
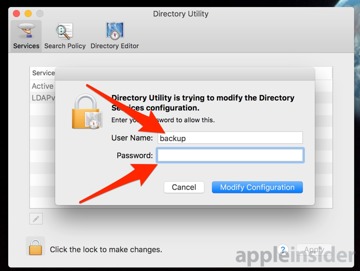
Click on the lock icon, and authenticate with an administrator's name and password. Click Login Options
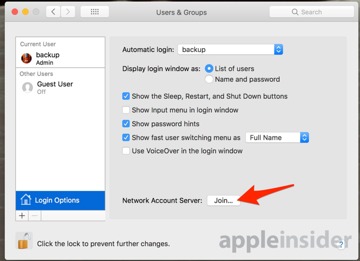
Click Join or Edit.
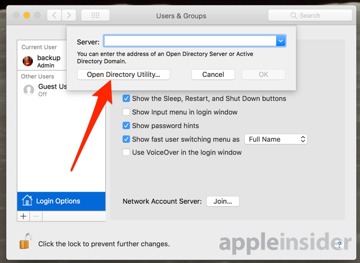
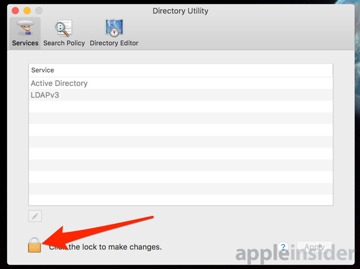
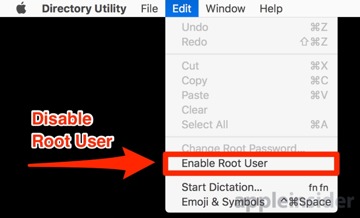
Click Open Directory Utility, and click on the lock icon to authenticate. Pull down the Edit menu, and select Disable Root User that will be in the same place as Enable Root User.
There is no way to generate the Root account from the login screen. After disabling the Root user, unless the procedure is followed again, the computer is secured.
Alternatively, from the Directory Utility, the Root account password can be changed. This will prevent the exploit from working again but can have unintended consequences, and the invocation of Root credential entry at unexpected times.
Update: Apple subsequently issued a statement to iMore
"We are working on a software update to address the issue. In the meantime, setting a root password prevents unauthorized access to your Mac. To enable the Root User and set a password, please follow the instructions here: https://support.apple.com/en-us/HT204012M. If a Root User is already enabled, to ensure a black password is not set, please follow the instructions from the "Change the root password" section.
 Malcolm Owen
Malcolm Owen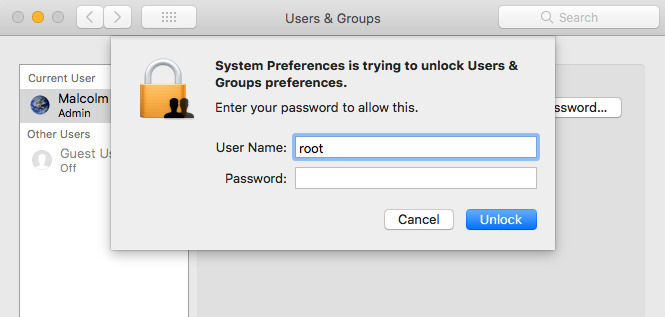







-m.jpg)






 Charles Martin
Charles Martin
 Christine McKee
Christine McKee
 Wesley Hilliard
Wesley Hilliard

 Andrew Orr
Andrew Orr
 William Gallagher
William Gallagher
 Sponsored Content
Sponsored Content








44 Comments
Your instructions are incorrect. Disabling the root user doesn't help.
https://news.ycombinator.com/item?id=15800676 says
"You're enabling the root user EVERY time you use this vulnerability. Even if you disable the root user in Directory Utility, logging in with root and no password will re-enable the root user."
You really need to set a password for "root" (using the same Directory Utility tool & nearby menu). After Apple releases a fix, remember to come back and disable the root user.
Fresh installation of High Sierra here. Root user was not enabled.
Scary. Yes, this bug is real as I just tried it and enabled root with my own password. Scary scary scary... Apple will move fast on this, no?
The original guy that found this should have quietly notified Apple through the official channels for reporting vulnerabilities. If Apple had not responded in a fair amount of time - then go public. He has just exposed a lot of people to having information stolen.