While the Pegasus software accessed the man's iPhone while he was in the company's offices, the attack was not wide, and the entrepreneur had volunteered his phone.
An entrepreneur, who works for an unnamed Israeli company, told Vice's Motherboard website this week that when he visited the offices of Spyware vendor NSO, he was asked if he wanted to receive a demo of the company's notorious Pegasus spying software.
When he volunteered a secondary iPhone and placed the phone on his desk, the NSO personnel compromised the phone within "5 to 7 minutes," placing the phone's screen on a large display in the room, accessing photos, emails, and even the microphone. And they got access without even getting the executive to click on a link.
It's an impressive feat, but the hacking of the phone was of only one target, one who had volunteered his phone and phone number. NSO, Vice said, had been known to do such things during demonstrations.
NSO Group, founded in 2010 in Israel, has often been controversial, with critics accusing it of helping governments crack down on political dissidents. In July a disgruntled NSO employee was indicted for stealing and attempting to sell the Pegasus code.
Apple has, multiple times in recent years, released patches in iOS and macOS to address vulnerabilities exploited by Pegasus.
NSO Group provided Vice with a statement in which it laid out its policies, including that signing up new clients requires permission and an export license from Israel's ministry of defense. Also, its product "cannot work" inside the United States.
"NSO's Business Ethics Committee, which includes outside experts from various disciplines, including law and foreign relations, reviews and approves each transaction and is authorized to reject agreements or cancel existing agreements where there is a case of improper use," the company said in that statement to the publication.
 Stephen Silver
Stephen Silver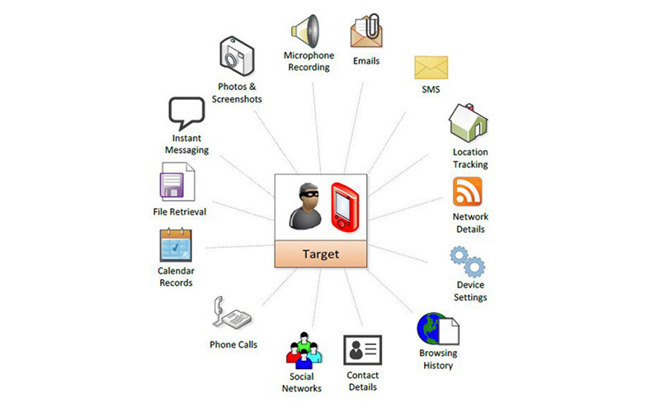








 Malcolm Owen
Malcolm Owen
 Amber Neely
Amber Neely
 Christine McKee
Christine McKee

 William Gallagher
William Gallagher
 Chip Loder
Chip Loder
 Brian Patterson
Brian Patterson

-m.jpg)






24 Comments
So? I’m not exactly shaking in my boots over this. Or should I just chuck my iPhone and get a Galaxy S9 to be more secure?
For starters, what version of iOS was installed, what model iPhone, was the device unlocked, and (presumably) what if anything was plugged into the Lightning port?
This article is very short on details.
"
Curious why they had to use his "other" iPhone and not his primary iPhone. Was it because of the phone number/carrier? Was it on a different version of iOS? Was it an older device?
"
Again, short on details. What does "put the phone on the desk" actually mean? Did he lay it down and they were able to get access via wireless (WiFi, BT or cellular), or did they connect the iPhone to a computer?While this is interesting, without these types of details it's hard to judge how serious this actually is.
As much as I’d love to be skeptical about their abilities, I believe it wholly. Apple has had exploits in their OS since day one. Jail breakers have been exploiting errors for years.
Imagine a company of nerds who who do this day in and day out? I think no prob. Between weak passwords, stack overflows, bizarre characters crashing iMessage, there have been tons of problems released publicly. Now imagine what hasn’t been made public.
I agree. Not enough details...
As a general best practice, people should reduce surface area vulnerability of their devices. For example, I have both WiFi and Bluetooth disabled. (Unless being used)
I’ve also disabled the login using biometrics. And, I have my devices patched (lastest OS). My password length/complexity is supposedly enough to keep it from being cracked in my lifetime.
Am I safe? No. But, I’m not a member of the “low hanging fruit” for attackers.