The second day of Pwn2Own 2018 saw Apple's Safari exploited twice, with one team completing its attempt within the competition's 30-minute, three-try guidelines, while another group demonstrated a bug in four attempts.
Results of the event were posted to Trend Micro's Zero Day Initiative website on Thursday, which noted a successful Safari exploit shown off by MWR Labs' Alex Plaskett, Georgi Geshev and Fabi Beterke.
The trio used two vulnerabilities — a heap buffer underflow in the browser and an uninitialized stack variable in macOS — to break Safari and escape the sandbox. The team earned $55,000 and 5 Master of Pwn points for their efforts.
A second attempt by Ret2 Systems, Inc.'s Markus Gaasedelen, Nick Burnett and Patrick Biernat failed to target Safari with a macOS kernel elevation of privilege vulnerability within the competition's prescribed limits. The team was able to get the exploit working on a fourth try.
Though it counts as a failure in terms of the hacking tournament's rules, the bug was still purchased and disclosed to Apple as per ZDI's normal procedure.
Richard Zhu, who unsuccessful targeted Safari on day one of Pwn2Own 2018, found success in a Mozilla Firefox exploit leveraging a Windows kernel EoP vulnerability, earning himself $50,000 and 5 Master of Pwn points. Zhu was this year's Master of Pwn, taking home a total of $120,000.
According to Trend Micro, a total of $267,000 were awarded at this year's event.
The inaugural Pwn2Own competition held in 2007 kicked off what has become an annual hacking contest encouraging researchers to discover and disclose zero-day vulnerabilities impacting a range of modern software and hardware. Hackers who demonstrate a successful exploit get to keep the hacked device, receive a cash prize and build points toward the coveted Master of Pwn title.
A number of Apple products have been targets over the contest's 11 years, from Safari to iPhone. At last year's Mobile Pwn2Own event, Zhu successfully escaped the sandbox in Safari on an iPhone 7 using two previously unknown bugs.
For vendors, the contest provides a relatively safe and affordable method of uncovering zero-day vulnerabilities that might have otherwise been discovered and leveraged by nefarious actors. Manufacturers and developers like Apple are given access to demonstrated exploits after they are confirmed by ZDI, a practice that often leads to critical software patches.
As noted in a previous report, ZDI partnered with Microsoft and sponsor VMWare for the 2018 contest to offer $2 million in cash and prizes to hackers targeting virtualization, web browsers, enterprise applications, servers and a special Windows Insider Preview Challenge. Five contestants were selected at random take part in the two-day competition, which covered two of the target categories.
 Mikey Campbell
Mikey Campbell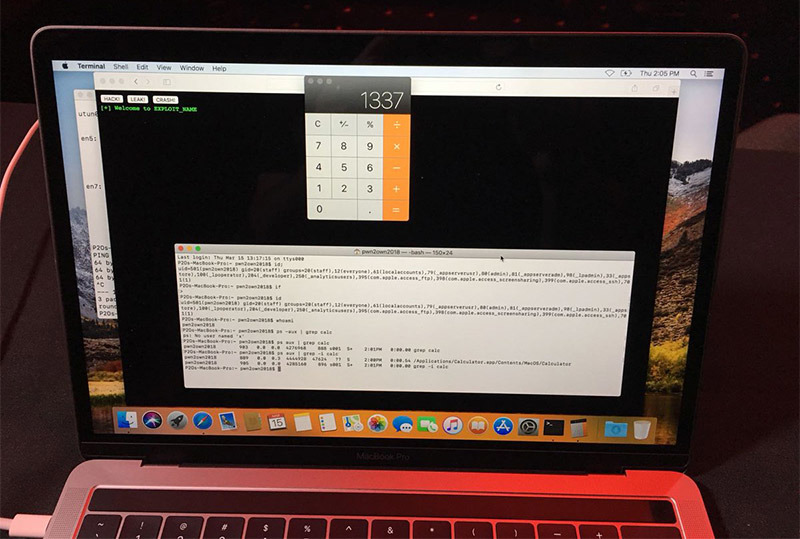







-m.jpg)






 Christine McKee
Christine McKee
 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Chip Loder
Chip Loder
 Brian Patterson
Brian Patterson

 Wesley Hilliard
Wesley Hilliard


-m.jpg)






6 Comments
This is a completely foreign land to me. If I could somehow live my life embodied through, say, 5 or 6 other human beings, I might pursue understanding in this field of endeavour (might). Interesting though...
This is a great way to find and fix exploits before they become problems. Safari/Mac is a popular target because the platform is so much more secure than any other consumer platform, and yet a grand total of three exploits were found by dedicated teams working all year. That’s fewer than Microsoft patches every week, and don’t even get me started on Android ...
These contests are a good thing for the product vendors are their customers. The only real losers in these contests are those entities who have already purchased or spent considerable time and money stockpiling these exploits for weaponization, e.g., NSA, CIA, FBI, PRNK, SVR/RF, etc. Hopefully, these exploits can now be partially or completely neutered. But also keep in mind that the other entities who profit from exploits are not restricted to the rules and guidelines of these contests, including which hackers are allowed to participate. The exploits identified during these contests are likely very low hanging fruit compared to what state funded hackers are able to obtain with no rules in place.