In what appears to be a response to allegations of installing "backdoor" services with the intent to harvest data from iOS devices, Apple on Tuesday posted to its website an explanation of three diagnostics capabilities built in to the mobile OS.
As listed in the support document, Apple goes over three iOS services, explaining how they work and why they exist, possibly in an attempt to address accusations that it installs backdoor services in cahoots with government agencies looking to surveil device owners.
The services detailed were mentioned by forensic scientist and iOS hacker Jonathan Zdziarski in a recent talk at the HOPE/X conference in New York. Zdziarski highlighted certain suspicious iOS background assets that appeared to serve no diagnostics purposes, but could potentially be exploited by law enforcement agencies or malicious hackers to steal sensitive personal data from iOS devices.
In the support document, Apple addresses three of these services — coincidentally listed in the same order as presented by Zdziarski in his slide deck — explaining how each works and its intended use as a diagnostics tool for developers or IT professionals.
From Apple's support document:
- com.apple.mobile.pcapd pcapd supports diagnostic packet capture from an iOS device to a trusted computer. This is useful for troubleshooting and diagnosing issues with apps on the device as well as enterprise VPN connections. You can find more information at developer.apple.com/library/ios/qa/qa1176.
- com.apple.mobile.file_relay file_relay supports limited copying of diagnostic data from a device. This service is separate from user-generated backups, does not have access to all data on the device, and respects iOS Data Protection. Apple engineering uses file_relay on internal devices to qualify customer configurations. AppleCare, with user consent, can also use this tool to gather relevant diagnostic data from users' devices.
- com.apple.mobile.house_arrest house_arrest is used by iTunes to transfer documents to and from an iOS device for apps that support this functionality. This is also used by Xcode to assist in the transfer of test data to a device while an app is in development.
In addition, Apple points readers in the direction of documents explaining data syncing and the "Trust this computer" iOS feature that protects against data extraction from an unknown Mac or PC.
While the document answers for three services questioned by Zdziarski, the hacker brought up many more, including those with the potential to seemingly bypass iOS backup encryption to serve up data from a user's address book, capture pictures from social media feeds, install spyware using available enterprise tools and more.
For its part, Apple responded to the allegations in a statement issued on Monday, saying diagnostic functions in iOS are designed to thwart any compromise of user privacy and security.
"As we have said before, Apple has never worked with any government agency from any country to create a backdoor in any of our products of services," Apple said.
The company added that users must first unlock their device and agree to trust a connected computer before transferring over diagnostics data, a point reiterated in today's support document.
 AppleInsider Staff
AppleInsider Staff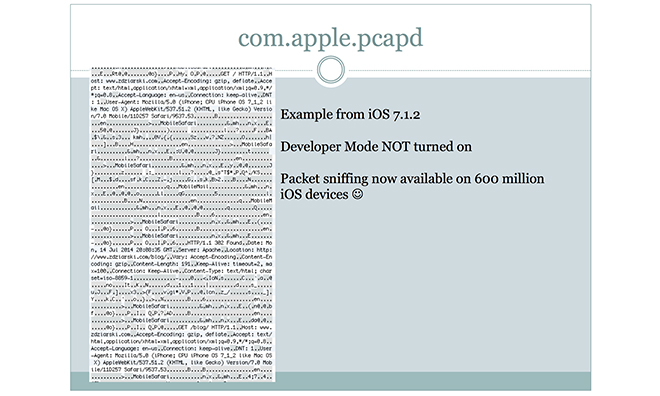







-m.jpg)





 Chip Loder
Chip Loder
 Wesley Hilliard
Wesley Hilliard
 Marko Zivkovic
Marko Zivkovic

 Christine McKee
Christine McKee
 Amber Neely
Amber Neely

 Malcolm Owen
Malcolm Owen






44 Comments
First it's denied. Then when it's realized that it has been put there on purpose it's a diagnostics tool? I guess I'll have to see what type of diagnostics this handles first. It's not currently being utilized. As noted by others, it's not an exploit. It's an open door intentionally programmed for something. Strangely it has access to all of your personal data. We'll just have to wait and see what that something is. Edit: added (Strangely it has access to all of your personal data) above.
[quote name="Silver Shadow" url="/t/181526/apple-details-ios-diagnostics-capabilities-in-answer-to-allegations-of-surreptitiously-installing-backdoor-assets#post_2567985"]First it's denied. Then when it's realized that it has been put there on purpose it's a diagnostics tool? I guess I'll have to see what type of diagnostics this handles first. It's not currently being utilized. As noted by others, it's not an exploit. It's an open door intentionally programmed for something. We'll just have to wait and see what that something is.[/quote] Apple didn't deny that the services exist; they denied that they were created to help law enforcement agencies crack iDevices. Good to see that Apple isn't letting the hit-whoring websites dictate the narrative completely. It's good practice for Apple's PR department which has been asleep at the wheel for years.
[quote name="Rayz" url="/t/181526/apple-details-ios-diagnostics-capabilities-in-answer-to-backdoor-services-allegations#post_2567996"] Apple didn't deny that the services exist; they denied that they were created to help law enforcement agencies crack iDevices. Good to see that Apple isn't letting the hit-whoring websites dictate the narrative completely. It's good practice for Apple's PR department which has been asleep at the wheel for years.[/quote] I'm glad to see their response also, although nothing in their press release or the subsequent links contained therein actually addressed why the deliberate holes were made. I'm hoping it's for a future product, but I'm optimistic! :) The problem is, if you JailBreak, that's instant access to every bit of personal data you have. That is of course if someone jailbreaks it. Those holes don't make it easier to JailBreak, but they do, all of your info is available. (Everything gets Jailbroken, it's just a matter of time).
The problem is, if you JailBreak, that's instant access to every bit of personal data you have. That is of course if someone jailbreaks it. Those holes don't make it easier to JailBreak, but they do, all of your info is available. (Everything gets Jailbroken, it's just a matter of time).
That is not entirely true. Several apps implement their own data encryption, which is not tied to the default root credentials. This data would still be encrypted after a jailbreak. Truly critical data (and I admit that this is a very subjective definition) does not belong into apps without such security features. Of course, most people will use the stock apps which do not have this additional protection for most stuff.
Nevertheless, I would argue that there is no need to blow this out of proportion. If somebody has physical access to a device and all the time in the world, most private, and even most business devices (laptops etc.) are even easier to read out (remove the drive and read it on another computer). Absolutely nobody makes a fuss about it. And if a government agency has the device and the authority to access it, they will, encryption or not.
[quote name="dreyfus2" url="/t/181526/apple-details-ios-diagnostics-capabilities-in-answer-to-backdoor-services-allegations#post_2568023"] That is not entirely true. Several apps implement their own data encryption, which is not tied to the default root credentials. This data would still be encrypted after a jailbreak. Truly critical data (and I admit that this is a very subjective definition) does not belong into apps without such security features. Of course, most people will use the stock apps which do not have this additional protection for most stuff. Nevertheless, I would argue that there is no need to blow this out of proportion. If somebody has physical access to a device and all the time in the world, most private, and even most business devices (laptops etc.) are even easier to read out (remove the drive and read it on another computer). Absolutely nobody makes a fuss about it. And if a government agency has the device and the authority to access it, they will, encryption or not. [/quote] Aren't you the person/persons that believes a .99 app could replace a $15k thermal imaging camera? Research what your posting about, because anyone with any real world experience can tell the difference. (Even opposed to researched material). With the two new built in holes, you do not need physical access. It allows access to all of your personal data. It could be because of the beta. No one knows why those holes are there right now. To me it looks like a tie in with a future product. Others have a different view. NO ONE KNOWS FOR SURE yet. If they're still there when it comes out of beta then it will certainly get a lot of attention. I'll help to make sure of it.