Those who own devices in Western Digital's My Book Live line woke up on Wednesday to find their devices have been wiped clean in an attack being attributed to malware.
Western Digital customers worldwide are discovering that years of data have been wiped clean without a trace and seemingly factory reset. Additionally, users cannot log into their devices with their user-set passwords or the manufacturer's default password.
The issue is currently known only to affect My Book Live devices, which saw their final firmware update in 2015. The devices were sold from 2010 until 2014, but have been discontinued since then.
While the issue was initially thought only to affect a few users, more users are taking to the forums to report that their devices have also been wiped. However, it is not currently known how many users are being affected.
It seems as though My Book Live devices received a remote command on June 23 to begin a factory restore on June 23, with the script set to run overnight.
BleepingComputer points out that WD's My Book line isn't connected to the internet the same way that QNAP devices are. This, in theory, prevents them from being exposed to QLocker ransomware attacks.
Instead, WD My Book Live devices are stored behind a firewall and are accessed via the My Book Live app or through internet browsers. Some users suspect that Western Digital's servers were hacked, allowing a bad actor to send out a remote factory reset command.
Western Digital told BleepingComputer that they are investigating the attacks but do not believe that its servers are at fault. Instead, they suggest an unpatched vulnerability is the cause of the problem.
Currently, this attack is suggested to only be destructive in nature. There have been no reports of any party asking for ransom.
It appears that Western Digital knew about the security flaw well before the recent exploitation. Western Digital forum user "thetick" reports finding reports of the vulnerability that allows for remote command execution as far back as 2019.
Years earlier, Western Digital told WisCase that they were no longer responsible for My Book Live devices. At the time, the company considered them "legacy devices" since they had been discontinued years prior.
To prevent further loss of data, Western Digital advises users to unplug My Book Live devices from the internet as soon as possible.
Keep up with everything Apple in the weekly AppleInsider Podcast — and get a fast news update from AppleInsider Daily. Just say, "Hey, Siri," to your HomePod mini and ask for these podcasts, and our latest HomeKit Insider episode too.
If you want an ad-free main AppleInsider Podcast experience, you can support the AppleInsider podcast by subscribing for $5 per month through Apple's Podcasts app, or via Patreon if you prefer any other podcast player.
 Amber Neely
Amber Neely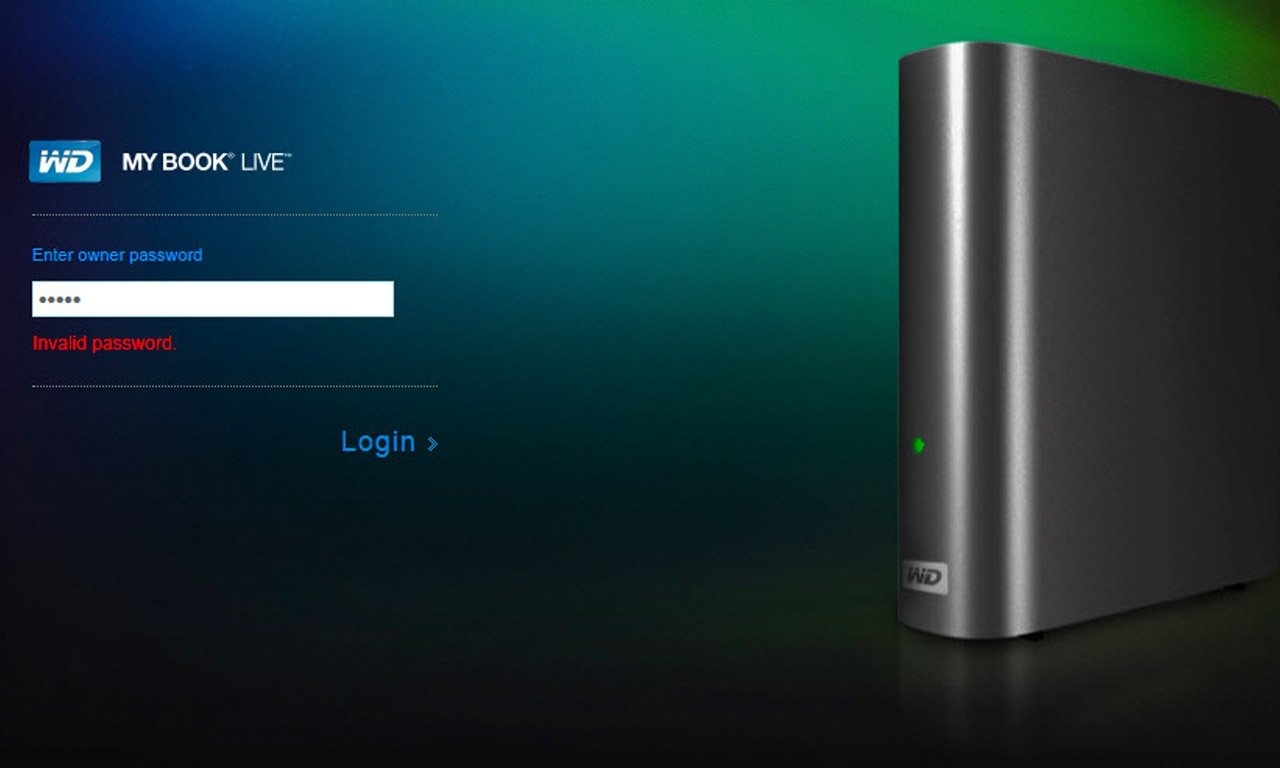

-m.jpg)






 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher
 Oliver Haslam
Oliver Haslam
 Thomas Sibilly
Thomas Sibilly
 Marko Zivkovic
Marko Zivkovic

 Wesley Hilliard
Wesley Hilliard


-m.jpg)






18 Comments
Kinda torn on this. On one hand if WD knew that's bad. But if WD knew but had declared them legacy well before and no longer supported them, well, that's the risk. Shouldn't be using such an archaic device for critical storage. Would we expect Apple to patch a vulnerability in Bondi Blue iMacs at this point? OTOH the newest of these would just be barely seven years old. That's not that far back. I don't know. 🤷
Ah, the discipline of "computer science"
F**king IT is a joke. I've never been more ashamed of my industry than here we are 40 years later and this shit is still happening. Except now being limited to damage that could be done through a floppy or maybe over modem through the wonders of the Internet all this haphazardly created and maintained shit can be touched by anyone from anywhere in the world.
Brilliant!
Most tech-oriented folks know to replace mechanical drives at least every 4 or 5 years, but most everyone is a not a techie. This is abhorrent...