According to Apple, the Java security update removes the "most common variants" of the Flashback malware and offers further protection from future iterations by configuring the web plug-in to disable the automatic execution of Java applets.
From the release notes:
This update also configures the Java web plug-in to disable the automatic execution of Java applets. Users may re-enable automatic execution of Java applets using the Java Preferences application. If the Java web plug-in detects that no applets have been run for an extended period of time it will again disable Java applets.This update is recommended for all Mac users with Java installed.
The Flashback trojan created a botnet of more than 600,000 Macs around the world and tracked web browsing information, user IDs and passwords. By exploiting a Java security hole, the malicious software was able to install itself automatically on a user's computer after they visited an offending website. Flashback was first discovered last year and evolved into the self-installing version seen today.
The download, which supersedes recent Java patches, is available via Software Update and comes in at 66.8MB.
 AppleInsider Staff
AppleInsider Staff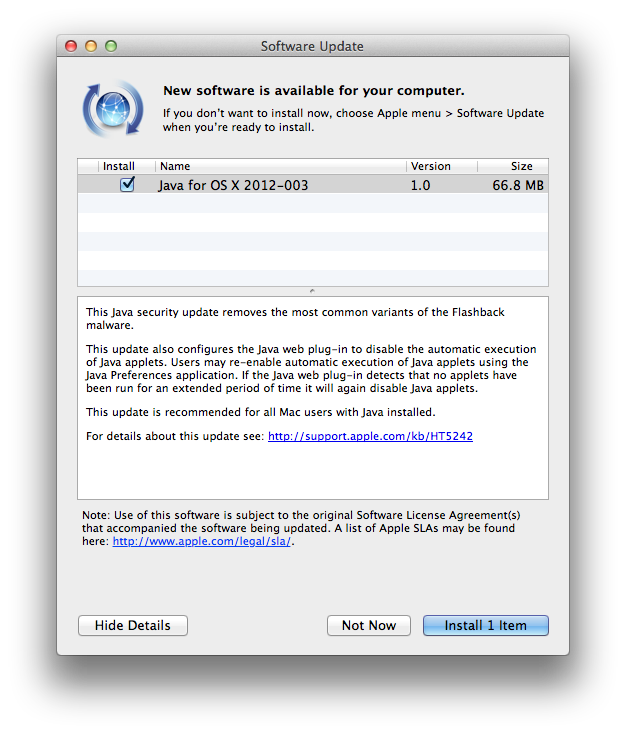








 Amber Neely
Amber Neely

 Wesley Hilliard
Wesley Hilliard
 Malcolm Owen
Malcolm Owen
 William Gallagher
William Gallagher











32 Comments
I was initially infected by this Flashback trojan on my Mac, and even the manual removal instructions did not get all of the trojan's files, which still tried to send info out over the Internet, but thanks to the Little Snitch app for finding these rogue infected files. I have installed this Java update with no problems. I hope I never see this trojan again on my Mac!
I was initially infected by this Flashback trojan on my Mac, and even the manual removal instructions did not get all of the trojan's files, which still tried to send info out over the Internet, but thanks to the Little Snitch app for finding these rogue infected files. I have installed this Java update with no problems. I hope I never see this trojan again on my Mac!
Interesting...it was my understanding that, according to F-secure, Flashback wouldn't install itself if you had Little Snitch (or a host of other programs). Am I reading this wrong?
http://www.f-secure.com/v-descs/troj...shback_i.shtml
Regardless, I ran the update and have done the discovery steps of the manual removal progress, and found nothing.
I know everyone wants to blame Java for this vulnerability and they should, however, allowing an application to auto install by visiting a website? Give me a break. That is something that neither the browser nor the OS should allow. Why they let a browser plugin write anything to disk other than a cookie or an html5 db, I do not know.
I was initially infected by this Flashback trojan on my Mac, and even the manual removal instructions did not get all of the trojan's files, which still tried to send info out over the Internet, but thanks to the Little Snitch app for finding these rogue infected files. I have installed this Java update with no problems. I hope I never see this trojan again on my Mac!
It will be interesting to see if Apple can find a way to prevent future threats without resorting to using an active or passive virus/trojan scanner. Locking down the execution of applications to signed apps is one step. Not sure how that will apply to Flash or Java applications started from the browser or malicious code somehow run within the browser.
I know everyone wants to blame Java for this vulnerability and they should, however, allowing an application to auto install by visiting a website? Give me a break. That is something that neither the browser nor the OS should allow. Why they let a browser plugin write anything to disk other than a cookie or an html5 db, I do not know.
Yeah, there should be multi-layer protection here. Java should restrict apps, the OS should sandbox Java, and Safari should not be executing Java apps/applets without specific user approval.