Although malware-affected Macs are on the decline, the numbers are at a point much higher than forecasted by software maker Symantec, according to a Tuesday post on the company's blog.
The security firm guessed that the number of affected machines would have dropped precipitously by now given that Apple and third-party vendors released their respective Flashback-neutralizing programs last week. The Mac maker even rolled out a removal tool for those Mac users who don't have Java installed, and thus may be harboring a dormant version of the malware.
Statistics from Symantec's "sinkhole," or spoofed command and control server, show that Flashback has been removed from some 460,000 machines since Apr. 9, but the company expected less than 99,000 would be carrying the trojan by Tuesday.
Sinkholes are used by internet security and research entities to monitor and analyze the spread of malicious programs, though the standard practice sometimes brings unwarranted suspicion to smaller, less well-known firms. For example, Apple reportedly attempted to shut down the server hosting a sinkhole belonging to Flashback's discoverer Dr. Web, mistakenly thinking that it was a legitimate command and control server. Apple's move, however, can also be considered standard practice when dealing with fast-moving malware.
Forecast of Flashback removal. | Source: Symantec
There has been no speculation as to why the remaining Macs haven't already disposed of Flashback, as the self-installing program can be easily identified and deleted. It is possible that machine owners remain unaware of the program and haven't yet performed a software update that would eradicate it.
The trojan itself continues to propagate on upatched systems. Analysis into Flashback's structure reveals that it is coded to exceed the .com top level domain, and generates domain names from .in, .info, .kz and .net. Flashback creates one new string every day that is paired with a random TLD.
Once a user visits a site carrying Flashback, the program installs itself without the need for permission and proceeds to collect sensitive data like user iDs, passwords and web browsing histories which it then sends to an off-site repository.
Just as Flashback exploited the "Oracle Java SE Remote Java Runtime Environment Denial Of Service Vulnerability" to create its botnet, another threat has surfaced that uses the same hole as a means of distribution.
Called Backdoor.OSX.SabPub.a, the newly-discovered malware was created in March and is considered an "active attack" trojan as an operator manually checks and harvests data from an affected machine. SabPub has also been seen being distributed in malicious Word documents, installing itself by exploiting a known record parsing buffer overflow vulnerability.
 Mikey Campbell
Mikey Campbell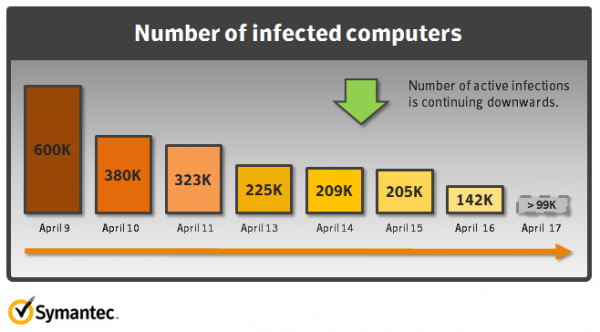

-m.jpg)






 William Gallagher
William Gallagher
 Thomas Sibilly
Thomas Sibilly
 Andrew O'Hara
Andrew O'Hara
 Amber Neely
Amber Neely
 Marko Zivkovic
Marko Zivkovic
 Malcolm Owen
Malcolm Owen
 William Gallagher and Mike Wuerthele
William Gallagher and Mike Wuerthele










38 Comments
80% drop in a week since it was announced is pretty damn impressive for dealing with a Trojan.
There has been no speculation as to why the remaining Macs haven't already disposed of Flashback, as the self-installing program can be easily identified and deleted. It is possible that machine owners remain unaware of the program and haven't yet performed a software update that would eradicate it.
Why doesn't it just download and work in the background? Malware removal tools have worked that way for a decade.
Apple needs to get its shit together and get out in front of this issue.
Why doesn't it just download and work in the background?
Becoming the demons isn't the right way to go.
Why doesn't it just download and work in the background? Malware removal tools have worked that way for a decade.
Apple needs to get its shit together and get out in front of this issue.
All you have to do is click install when Software Update notifies you of the update. Nothing more.
I call BS.
Look at the numbers in the chart. Now, note that Apple didn't release the removal tool until April 13.
One of two things happened:
1. The systems repaired themselves with no help from Apple
or
2. The numbers are entirely fabricated and meaningless.
Obviously, the latter is far more likely.