Apple's iOS 'dishing out a lot of data behind our backs,' security researcher charges
Noted forensic scientist and iOS hacker Jonathan Zdziarski has uncovered a number of undocumented "backdoor" services in Apple's mobile operating system that he argues could be exploited by law enforcement agencies, the NSA, or other malicious actors to bypass encryption and siphon sensitive personal data from iOS devices.
Zdziarski — an early member of iOS jailbreaking teams and author of the O'Reilly title Hacking and Securing iOS Applications — presented his discoveries as part of a talk at the annual HOPE/X conference, a long-running hacking and development conference in New York. The slides from that talk were first noted by ZDNet.
In the talk, Zdziarski touches on a number of services that run in the background on iOS but, he believes, do not appear to serve developers, Apple's engineering staff, or support personnel in any way. Others are designed for the benefit of enterprise administrators, but are crafted in such a way that they could be used for nefarious purposes.
"Much of this data simply should never come off the phone, even during a backup," Zdziarski wrote in one slide, referring to the information made available by those background services.
One service, com.apple.pcapd, captures HTTP data packets that flow to and from a user's device via libpcap. The service is active on every iOS device, according to Zdziarski, and could possibly be targeted via Wi-Fi for monitoring without the user's knowledge.
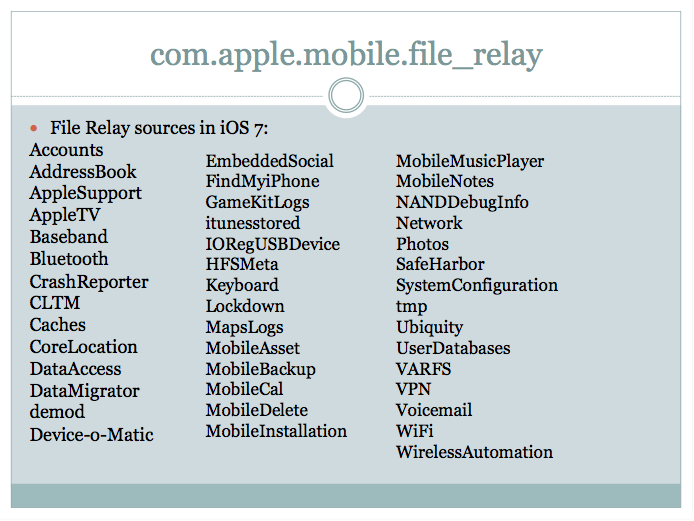
Zdziarski takes particular issue with the com.apple.mobile.file_relay service, which came around in iOS 2 but has been significantly expanded with successive release. This service completely bypasses iOS backup encryption, he says, exposing a "forensic trove of intelligence" including the user's address book, CoreLocation logs, the clipboard, calendars, notes, and voicemails.
In one particularly poignant example, Zdziarski says that an attacker could make use of this service to grab recent photos from a user's Twitter stream, their most recent timeline, their DM database, and authentication tokens that could be used "to spy on all future [Twitter] correspondence remotely."
Neither iTunes nor Xcode make use of these hidden services, Zdziarski notes, and the data is "in too raw a format" for Genius Bar use and cannot be restored to the device in any way.
Zdziarski also panned some of Apple's enterprise-friendly features, including mobile device management options that could allow an attacker to load custom spyware on a device by forging a security certificate. Zdziarski created a proof-of-concept spyware application for iOS in this way, he said, though Apple closed the loophole through which it collected data by denying applications the ability to create socket connections to the device itself.
A few of these services have already been tapped by manufacturers of commercial forensic devices, Zdziarski says, including companies like Elcomsoft, AccessData, and Cellebrite. Cellebrite products are widely used by U.S. law enforcement agencies to extract the contents of mobile devices seized from suspects.
Apple's iOS security is "otherwise great," Zdziarski wrote, noting that Apple has "worked hard to make iOS devices reasonably secure against typical attackers."
 Sam Oliver
Sam Oliver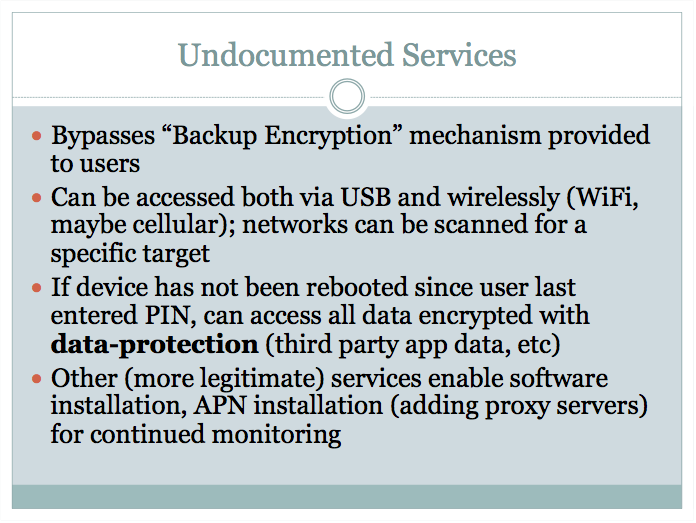












 Amber Neely
Amber Neely
 Thomas Sibilly
Thomas Sibilly
 AppleInsider Staff
AppleInsider Staff
 William Gallagher
William Gallagher
 Malcolm Owen
Malcolm Owen
 Christine McKee
Christine McKee









45 Comments
if you think Apple is bad you should look at Android cause Android is worse! I'd hate to be an Android owner, becuase the NSA pwns all of Android phones. And windoze Apple is Awesome!
This will be lost on the noise ... Apple's iOS security is "otherwise great," Zdziarski wrote, noting that Apple has "worked hard to make iOS devices reasonably secure against typical attackers."
Yet more reasons to never jailbreak. You never know what jailbreak apps really do.
I want to see this guy demonstrate this function.
I'm so sick of people talking about what "could be happening" or that it's "possible". Quit talking out of your ass to make a name for yourself and show us a working, functioning exploit where you've successfully pulled data off a device. Like he claims forensics agencies are doing.
Otherwise STFU.
if you think Apple is bad you should look at Android cause Android is worse!
I'd hate to be an Android owner, becuase the NSA pwns all of Android phones. And windoze
Apple is Awesome!
NSA is turning out just like in the sci-fi movies such as Minority Report, Fifth Sense, etc. In the future no one will have any real privacy.