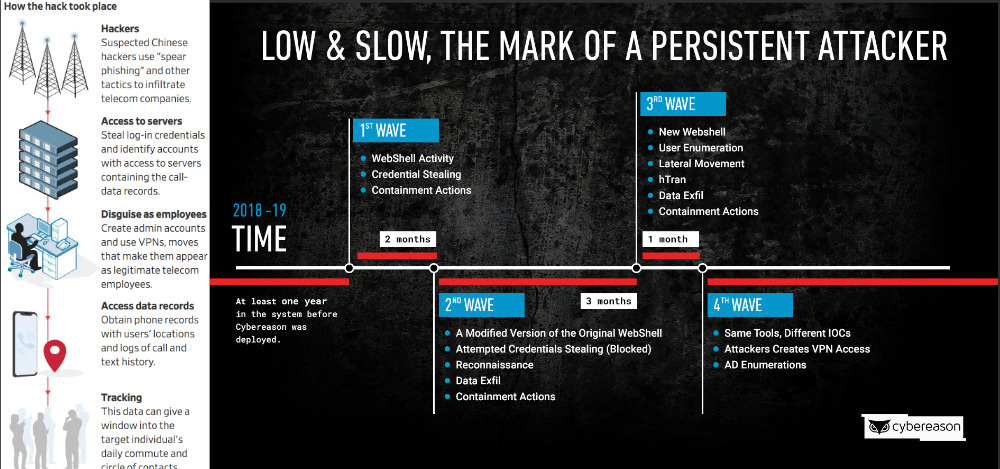
A Chinese government-backed group called APT 10 could be behind an unprecedented hack that granted high level access to at least ten global telecommunications carriers, permissions that were subsequently used to track specific spies, law enforcement, military personnel and dissidents linked to China.
Boston-based cybersecurity firm Cybereason Inc., claims to have identified an attack it calls Operation Soft Cell, which affected at least 10 carriers over the last few years, and is continuing now. As part of the ongoing intrusion, hackers reportedly attacked and infiltrated the networks of global phone carriers in order to track around 20 specific individuals of interest to China.
According to the Wall Street Journal, Cybereason's CEO Lior Div briefed over two dozen carriers about the issue this weekend.
"We never heard of this kind of mass-scale espionage ability to track any person across different countries," Div told the Journal. "All the indications are directed to China."
While Cybereason fell short of identifying the attackers, it said the bad actors left behind digital fingerprints pointing to APT 10, a group believed to be backed by the Chinese government. Last year, two alleged members of APT 10 were indicted by the U.S. Department of Justice for hacks targeting businesses and government agencies, the report said.
Cybereason's head of security research, Amit Serper, says the hackers did not listen in on calls, but instead harvested data about user location, movement and everyone they contacted. "They owned the entire network," he said.
Amongst other techniques, they reportedly gained access through spear phishing, the sending of emails purportedly from trust sources. They then stole log-in credentials, created admin accounts and through using VPNs, disguised their location to make it appear as if they were legitimate users within the telecoms firm.
Once able to enter the system, they accessed phone records which gave them call logs showing location, plus a complete list of who the target phoned or texted.
Cybereason would not reveal the carriers affected nor name the military, dissidents or other individuals whose details and movements had been tracked. The Wall Street Journal says that it has not been able to independently confirm the report and notes that China has always denied using cyberattacks.
However, senior manager of FireEye Intelligence, Ben Read, separately told the Journal that APT 10 has been less visibly active since the DOJ indictments but is likely to be continuing. "They're one of the most active China groups we track," he said.
 William Gallagher
William Gallagher




-xl-m.jpg)


-m.jpg)






 Amber Neely
Amber Neely

 Malcolm Owen
Malcolm Owen

 Mike Wuerthele
Mike Wuerthele

 Thomas Sibilly
Thomas Sibilly








13 Comments
Ironic seeing how the US is busy cyber-attacking Iran as we speak.
Venezuela's power grid crash is heavily tainted by some American scent too.
"If you don't buy from us, we will hack you!"
"It was the best of times. it was the worst of times, it was the age of wisdom, it was the age of foolishness..."
People are so quick to forget what Snowden told us about the utterly pervasive US surveillance of EVERYONE!
Only a fool would think China is behaving any differently to Western Governments but those stories don't make for great propaganda.